1. Introduction
1.1 What is Vulnerability Assessment?
Vulnerability assessment is the process of identifying, evaluating, and prioritizing security weaknesses in a system, network, or application. The goal is to identify vulnerabilities that could be exploited by attackers to compromise the system. A vulnerability is essentially a flaw or weakness in the software, hardware, or configuration that can be targeted by malicious actors.
By conducting regular vulnerability assessments, organizations can identify these weaknesses and take proactive steps to fix them before they are exploited. This can be done through the use of automated vulnerability scanning tools, manual testing, and penetration testing. Vulnerability assessments are typically part of an organization’s broader risk management strategy and help prevent cyberattacks, data breaches, and other security incidents.
1.2 Why is Vulnerability Assessment Important in Cybersecurity?
In cybersecurity, vulnerabilities are the entry points for attackers. Cybercriminals are constantly looking for weaknesses in systems to exploit. By regularly conducting vulnerability assessments, businesses can reduce the risk of such attacks and strengthen their defenses. These assessments help uncover not only known vulnerabilities but also new ones that could pose a threat.
A vulnerability assessment offers a proactive way to safeguard sensitive information, secure IT infrastructure, and ensure compliance with security regulations. Moreover, organizations can minimize downtime, reduce the financial and reputational damage from a breach, and foster a culture of security awareness among employees. Without regular vulnerability assessments, organizations leave themselves exposed to significant risks that can lead to severe consequences.

1.3 How Does Risk Management Fit in?
Risk management plays a crucial role in vulnerability assessments because it helps organizations prioritize vulnerabilities based on their potential risk to the business. Not all vulnerabilities are equal in terms of the threat they pose. For example, a vulnerability in a public-facing server could be much more critical than a minor flaw in an internal employee portal.
By assessing the risk associated with each vulnerability—such as the likelihood of exploitation and the potential impact on the organization—risk management practices help businesses decide which vulnerabilities to address first. This ensures that resources are focused on addressing the most critical vulnerabilities, minimizing the likelihood of a successful attack.
1.4 Goals of Vulnerability Assessment
The goals of a vulnerability assessment are straightforward but crucial for maintaining a secure infrastructure. These goals include:
- Identifying vulnerabilities: The first goal is to identify vulnerabilities in your network, applications, and systems. This helps organizations understand what is vulnerable and susceptible to cyberattacks.
- Evaluating the risk: Once vulnerabilities are identified, they need to be assessed for their severity and potential risk to the organization. This step is important for prioritizing remediation efforts.
- Mitigating vulnerabilities: After vulnerabilities are prioritized, the next goal is to fix or mitigate them by applying patches, reconfiguring systems, or implementing new security measures.
- Maintaining compliance: Many industries are governed by strict regulatory standards that require regular vulnerability assessments to ensure systems are compliant with laws and regulations. This can include standards such as PCI-DSS, HIPAA, or GDPR.
2. Cybersecurity and Vulnerability Assessment
2.1 How Vulnerability Assessment Improves Cybersecurity
Vulnerability assessments are a fundamental part of a comprehensive cybersecurity strategy. They provide organizations with valuable insights into the security weaknesses present in their IT infrastructure. By identifying these weaknesses, organizations can develop more effective security measures and reduce the chances of cyberattacks.
A strong vulnerability assessment strategy helps create a proactive rather than reactive security posture. Cybersecurity teams can address vulnerabilities before cybercriminals have the chance to exploit them, reducing the likelihood of data breaches, ransomware attacks, and other threats. With the constant evolution of cyber threats, vulnerability assessments must be conducted regularly to ensure that security measures remain up to date.
2.2 Common Cybersecurity Threats
Cybersecurity threats are constantly evolving, but some of the most common threats that organizations face include:
- Malware: Malicious software, such as viruses, worms, and ransomware, designed to disrupt or damage systems.
- Phishing: A form of social engineering where attackers impersonate legitimate organizations to steal sensitive information, such as login credentials and personal data.
- Denial-of-Service (DoS): An attack designed to overwhelm a system or network with traffic, making it unavailable to legitimate users.
- Man-in-the-Middle (MitM): A type of attack where an attacker intercepts and potentially alters the communication between two parties without their knowledge.
