1. Introduction to Security Architecture Frameworks
1.1 Overview of Security Architecture Frameworks
Security architecture frameworks serve as a strategic foundation for safeguarding digital assets, offering a distinct approach to ensuring robust protection. They help organizations design, implement, and manage secure IT systems that align with business goals. TOGAF, for example, is widely used to manage enterprise IT architecture. It defines the roles of technology, people, and processs to ensure a secure environment. SABSA focuses on linking security strategies to business objectives, making it a business-friendly framework. Meanwhile, OSA provides open-source solutions for organizations looking for flexible and cost-effective security frameworks.
Using these frameworks, organizations can identify vulnerabilities, address risks, and establish processes to mitigate potential attacks. These frameworks also provide guidance on adapting to new threats, ensuring long-term security.
1.2 Importance of Cybersecurity Frameworks
In today’s digital age, cyberattacks are becoming more sophisticated. Cybersecurity frameworks like NIST and ISO/IEC 27001 help businesses adopt industry best practices. These frameworks ensure compliance with regulations and provide a structured approach to securing sensitive information. For example, NIST CSF is commonly used by businesses to align their cybersecurity strategies with organizational goals.
Moreover, adhering to these frameworks can build customer trust. Customers are more likely to engage with businesses that prioritize their data’s security, making these frameworks a critical investment.
1.3 Key Objectives of Enterprise Security Architecture
The key goals of enterprise security architecture are data protection, compliance, and risk management. Businesses must secure their systems to prevent unauthorized access, ensure continuity during outages, and meet legal requirements. Furthermore, the architecture must adapt to emerging threats, making flexibility a crucial objective.
2. Cloud Security Architecture and Frameworks

2.1 Introduction to Cloud Security Architecture
Cloud computing offers many benefits, including flexibility and scalability, but it also presents unique security challenges. A cloud security architecture ensures the protection of applications, data, and services hosted in the cloud. It helps organizations secure their cloud infrastructure and reduce vulnerabilities from data breaches.
2.2 Cloud Service Models
Understanding the cloud service models is essential for managing security effectively:
- SaaS: Applications like Google Drive and Zoom provide ready-to-use services. Businesses must focus on user access and data protection.
- PaaS: Platforms like Microsoft Azure let developers build and deploy applications. Here, developers must secure their code and configurations.
- IaaS: Services like Amazon EC2 offer virtualized resources. Businesses must secure operating systems, network configurations, and stored data.
2.3 Shared Responsibility Model in Cloud Security
The shared responsibility model ensures that both cloud providers and users understand their roles in securing the environment. Providers secure the physical infrastructure and core services, while customers manage applications, access control, and data protection.
2.4 Encryption Strategies and Standards for Cloud Data
Encryption is vital for securing cloud data. Businesses use AES encryption, TLS protocols, and secure key management systems to protect data at rest and during transmission. Advanced tools like hardware security modules (HSMs) ensure that encryption keys are safely stored and managed.
3. Data Security Frameworks and Principles
3.1 Importance of Data Security Frameworks
A data security framework helps organizations establish consistent security practices. Frameworks like COBIT guide businesses in protecting data throughout its lifecycle. They provide recommendations for secure storage, transmission, and disposal of sensitive information.
3.2 Confidentiality, Integrity, and Availability (CIA Triad)
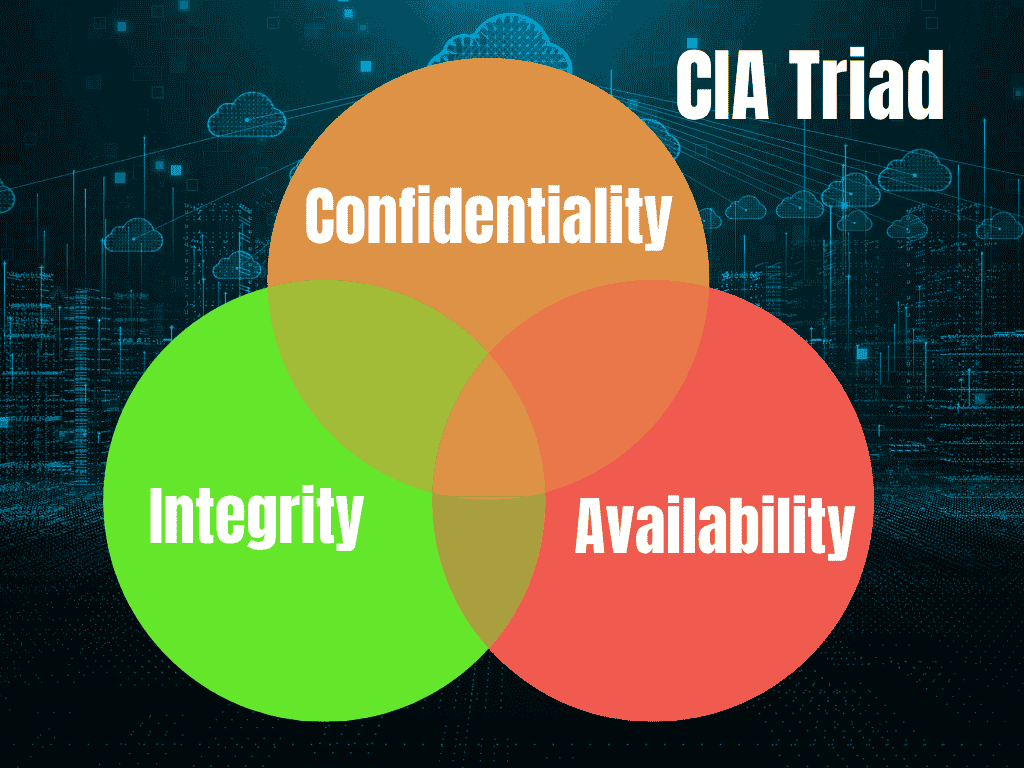
The CIA Triad forms the fundamental framework of data security principles. Businesses use it to build robust systems that are:
- Confidential: Data is protected from unauthorized access using encryption and IAM solutions.
