1 Understanding PIAM
Physical Identity and Access Management, or PIAM, is a security approach that combines traditional physical access control with modern identity management tools to secure locations like buildings, rooms, and restricted areas. PIAM systems go beyond basic access control (like swiping an ID card to enter) by linking each access event to a verified identity, thus adding a layer of security that’s essential in today’s interconnected environments.
A PIAM system might manage not only the physical entry of a person but also log related digital activity if needed. For instance, when someone enters a high-security area, their entry and movement may be logged to ensure compliance with security policies. This integration with digital identity management makes PIAM an indispensable tool in maintaining security within many organizations.
2 Why PIAM Matters in Today’s Security Landscape
Modern security challenges demand a more comprehensive approach, as threats have become increasingly sophisticated. Whether a threat is physical (unauthorized access to sensitive areas) or digital (data breaches), PIAM can help organizations respond more effectively. By unifying physical and digital security, PIAM creates a streamlined, efficient approach to manage and monitor access. For example, PIAM ensures only verified employees have access to sensitive areas like server rooms, adding an extra layer of defense.
PIAM systems also help organizations meet regulatory requirements. For example, in sectors like finance and healthcare, companies are often required to keep detailed records of who accessed secure areas and when. PIAM can provide this level of detail, supporting regulatory compliance and protecting against potential security incidents. Additionally, in emergency situations, PIAM systems can provide real-time information on who is in a specific area, aiding quick response efforts and ensuring the safety of all personnel.
3 Key Applications of PIAM
PIAM’s ability to manage physical and identity-based access makes it adaptable across various industries. Here are some notable applications:
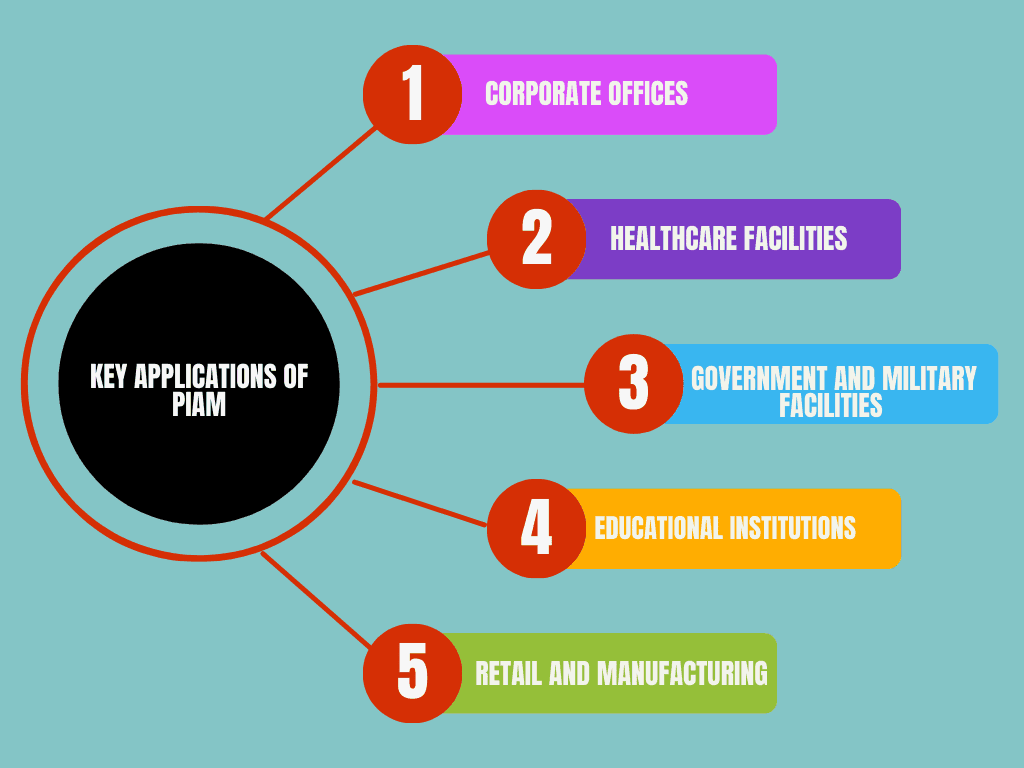
- Corporate Offices: Corporations employ PIAM to ensure that only authorized employees or visitors access certain areas, such as executive boardrooms, data centers, or research labs.