Vulnerabilities in a system, such as unpatched software or weak encryption, can provide a way for these threats to be successfully executed. Identifying these vulnerabilities is critical in reducing the risk of cyber threats.

2.3 How Vulnerability Assessments Address Cybersecurity Threats
Vulnerability assessments play a key role in defending against cybersecurity threats by identifying and mitigating potential weaknesses. When organizations know where their vulnerabilities lie, they can implement appropriate security controls to reduce the likelihood of a breach.
For example, if an organization identifies outdated software or unpatched security flaws, it can apply updates and patches to fix these vulnerabilities. Similarly, by detecting weak or reused passwords, organizations can implement stronger password policies and multi-factor authentication (MFA). Vulnerability assessments help organizations stay one step ahead of potential cybercriminals by providing the insights needed to bolster defenses.
3. Risk Management in Vulnerability Assessment
3.1 What is Risk Management?
Risk management is the process of identifying, assessing, and controlling risks that might negatively affect an organization’s assets and operations. In cybersecurity, risk management involves evaluating threats, vulnerabilities, and the potential impact of security incidents, then implementing measures to reduce or mitigate those risks.
The goal of risk management is to protect critical assets and ensure business continuity by minimizing exposure to risks that could result in financial loss, reputational damage, or regulatory penalties.
3.2 How Risk Assessment Works
Risk assessment plays a crucial role in the risk management process. It entails assessing each identified vulnerability by considering two critical factors that set it apart.:
- Likelihood: How likely is it that a particular vulnerability will be exploited by a cybercriminal?
- Impact: If the vulnerability were to be exploited, what would be the consequences for the organization? This could include financial loss, data breaches, legal ramifications, and damage to the organization’s reputation.
The risk assessment process helps organizations understand the real-world risks posed by vulnerabilities, enabling them to prioritize their response efforts based on the severity and likelihood of exploitation.

3.3 Vulnerability Management and Risk Mitigation
Once vulnerabilities are assessed for risk, vulnerability management practices focus on addressing and mitigating them. This can involve a combination of technical solutions, such as applying software patches and updates, and procedural measures, such as implementing security training for employees or strengthening access controls.
Effective vulnerability management also includes continuous monitoring and periodic reassessments to ensure that new vulnerabilities are detected and addressed as they arise. By following a structured vulnerability management process, organizations can minimize their overall risk and ensure that vulnerabilities are handled promptly and effectively.
4. Vulnerability Analysis and Classification
4.1 What is Vulnerability Analysis?
Vulnerability analysis is the process of evaluating identified vulnerabilities to determine their severity, potential impact, and likelihood of exploitation. It involves scanning systems, networks, and applications for known vulnerabilities and analyzing them to prioritize the fixes that need to be applied.
By performing a vulnerability analysis, organizations can identify the most critical vulnerabilities that could potentially cause significant harm and focus on addressing them first. Vulnerability analysis helps improve the effectiveness of vulnerability management strategies by providing a detailed understanding of the vulnerabilities and how they affect the organization’s security posture.
4.2 Tools for Vulnerability Analysis
Several tools are available to help automate the process of vulnerability analysis. These tools scan systems for known vulnerabilities, compare them to a database of threats, and generate reports on potential risks. Some commonly used vulnerability analysis tools include:

- Nessus: A popular tool that helps identify vulnerabilities in systems, networks, and applications.It offers comprehensive reports along with suggestions for corrective actions.
- OpenVAS: An open-source vulnerability scanner that helps assess security issues in various systems.
- Qualys: A cloud-based solution for vulnerability scanning, asset management, and compliance monitoring.
These tools can help reduce the manual effort involved in vulnerability analysis, making it faster and more comprehensive.
4.3 Vulnerability Classification
After identifying vulnerabilities, they should be categorized according to their level of severity and potential impact.. Vulnerability classification helps organizations determine which vulnerabilities should be addressed immediately and which can be fixed later. Common classifications include:
- Critical vulnerabilities: These vulnerabilities pose the highest risk and must be fixed immediately.
- High vulnerabilities: These vulnerabilities should be addressed as soon as possible but are not as urgent as critical vulnerabilities.