- Integral: Systems use hashing algorithms to ensure data integrity.
- Available: Backup solutions and redundant systems ensure uninterrupted access.
3.3 Identity and Access Management (IAM) Fundamentals
IAM ensures that only authorized users can access systems and data. Methods such as multi-factor authentication (MFA) enhance security by introducing additional protective layers. For instance, a bank may require both a password and a one-time code sent to the user’s mobile phone before granting access.
IAM also enables businesses to enforce least privilege access, ensuring users only have permissions necessary for their roles.
4. IT Governance and Security Integration
4.1 IT Governance and Security Alignment
Integrating security into IT governance helps businesses align technology investments with security goals. Frameworks like COBIT 5 and ITIL provide detailed guidance on managing IT resources efficiently while reducing risks.

4.2 Compliance and Regulatory Requirements
Businesses must adhere to data protection laws like GDPR, HIPAA, and CCPA. Compliance guarantees that organizations safeguard customer data while adhering to legal requirements to avoid penalties. For example, GDPR requires businesses to notify users of data breaches within 72 hours.
4.3 Secure DevOps Practices (DevSecOps)
DevSecOps promotes embedding security checks into the software development lifecycle. This ensures that vulnerabilities are identified and resolved during development, reducing the risk of exploitation in production environments.
5. Threat Modeling and Risk Assessment in Security Architecture
5.1 Understanding Threat Modeling and Mitigation
Threat modeling identifies potential risks and outlines mitigation strategies. For instance, businesses using STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) can categorize threats and create targeted defenses.
5.2 Conducting Effective Risk Assessments
Risk assessments evaluate threats based on their impact and likelihood. Businesses often use heat maps to visualize risks and prioritize mitigation efforts. Regular assessments ensure that evolving threats are addressed promptly.
5.3 Incorporating Security Design Principles
Security design principles like separation of duties and fail-safe defaults ensure that systems are built with protection in mind. For instance, logging out inactive users prevents unauthorized access in shared workspaces.
6. Secure Software Development Lifecycle (SDLC)
6.1 Role of SDLC in Security Architecture
The Secure SDLC integrates security into every step of the software development lifecycle, which includes planning, design, development, testing, deployment, and maintenance. Traditionally, security was considered a separate process carried out after development. However, this approach often resulted in vulnerabilities being discovered late, causing delays and increased costs.
Modern secure SDLC emphasizes a proactive approach, embedding security checks early in the lifecycle. For example, during the planning phase, teams conduct threat modeling to anticipate potential risks. During development, they implement secure coding practices to avoid vulnerabilities like buffer overflows or SQL injections.
This approach not only improves the security of the final product but also enhances efficiency by addressing issues early.
6.2 Best Practices for Secure Development
To achieve secure software development, businesses can follow these practices:
- Security Training for Developers: Developers should be trained to recognize and avoid common security pitfalls.
- Automated Security Testing: Tools like static application security testing (SAST) and dynamic application security testing (DAST) help identify vulnerabilities in real-time.
- Use of Frameworks and Libraries: Employing security-focused frameworks such as Django or Spring ensures compliance with secure coding standards.
Moreover, implementing security gates at every phase of the SDLC ensures that code is reviewed and tested for vulnerabilities before moving to the next phase.
6.3 Zero Trust Architecture in Software Design
Zero Trust in software design involves the principle of least privilege access and continuous monitoring. This means users and applications are granted only the permissions they need, reducing the risk of exploitation.