- Healthcare Facilities: Hospitals and clinics use PIAM to control access to areas containing sensitive patient records or pharmaceuticals. This prevents unauthorized individuals from entering secure areas and ensures the privacy of patient data, a requirement in healthcare settings.
- Government and Military Facilities: Security is a top priority in government buildings and military installations, where access to sensitive information is tightly controlled. PIAM systems limit access to secure areas to individuals with the appropriate security clearance, helping to prevent unauthorized access.
- Educational Institutions: Universities and schools use PIAM systems to manage access to classrooms, dormitories, and other facilities, ensuring a safe environment for students and staff. In emergencies, PIAM systems can help locate students, staff, and visitors, aiding in coordinated responses.
- Retail and Manufacturing: Retailers and manufacturers use PIAM to secure warehouses, stockrooms, and manufacturing areas. By restricting access to specific personnel, these businesses can prevent theft and maintain the safety of their operations.
Overall, PIAM offers scalable solutions that enhance security and ensure compliance with various industry standards, making it a versatile tool in today’s security toolkit.
2: Core Components of Physical Identity and Access Management
Key Elements of PIAM
2.1Identity Management
Identity management within PIAM involves creating, updating, and deleting identity records for everyone who may access a facility, including employees, contractors, and visitors. Identity management tracks each person’s status and role, ensuring that their access permissions match their responsibilities.
An effective identity management system verifies each individual’s credentials, making sure that only authorized individuals enter secure areas. This can involve processes such as biometric verification, badge issuance, or PIN assignment. Identity management also helps organizations adjust permissions in real time, allowing for quick responses to changing access needs, such as employee role changes or visitor access adjustments.
2.2 Access Control Systems
Access control systems are the physical or digital tools used to grant or deny access. PIAM systems can integrate with access control technologies like keycards, PINs, and biometric readers. Each of these methods has advantages and is selected based on the security level of each area.
Biometric access, for example, provides a high level of security because it requires unique physical characteristics (like fingerprints or retina scans) to grant access. Keycards or RFID badges, on the other hand, are useful for general areas where ease of entry is important. By combining these tools, organizations can maintain strict access in high-security areas while keeping other areas easily accessible.

2.3 Credentialing and Verification
Credentialing assigns and verifies each individual’s access rights. It can include issuing badges, generating unique PINs, or recording biometric data. Verification processes within PIAM ensure that each credential is up to date and valid, preventing access by former employees or unauthorized visitors.
Credentialing helps prevent security risks associated with lost or stolen access cards. For example, biometric verification requires the individual’s physical presence, ensuring that a stolen badge alone would not grant access to a secure area.
2.4 Integration with IT Security
PIAM integrates with IT security systems to provide a seamless approach to access management. In organizations where digital security is as critical as physical security, integrating PIAM with IT systems allows for unified monitoring and response. For instance, if an individual is terminated, PIAM can immediately revoke their access to both physical locations and digital systems.
This integration also helps manage security alerts and responses. If suspicious activity is detected, such as repeated failed access attempts, both the PIAM and IT systems can alert security personnel, allowing them to take swift action.