- Medium and Low vulnerabilities: These should be fixed but may not pose an immediate risk to the organization’s security.
Effective vulnerability classification ensures that resources are focused on the most dangerous vulnerabilities first, reducing the risk of exploitation.
5. Security Scanning Tools in Vulnerability Assessment
5.1 Types of Security Scanning Tools
Security scanning tools are crucial for identifying vulnerabilities and misconfigurations in systems, applications, and networks. They help automate much of the vulnerability detection process, which can be tedious and time-consuming when done manually. These tools typically scan for known vulnerabilities listed in threat databases, such as CVEs (Common Vulnerabilities and Exposures), and generate reports on the security state of the target systems.
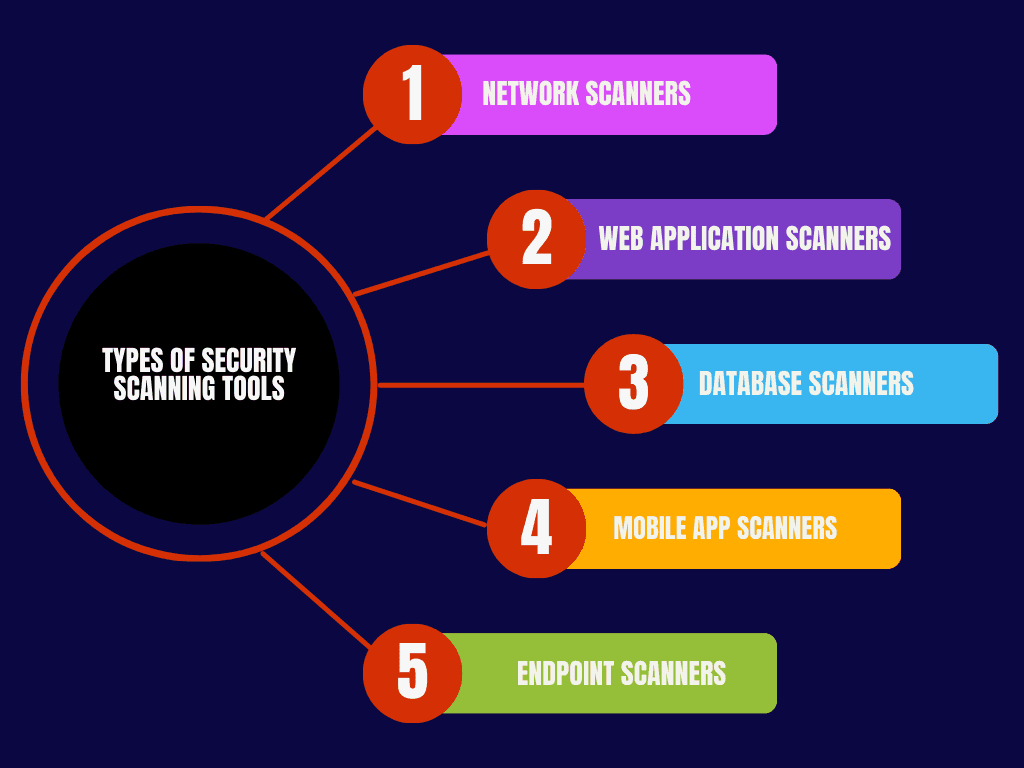
There are several types of security scanning tools that can be used during vulnerability assessments:
- Network Scanners: Tools that check network configurations and devices for security weaknesses. Examples include Nessus, OpenVAS, and Qualys.
- Web Application Scanners: These tools scan web applications for vulnerabilities such as SQL injection, cross-site scripting (XSS), and other web-specific issues. Popular tools include Acunetix and Burp Suite.
- Database Scanners: These focus on vulnerabilities within databases, such as insecure configurations, outdated versions, or unpatched database management systems. Tools like AppScan and Database Recon are often used.
- Mobile App Scanners: As mobile security threats increase, dedicated scanning tools like MobSF help identify vulnerabilities specific to mobile applications.
- Endpoint Scanners: These tools focus on identifying vulnerabilities on individual devices connected to the network, such as computers and smartphones.
Each tool type targets different areas of the system, and using a combination of them provides a more comprehensive view of vulnerabilities in an organization’s infrastructure.