An example is containerization, where each application component operates in its isolated environment.Even if a single component is breached, the rest of the system retains its security integrity.
7. Incident Response and Business Continuity
7.1 Incident Response Planning in Security Frameworks
Incident response frameworks like NIST SP 800-61 provide structured guidelines to handle cybersecurity incidents. An effective plan ensures:
- Early Detection: Using tools like Security Information and Event Management (SIEM) systems.
- Rapid Containment: Segregating compromised systems to halt the spread of damage.
- Swift Recovery: Restoring operations to minimize downtime.
Regular drills and tabletop exercises can test the readiness of incident response teams.

7.2 Disaster Recovery and Business Continuity Planning
Disaster recovery (DR) focuses on restoring critical IT systems after an incident, while business continuity planning (BCP) ensures uninterrupted operations. Key elements include:
- Data Backups: Regular backups ensure data can be restored even in ransomware attacks.
- Redundant Systems: Secondary systems take over if the primary systems fail.
- Communication Plans: Keeping all stakeholders informed throughout incident management.
A well-documented DR and BCP plan minimizes financial and reputational losses during a crisis.
7.3 Integration with Network Security Architecture
Modern businesses rely on network security tools like firewalls, intrusion detection systems (IDS), and VPNs to support incident response and recovery. For instance, during a distributed denial-of-service (DDoS) attack, these tools can block malicious traffic, ensuring legitimate users retain access.
8. Network Security Architecture and Cryptographic Controls
8.1 Foundations of Network Security Architecture
A network security architecture is a layered framework designed to protect digital networks from unauthorized access and attacks. It involves components like:
- Perimeter Security: Using firewalls and gateways to filter traffic entering the network.
- Internal Network Segmentation: Dividing networks into zones to limit access.
- Endpoint Security: Protecting devices like laptops and mobile phones.
For instance, a bank may use layered security to ensure that unauthorized users cannot access sensitive systems even if the perimeter is breached.
8.2 Cryptographic Security Controls and Applications
Cryptography ensures secure communication and data protection. Common cryptographic applications include:
- Public Key Infrastructure (PKI): Enables secure exchange of information online.
- Digital Certificates: Verifies the authenticity of websites or users.
- End-to-End Encryption: Ensures only the intended recipient can read messages.
Organizations must also prepare for future threats, such as quantum computing, by adopting quantum-resistant cryptography.
8.3 Intrusion Detection and Prevention Systems (IDPS)
An IDPS is crucial for detecting and mitigating cyber threats in real-time. Advanced systems use machine learning to identify abnormal patterns, enabling proactive responses to emerging threats.
For example, when an IDPS detects unusual login attempts from multiple locations, it can block access and alert administrators, preventing potential breaches.
9. Information Security Policy Frameworks
9.1 Developing Comprehensive Security Policies
A well-defined information security policy serves as the foundation of an organization’s security strategy. It should address:
- Acceptable Use Policies: Defining appropriate use of company resources.
- Access Control Policies: Specifying how users are granted and revoked access.
- Incident Response Policies: Providing steps to handle breaches effectively.
Policies should be tailored to the organization’s needs and aligned with industry standards like ISO/IEC 27001.
9.2 Framework Alignment with Enterprise Security Goals
Security policies must align with enterprise goals, ensuring they support business operations without compromising protection. For example, a retail company might focus on securing customer payment data to build trust and meet compliance with PCI DSS standards.
9.3 Ensuring Policy Effectiveness through IT Governance
Regular policy reviews, employee training, and governance frameworks like COBIT ensure that security policies remain effective. Automated tools can monitor compliance and flag violations, reducing the risk of human error.
10. Emerging Trends in Security Architecture

10.1 Zero Trust and Its Growing Relevance
Zero Trust architecture is no longer optional but a necessity in today’s cybersecurity landscape. Organizations adopting this model implement:
- Behavioral Analytics: Monitoring user actions to detect anomalies.
- Secure Access Service Edge (SASE): Combining networking and security into a single cloud-based platform.
Zero Trust is especially critical as remote work expands, exposing traditional perimeter defenses.
10.2 Advances in Cloud Security Practices
Cloud security continues to evolve with:
- AI-Powered Threat Detection: Leveraging machine learning to predict and neutralize threats before they occur.
- Serverless Security: Addressing vulnerabilities in serverless environments by automating security tasks.
- Container Security: Ensuring applications within containers are isolated and secure.
These innovations help businesses protect cloud environments from increasingly sophisticated attacks.
10.3 Future of Security Management Frameworks
The future of security frameworks lies in automation and adaptability. For example:
- AI-Driven Frameworks: Enabling continuous threat assessment and response.