3: The Benefits of Implementing PIAM
Why PIAM is a Game-Changer for Security
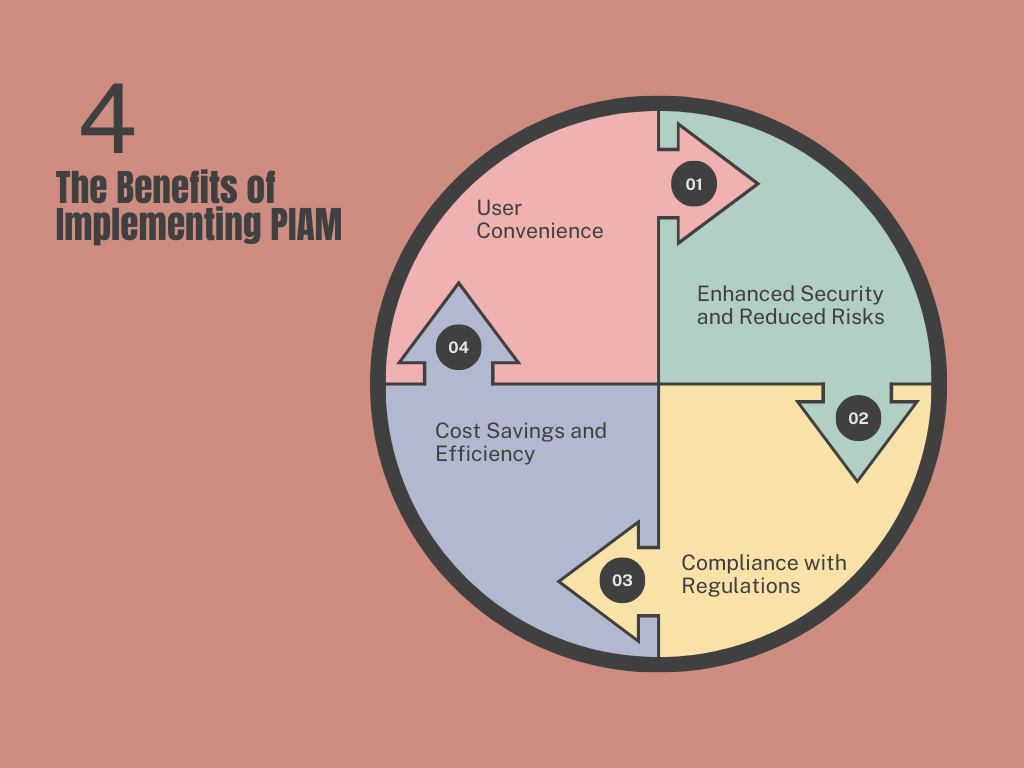
3.1 Enhanced Security and Reduced Risks
PIAM reduces risks by adding layers of verification and providing detailed tracking. Real-time monitoring allows security teams to detect and address unauthorized access attempts immediately, thus reducing security vulnerabilities.
Additionally, the integrated approach of PIAM helps companies identify potential risks. By logging all entries and exits, PIAM provides security teams with comprehensive data that can be analyzed to spot patterns or risks.
3.2 Compliance with Regulations
PIAM helps companies comply with industry-specific regulations. In sectors like healthcare or finance, regulatory standards demand that companies maintain accurate access records. PIAM meets this need by recording access data automatically and securely.
PIAM systems also help with audit readiness. Should an organization face a compliance inspection, PIAM provides readily available records that show who accessed specific areas and when, simplifying the process and reducing administrative burden.
3.3 Cost Savings and Efficiency
PIAM systems streamline operations, reducing the workload on security staff by automating access control tasks. Over time, this automation results in cost savings, as fewer resources are required for manual oversight of access points. Additionally, PIAM systems reduce the likelihood of security incidents that can lead to costly breaches or property loss.
Automated processes also mean that PIAM can update or revoke access in real-time, responding instantly to changes in employee status or visitor access. This level of efficiency improves overall productivity by reducing downtime associated with manual access management.
3.4 User Convenience
PIAM streamlines access for authorized users, delivering a more seamless and user-friendly experience. With up-to-date identity management, employees and visitors face fewer obstacles when entering secure areas. For example, with biometric access, authorized personnel can quickly enter secure zones without fumbling with badges or PIN codes. This not only improves user satisfaction but also keeps workflows moving efficiently.
PIAM also reduces the risk of human error. By automating access controls, the system minimizes mistakes, such as forgetting to deactivate a former employee’s access, which can lead to security risks.
Chapter 4: PIAM Technologies and Tools
Technologies Enhancing PIAM Systems
4.1 Access Control Solutions
PIAM incorporates a range of access control technologies, each suited to different levels of security. Common options include biometric readers (like fingerprint, iris, or facial recognition), RFID cards, and PIN-based access. Each technology adds its own layer of security and usability, allowing organizations to tailor access control to specific areas or roles within the organization.