5.2 Manual vs. Automated Scanning
Automated scanning tools are faster and more efficient at detecting a wide range of known vulnerabilities. These tools are valuable for regular scans and offer real-time analysis capabilities. However, automated scans often miss complex, non-obvious vulnerabilities that require a human touch to uncover.
Manual scanning or penetration testing allows cybersecurity experts to simulate real-world attacks, uncovering vulnerabilities that might not be easily detected by automated tools. Penetration testing often identifies logic flaws, complex misconfigurations, and advanced attack vectors, which automated tools might miss.
Therefore, a combination of both automated and manual scanning is recommended. Automated tools handle the repetitive tasks, while manual testing ensures that advanced or sophisticated vulnerabilities are identified and mitigated.
5.3 Best Practices for Using Scanning Tools
- Regular scans: Vulnerabilities evolve, and new threats emerge constantly. Regular scans ensure vulnerabilities are continuously identified.
- Comprehensive scanning: Ensure that all parts of the network, including servers, endpoints, applications, and cloud infrastructure, are regularly scanned.
- Prioritize findings: Automated tools often generate a large number of potential vulnerabilities. It’s important to filter and prioritize those based on severity, criticality, and the likelihood of exploitation.
- Integration with vulnerability management: Use security tools in combination with a vulnerability management system for continuous monitoring and tracking of remediation efforts.
5.4 Evaluating the Effectiveness of Security Tools in Assessment
Not all security scanning tools are created equal. It’s essential to evaluate the effectiveness of these tools before using them to scan systems. When selecting scanning tools, consider the following:
- Coverage: Does the tool support all the necessary platforms and technologies within your organization?
- Accuracy: How accurate are the results? False positives and false negatives can significantly impact the efficiency of the assessment.
- Ease of Use: Is the tool user-friendly? A tool that requires extensive training or complex configurations may not be ideal for regular use.
- Integration: Can the tool integrate with other security systems and workflows, such as security incident and event management (SIEM) systems or vulnerability management platforms?
6. Security Audits and Vulnerability Assessments
6.1 What is a Security Audit?
A security audit is a thorough examination of an organization’s security policies, procedures, and controls. It assesses the organization’s adherence to security best practices and identifies gaps in security management. While vulnerability assessments focus primarily on identifying technical weaknesses, security audits provide a broader view by reviewing overall security posture, including governance, compliance, and security policies.
Security audits can be internal or external. Internal audits are conducted by an organization’s own security team, while external audits are performed by third-party firms with expertise in security and compliance.
6.2 How Security Audits Complement Vulnerability Assessments
Security audits complement vulnerability assessments by offering an in-depth look at the broader security landscape. While vulnerability assessments focus on finding and patching vulnerabilities, security audits ensure that an organization’s security measures align with industry standards, regulatory requirements, and organizational policies.
For example, vulnerability assessments might reveal outdated software or insecure configurations, while a security audit might examine whether the organization is adhering to policies such as regular software patching or secure coding practices. Combining both audits and assessments helps organizations develop a more complete, proactive security strategy.

6.3 Conducting Vulnerability-Focused Security Audits
A vulnerability-focused security audit examines an organization’s vulnerability management practices, ensuring that vulnerabilities are being properly addressed. This includes reviewing policies related to patch management, incident response, and risk management. Auditors will also assess how the organization responds to vulnerabilities when identified and whether remediation efforts are timely and effective.
Key steps in a vulnerability-focused security audit include:
- Reviewing vulnerability assessment reports: Ensuring identified vulnerabilities are tracked and addressed.
- Assessing patch management processes: Ensuring that patches are being applied promptly.
- Examining compliance with internal security policies: Ensuring that the organization follows best practices for security management.
7. Penetration Testing vs. Vulnerability Assessment
7.1 What is Penetration Testing?
Penetration testing, also known as ethical hacking, is a simulated attack on a system to uncover vulnerabilities that could potentially be exploited by real-world attackers. Unlike vulnerability assessments, which focus on finding and listing vulnerabilities, penetration testing attempts to exploit them to determine the real-world impact of an attack.