- Blockchain Technology: Enhancing data integrity and transparency.
- Quantum-Resilient Algorithms: Preparing for threats from quantum computing.
These advancements will redefine security architecture, ensuring it remains robust against emerging challenges.
11 Differences Between Zero Trust Architecture and Traditional Security Architecture
| Definition | A security model that assumes no entity (internal or external) can be trusted by default and requires verification. | A security model based on protecting the network perimeter with trusted internal access. |
| Core Principle | “Never trust, always verify.” | “Trust but verify.” |
| Trust Model | Does not trust any entity by default, regardless of location (internal or external). | Assumes entities inside the network are trustworthy and focuses on external threats. |
| Access Control | Grants access based on continuous verification and least privilege. | Grants broad access once inside the network perimeter. |
| Security Perimeter | No clear perimeter; security is applied at every access point. | Relies on a strong network perimeter to block unauthorized external access. |
| Focus | User, device, and application verification with strict policies. | Network-level protection with limited attention to internal user behavior. |
| Technology Used | Multi-factor authentication (MFA), micro-segmentation, and continuous monitoring. | Firewalls, VPNs, and intrusion prevention systems (IPS). |
| Threat Assumption | Assumes threats can originate from anywhere, even inside the network. | Assumes threats are primarily external and focuses on protecting the perimeter. |
| Risk Mitigation | Minimizes impact by segmenting access and reducing attack surfaces. | Focuses on keeping attackers out but has limited measures for internal breaches. |
| Flexibility | Adaptable to remote work, cloud environments, and dynamic infrastructures. | Best suited for on-premises systems with fixed infrastructures. |
| User Authentication | Continuous authentication for every session or transaction. | One-time authentication, typically at login. |
| Scalability | Highly scalable for modern, distributed networks and cloud-based infrastructures. | Limited scalability, as security relies heavily on centralized control. |
| Adoption | Gaining popularity with remote work and cloud computing trends. | Widely used in legacy systems and traditional on-premises environments. |
| Outcome | Ensures robust security by reducing trust assumptions and enhancing visibility. | Provides strong external defense but may leave internal systems more vulnerable to insider threats. |
12 FAQs
1. What is the difference between Vulnerability Assessment and Risk Assessment?
Vulnerability assessment focuses on identifying weaknesses in a system, such as unpatched software or weak passwords, which could be exploited by attackers. Risk assessment, on the other hand, evaluates the potential impact and likelihood of threats, prioritizing risks based on their impact on an organization’s operations and data.
2. How does Zero Trust Architecture improve security compared to traditional methods?
Zero Trust Architecture enhances security by assuming no user or device can be trusted by default, regardless of location. It uses strict access controls, multi-factor authentication (MFA), and continuous verification to protect systems. In contrast, traditional security models rely on perimeter defense, which can be vulnerable to internal threats once the perimeter is breached.
3. Why is the CIA Triad important in cybersecurity?
The CIA Triad—Confidentiality, Integrity, and Availability—is the foundation of cybersecurity. Confidentiality ensures only authorized users can access data, integrity ensures the data is accurate and unaltered, and availability ensures that the data is accessible whenever needed. Together, these principles ensure robust data security.
4. What are some key benefits of using a security framework like NIST or ISO/IEC 27001?
Security frameworks like NIST and ISO/IEC 27001 provide structured guidelines for managing cybersecurity risks. They help organizations identify vulnerabilities, comply with regulations, and establish best practices for data protection. These frameworks also build customer trust and improve operational efficiency.
5. How does the Shared Responsibility Model work in cloud security?
In the Shared Responsibility Model, cloud providers and users share security responsibilities. Providers secure the infrastructure (e.g., servers, storage), while users are responsible for securing their data, managing access controls, and monitoring user activity. This collaboration ensures robust cloud security.
13 Conclusion
In today’s fast-evolving digital landscape, building a robust security architecture is not just a necessity but a strategic advantage for organizations. From adopting frameworks like TOGAF, SABSA, and NIST to implementing advanced models such as Zero Trust Architecture, businesses must prioritize proactive and adaptive security measures to protect their data and operations.
By understanding the differences between vulnerability assessments and risk assessments, aligning IT governance with security, and embracing cloud-specific strategies like the Shared Responsibility Model, organizations can strengthen their defenses against both internal and external threats. Furthermore, incorporating security into the SDLC and maintaining business continuity plans ensures resilience during crises.
Emerging trends such as AI-driven threat detection, quantum-resistant cryptography, and the growing relevance of Zero Trust Architecture emphasize the need for a future-ready approach. Whether addressing network security, data protection, or compliance, organizations must adopt a layered, holistic strategy to stay ahead of cyber threats