For example, biometric systems, which use unique physical traits, are highly secure because they are difficult to forge or steal. RFID cards are another popular choice, offering both security and convenience, as they allow for fast entry and don’t require physical contact with the reader. PIN codes, on the other hand, are easy to deploy but are generally suited to lower-security areas, as they can be shared or forgotten.
In a PIAM system, these technologies often work in combination. For instance, high-security areas might require both an RFID badge and a biometric scan, providing double security and ensuring only specific individuals can enter.
4.2 Identity Verification Solutions
Verification solutions in PIAM ensure that individuals requesting access are who they say they are. This may involve ID badge verification, biometric scans, or even mobile devices acting as credentials. Verification adds a critical layer, as it prevents unauthorized individuals from gaining access even if they possess valid-looking credentials.
Many PIAM systems use two-factor authentication (2FA), where, for example, an ID badge swipe is combined with a biometric check. This approach makes it harder for unauthorized individuals to bypass security, as they would need both the badge and the physical trait (like a fingerprint) of the person they are impersonating.

4.3 Security Monitoring Systems
Security monitoring systems in PIAM play a crucial role in detecting unusual or unauthorized access attempts. These systems can alert security teams in real-time if a suspicious event occurs, such as multiple failed entry attempts or attempts to access restricted areas outside of normal hours.
Monitoring can also be integrated with CCTV cameras or alarm systems, providing visual verification of any incidents and allowing security teams to respond more effectively. Additionally, these systems create an access log, storing data that can be analyzed later to identify any potential security risks.
4.4 Integrated Platforms
Many organizations are adopting integrated PIAM platforms that bring together access control, identity verification, and monitoring in one unified system. This consolidation simplifies management, as security teams can oversee all aspects of physical identity and access from a single interface.
Integrated platforms also allow for seamless updates and maintenance. For example, if a new employee joins or leaves, their access permissions can be added or removed across all access points in one step. This ensures that security is maintained consistently and that there are no gaps or delays in updating access rights.
5: How to Implement PIAM Effectively
Step-by-Step Guide for PIAM Implementation
Step 1: Assess Security Needs
The first step in implementing PIAM is to assess the unique security needs and vulnerabilities of the organization. This involves identifying areas with sensitive information or assets, as well as evaluating the current security measures in place. A thorough assessment helps determine where PIAM would be most beneficial and what specific technologies (like biometric readers or RFID badges) will be required.
This phase may also involve consulting with security professionals or conducting a risk assessment. The goal is to understand potential threats and how PIAM can address them, creating a tailored plan for effective protection.
Step 2: Define Requirements
After assessing security needs, it’s time to outline the specific requirements for the PIAM system. For instance, high-security areas might need biometric access controls, while general office areas may only need RFID badges. Requirements should also consider the type of data collected, ensuring that privacy and data protection regulations are met.
Defining requirements includes determining how access permissions will be assigned (e.g., based on job role or security clearance) and how the system will handle different types of users, like employees, contractors, and visitors. These decisions will shape the rest of the PIAM implementation process.
Step 3: Choose PIAM Technologies
With requirements in hand, organizations can select the specific technologies that best fit their needs. For high-security zones, biometric scanners or multi-factor authentication might be ideal, while simpler access points could use RFID badges or PIN codes.
It’s essential to choose technologies that not only meet current security needs but can also adapt to future growth. Scalable solutions allow companies to expand their security infrastructure over time, avoiding the need for costly overhauls as the organization grows.
Step 4: Integrate with Existing Systems
To maximize efficiency, PIAM should integrate with existing IT and security systems. Integration ensures a unified approach to security management, with physical and digital systems working together. For example, if an employee’s status changes in the HR system, their access permissions should automatically update in the PIAM system as well.
Integration also allows for centralized monitoring and streamlined updates, as changes to access levels or policies can be applied across the system instantly. This cohesive approach helps organizations maintain consistent security standards across both physical and digital realms.