Penetration testing often involves exploiting weaknesses to gain unauthorized access to sensitive systems, applications, or data. The results of penetration testing provide organizations with a clear understanding of the risks and potential damage that could occur if the vulnerabilities were exploited.
7.2 Differences Between Penetration Testing and Vulnerability Assessment
While both penetration testing and vulnerability assessments aim to identify weaknesses, there are key differences:
- Scope: Vulnerability assessments are broader and focus on identifying all potential vulnerabilities, whereas penetration testing is focused on exploiting identified weaknesses to demonstrate the severity of an attack.
- Approach: Vulnerability assessments are typically automated, using tools to scan for known vulnerabilities. Penetration testing, however, involves manual testing and simulating real-world attack scenarios.
- Outcome: A vulnerability assessment generates a report listing potential vulnerabilities, while a penetration test provides a demonstration of how an attacker might exploit those vulnerabilities.
7.3 Combining Penetration Testing with Vulnerability Assessment
For the best results, vulnerability assessments and penetration testing should be integrated into the security program. Vulnerability assessments can be used to identify a broad set of potential vulnerabilities, while penetration testing provides deeper insights into how these vulnerabilities can be exploited.
By combining both methods, organizations gain a comprehensive understanding of their security posture. Vulnerability assessments provide the technical details needed to secure the system, while penetration testing demonstrates how vulnerabilities can be leveraged in an actual attack.
8. Vulnerability Prioritization and Management
8.1 Why Vulnerability Prioritization Matters
Vulnerability prioritization is essential for managing resources effectively. Not all vulnerabilities carry the same level of risk, so it’s important to focus on fixing those that pose the greatest threat to the organization. Prioritization helps ensure that high-risk vulnerabilities are addressed first, reducing the likelihood of exploitation.
Without prioritization, organizations may waste time and resources on low-impact vulnerabilities while leaving critical risks unaddressed. A proper prioritization strategy allows organizations to focus their efforts where they matter most.
8.2 Methods for Prioritizing Vulnerabilities
Various approaches can be employed to prioritize vulnerabilities.:
- Risk-Based Analysis: Evaluating vulnerabilities based on their potential impact and likelihood of exploitation. This method focuses on the risk they pose to the business.
- CVSS Scoring: The Common Vulnerability Scoring System (CVSS) is a widely recognized standard used to evaluate the severity of vulnerabilities. score helps organizations prioritize vulnerabilities based on their potential impact.
- Threat Intelligence: Integrating threat intelligence feeds into vulnerability management helps organizations understand how active the threat landscape is and prioritize vulnerabilities that are being actively exploited.
8.3 Vulnerability Management Strategies
An effective vulnerability management strategy includes:
- Regular vulnerability scanning: Performing regular scans ensures that new vulnerabilities are quickly identified and addressed.
- Patch management involves quickly implementing patches and fixes to address vulnerabilities.
- Continuous monitoring: Vulnerabilities and threats evolve over time, so continuous monitoring helps organizations stay ahead of new risks.
A strong vulnerability management strategy should be a continuous process, integrated into the organization’s overall security strategy, to ensure long-term protection.
9. Addressing Security Threats Through Vulnerability Assessment
9.1 Identifying Security Threats During Vulnerability Assessment
Vulnerability assessments play a critical role in identifying potential security threats. The main goal is to identify system vulnerabilities that could be targeted by attackers.. These weaknesses might include open ports, outdated software, misconfigured systems, weak passwords, and unpatched vulnerabilities. Once discovered, these vulnerabilities provide attackers with potential points of entry into a system.
For instance, open ports can expose a network to attacks such as Denial of Service (DoS) or Distributed Denial of Service (DDoS), while outdated software may contain known exploits that attackers can easily use to gain unauthorized access. A vulnerability assessment helps organizations locate these weak points before cybercriminals can use them for malicious purposes.
Additionally, vulnerability assessments use security scanning tools and manual penetration testing to simulate potential attacks. This allows the organization to understand how an attacker might exploit weaknesses in the system, offering valuable insights into the overall security posture.
9.2 Correlation Between Threats and Vulnerabilities
Vulnerabilities act as the entry points for threats. Without vulnerabilities in place, it would be nearly impossible for attackers to execute an attack. A detailed vulnerability assessment helps establish a direct connection between existing security threats and the specific weaknesses they target.
For example, a phishing attack often targets weak user authentication protocols (like weak passwords), while an attacker might exploit an SQL injection vulnerability in a web application to gain unauthorized access. A successful vulnerability assessment uncovers these weaknesses, helping organizations understand how certain vulnerabilities expose them to specific types of threats.
By connecting threats to vulnerabilities, organizations can implement targeted remediation strategies to block the attack vectors that are most likely to lead to exploitation. This correlation helps to develop a layered security approach that addresses both vulnerabilities and the threats they attract.
9.3 Mitigating Security Threats Through Effective Assessment
Once vulnerabilities are identified and prioritized, the next step is to mitigate the security threats associated with them. Remediation efforts may involve patching software, closing open ports, implementing strong password policies, or applying security controls like firewalls and intrusion detection systems.
By addressing vulnerabilities effectively, organizations can reduce the risk of exploitations and minimize the impact of potential attacks. The idea is to neutralize vulnerabilities before attackers can take advantage of them. A solid vulnerability management plan includes regular updates, patches, and proactive monitoring to ensure that threats are identified and neutralized before exploitation occurs.
10. Best Practices for Conducting Vulnerability Assessments
10.1 Comprehensive Approach to Vulnerability Assessments
A comprehensive vulnerability assessment covers all areas of an organization’s infrastructure, including network infrastructure, applications, endpoints, and databases. This approach ensures that all possible attack surfaces are covered, and no part of the organization is left exposed to potential vulnerabilities.
Network scans can identify weaknesses in configurations, while application assessments focus on identifying security flaws like SQL injection or cross-site scripting (XSS). Endpoint assessments ensure that all devices connected to the network (e.g., desktops, smartphones, IoT devices) are secure and free from vulnerabilities. Combining all these areas provides a holistic view of an organization’s cybersecurity posture and ensures that no potential weakness is overlooked.

10.2 Continuous Monitoring and Vulnerability Analysis
Cybersecurity is a continuous process. Threats change quickly, and new vulnerabilities are continually being discovered. Therefore, continuous monitoring is crucial for identifying emerging threats and vulnerabilities as they arise. Automated scanning tools and real-time monitoring systems allow organizations to detect vulnerabilities on the fly and respond to them in real time.
By continuously analyzing vulnerabilities, organizations can stay ahead of attackers and ensure that newly discovered vulnerabilities are promptly addressed. This proactive approach reduces the risk of undetected weaknesses being exploited over time.
10.3 Common Pitfalls in Security Audits and Vulnerability Assessments
While vulnerability assessments are essential for cybersecurity, several common pitfalls can undermine their effectiveness:
- Failure to prioritize critical vulnerabilities: Not all vulnerabilities are equally dangerous. Failing to prioritize high-risk vulnerabilities can lead to devastating breaches.
- Over-reliance on automated tools: While automated tools are useful, they are not foolproof. Automated scans may miss complex vulnerabilities or new attack vectors. Manual testing and penetration testing should complement automated scans.
- Not conducting regular assessments: Vulnerability assessments should be conducted on a regular basis. A one-time assessment is insufficient, as vulnerabilities change over time with new software updates, configurations, and threats.
Avoiding these pitfalls ensures a more effective and comprehensive vulnerability management strategy.
11. Case Studies and Real-World Applications
11.1 Case Studies of Successful Vulnerability Assessments
Real-world case studies provide concrete examples of how vulnerability assessments have helped organizations identify and mitigate critical vulnerabilities before they resulted in major security incidents. For example, a vulnerability assessment might identify an unpatched vulnerability in an outdated web server that could be exploited by attackers. Once this vulnerability is patched, the organization significantly reduces its risk of a data breach.
Another case study might involve a large financial institution that conducted vulnerability assessments regularly, discovering a misconfigured database that exposed sensitive customer information. By fixing this configuration, the organization prevented a major data leak, avoiding financial losses and reputational damage.

11.2 Lessons Learned from Past Security Threats and Vulnerability Management
Learning from past breaches is crucial for improving future vulnerability management strategies. By analyzing past attacks and understanding the vulnerabilities that led to them, organizations can refine their vulnerability assessment and remediation processes.
For instance, after a ransomware attack exploiting an unpatched vulnerability, the organization may implement a policy for faster patching, enhance endpoint security, and establish stronger network segmentation. These lessons help create a more resilient cybersecurity framework.
11.3 Analyzing the Effectiveness of Vulnerability Assessment Methodologies
After conducting vulnerability assessments, it is important to evaluate their effectiveness. Post-assessment reviews ensure that identified vulnerabilities were adequately addressed, and any missed vulnerabilities are noted for future assessments.
An analysis of past assessments can help identify any gaps in the methodology or the tools used, ensuring that the assessment process evolves and adapts to meet the latest security threats. Continuous improvement in the vulnerability assessment process is key to maintaining strong cybersecurity defenses.
12. The Future of Vulnerability Assessment Methodology
12.1 Emerging Trends in Vulnerability Assessment
The future of vulnerability assessments will likely see more automation, AI integration, and the use of advanced threat intelligence. As cyber threats become more sophisticated, the tools and methodologies used to assess vulnerabilities will need to evolve.
AI and machine learning will play a larger role in identifying complex vulnerabilities, predicting potential exploits, and automating remediation processes. These advancements will significantly enhance the efficiency and accuracy of vulnerability assessments.
12.2 Trends in Risk Management and Vulnerability Scanning Tools
The development of new scanning tools and risk management frameworks will continue to evolve, providing more comprehensive, accurate, and real-time vulnerability assessments. Technologies like cloud security tools, container scanning, and IoT security will be increasingly important as organizations embrace new technologies and move more operations to the cloud.
These tools will enable organizations to scan complex, hybrid infrastructures more easily, ensuring vulnerabilities are identified across both on-premise and cloud-based environments.
12.3 Innovations in Penetration Testing and Vulnerability Prioritization
The integration of AI and machine learning in penetration testing and vulnerability prioritization will help organizations handle vulnerabilities more effectively. AI can help penetration testers identify patterns and anomalies that would be difficult for human testers to spot.
Moreover, AI-driven vulnerability prioritization will enable organizations to assess the risk associated with each vulnerability more accurately, helping them prioritize remediation efforts with even greater precision.
13 Difference between Vulnerability Assessment and Risk Assessment
| Definition | The process of identifying, evaluating, and classifying vulnerabilities in a system, network, or application. | The process of identifying, evaluating, and prioritizing risks to an organization’s assets, based on the likelihood and impact of potential threats. |
| Purpose | To find weaknesses (vulnerabilities) that could be exploited by attackers, helping organizations secure their systems. | To assess potential risks and the impact of various threats on the organization’s operations, data, and reputation, and to prioritize them. |
| Focus | Focuses on identifying weaknesses in systems, applications, or network configurations. | Focuses on evaluating potential risks, including those posed by vulnerabilities, threats, and the impact they could have on the business. |
| Scope | Limited to identifying specific vulnerabilities, such as outdated software, configuration issues, or weak passwords. | Broader scope, considering internal and external risks (e.g., cyber threats, natural disasters, human error, financial risks). |
| Methodology | Primarily involves scanning tools, manual testing, and pen testing to detect vulnerabilities. | Involves qualitative and quantitative analysis, such as risk matrices, CVSS scoring, and expert assessments. |
| Tools Used | Nessus, OpenVAS, Qualys, Burp Suite, and other vulnerability scanning tools. | Risk matrices, FMEA (Failure Mode Effects Analysis), ISO 27005, and Bowtie analysis. |
| Outcome | The identification of specific vulnerabilities with recommendations for patches or mitigations. | A prioritized list of risks, with strategies for mitigation or acceptance based on their likelihood and impact. |
| Frequency | Regular assessments are performed to stay up-to-date with emerging vulnerabilities (e.g., monthly, quarterly). | Performed periodically or based on significant changes in business environment, strategy, or technology. |
| Who Performs It | Typically performed by security teams, penetration testers, or security auditors. | Performed by risk managers, business analysts, and security officers, involving multiple departments (IT, legal, operations). |
| Example | Finding an outdated version of a software package vulnerable to known exploits. | Assessing the likelihood of a data breach occurring due to vulnerabilities in a web application, and the financial impact if it happens. |
| Output | Reports identifying vulnerabilities, severity levels, and recommended actions to mitigate or eliminate them. | Risk register or risk management plan, including risk ranking and mitigation strategies for identified risks. |
14 FAQs
1. What is a Vulnerability Assessment and why is it important?
A Vulnerability Assessment involves identifying, categorizing, and prioritizing vulnerabilities within systems, networks, and applications. The goal is to find weaknesses (e.g., outdated software, open ports, weak configurations) that could be exploited by attackers. It’s important because finding vulnerabilities early allows organizations to fix them before attackers can exploit them, reducing the risk of cyberattacks and data breaches. By regularly conducting vulnerability assessments, organizations can stay proactive, maintain stronger defenses, and ensure the integrity and availability of their systems.
2. How often should a Vulnerability Assessment be conducted?
Vulnerability assessments should be conducted on a regular basis, typically every 3 to 6 months, or whenever there are significant changes in the environment (e.g., system upgrades, new applications, changes in network configuration). In fast-paced industries like technology, assessments may need to be monthly. Additionally, it’s important to conduct assessments after any major update or patching of systems to ensure no new vulnerabilities are introduced. Continuous monitoring using automated tools is also recommended for detecting new threats in real-time.
3. What tools are used in Vulnerability Assessments?
There are a variety of tools available for vulnerability assessments, which help automate the process of scanning systems for weaknesses. Common tools include:
- Nessus: A widely used tool that provides comprehensive scans for a variety of vulnerabilities, offering detailed reports and remediation suggestions.
- Qualys: A cloud-based tool that scans for vulnerabilities across a network and provides continuous monitoring.
- OpenVAS: An open-source tool offering vulnerability scanning for different types of networks and applications.
- Burp Suite: Focuses on web application security, identifying vulnerabilities like SQL injection and cross-site scripting (XSS).
- Acunetix: Primarily used for web applications, this tool finds vulnerabilities such as SQL injection, XSS, and misconfigurations in web apps.
These tools help organizations identify and fix vulnerabilities before they can be exploited.
4. How does Vulnerability Assessment help mitigate cyberattacks?
While vulnerability assessments alone cannot stop cyberattacks, they are a crucial part of the cybersecurity defense process. By regularly identifying and addressing vulnerabilities, organizations can significantly reduce the attack surface available to cybercriminals. For example, identifying and patching a known vulnerability in a software program prevents attackers from using it as an entry point for malware or data theft. Furthermore, vulnerability assessments also provide valuable insights into network configurations, allowing companies to apply stronger security measures (e.g., firewalls, intrusion detection systems) to block malicious activity.
5. Why is Risk Assessment critical in Vulnerability Management?
Risk Assessment is essential because it helps organizations understand the impact of vulnerabilities on business operations. Not all vulnerabilities present the same level of risk. For example, a critical vulnerability in a public-facing server poses a higher risk than a minor vulnerability in an internal system. Risk assessments help organizations prioritize remediation efforts by considering both the likelihood of a vulnerability being exploited and the severity of the impact. By combining vulnerability assessments with risk assessment, organizations can apply more strategic and effective security measures that protect their most valuable assets and minimize damage in case of an attack.
6. How do Vulnerability and Risk Assessments work together in cybersecurity?
Vulnerability and risk assessments work hand in hand to create a robust cybersecurity strategy. While vulnerability assessments focus on identifying specific weaknesses in systems, risk assessments help determine the likelihood and impact of those vulnerabilities being exploited. After vulnerabilities are identified, risk assessments help prioritize them based on their potential to cause harm. For example, if a vulnerability is identified in a high-traffic web server, a risk assessment will analyze the impact of exploiting that vulnerability on the entire network and business, leading to more focused remediation efforts.
15 Conclusion
In summary, Vulnerability Assessments identify weaknesses in systems, while Risk Assessments evaluate the potential impact of those vulnerabilities. Both are crucial components of a robust cybersecurity strategy. Vulnerability assessments help uncover and fix weaknesses, while risk assessments prioritize those vulnerabilities based on their potential threat to the organization. Together, they enable organizations to proactively manage security, reduce risks, and protect critical assets.