Chapter 6: Best Practices for PIAM
Tips to Maximize PIAM Effectiveness
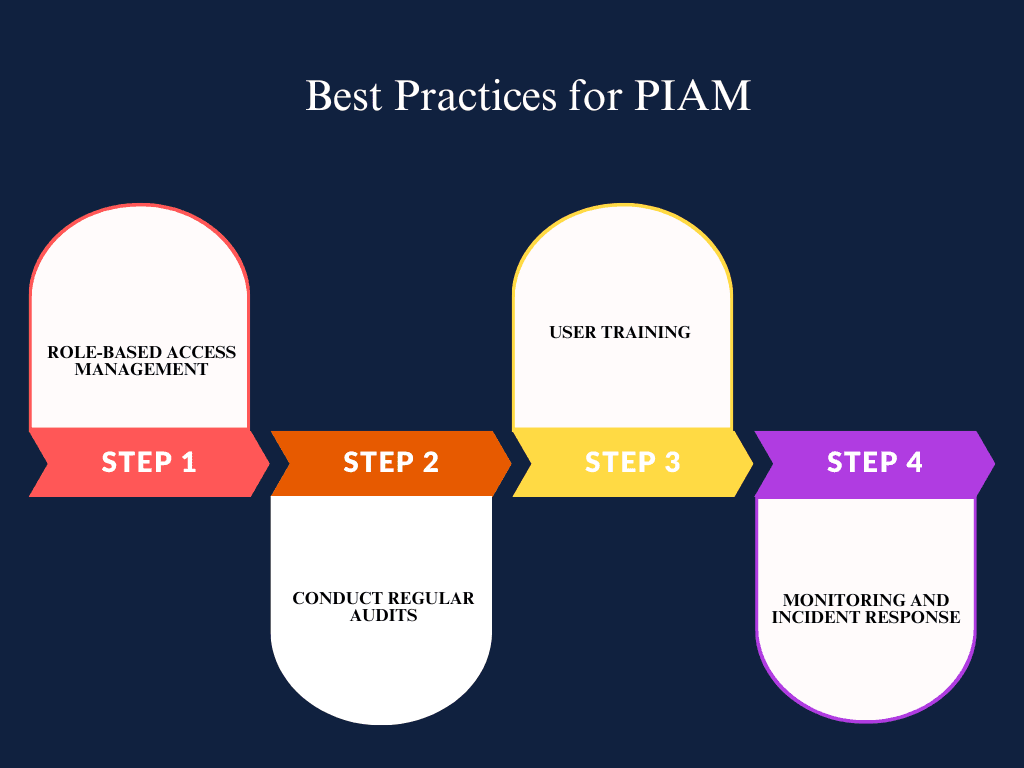
6.1 Role-Based Access Management
One effective best practice is implementing role-based access management (RBAC). With RBAC, access is granted based on a person’s role rather than on an individual basis. This simplifies access control by ensuring that individuals only have permissions aligned with their responsibilities, reducing the risk of unauthorized access.
For example, employees in the IT department might have access to server rooms, while marketing staff would not. This role-based approach prevents accidental access to high-security areas by employees who don’t need entry.
6.2 Conduct Regular Audits
Regular audits are essential to ensure that the PIAM system functions correctly. Audits help identify and resolve any discrepancies, such as outdated access permissions or security gaps. By conducting audits, organizations can confirm that only current employees have access and that permissions reflect job responsibilities.
Audits should be scheduled periodically and should involve testing the system’s responsiveness to breaches or attempts at unauthorized access. Additionally, auditing access logs allows for identifying any patterns that may signal potential security risks.
6.3 User Training
Training employees on how to use PIAM systems effectively can prevent many common security risks. Employees should understand the importance of access control, as well as how to use their credentials (like badges or biometric scans) properly.
Training also helps prevent simple mistakes, like sharing badges or leaving access cards unattended. When employees understand the system and its role in protecting the organization, they are more likely to follow best practices, reducing security vulnerabilities.
6.4 Monitoring and Incident Response
Effective monitoring and quick incident response are key to addressing security threats as they occur. PIAM systems can alert security teams to unusual access events, like failed entry attempts or attempts to access restricted areas.
Organizations should have a clear incident response plan in place, outlining the steps to take when a security alert occurs. This plan should include notifying relevant personnel, securing any breached areas, and logging the incident for future review and audit purposes.
7: Challenges in PIAM Implementation
Key Challenges and How to Overcome Them
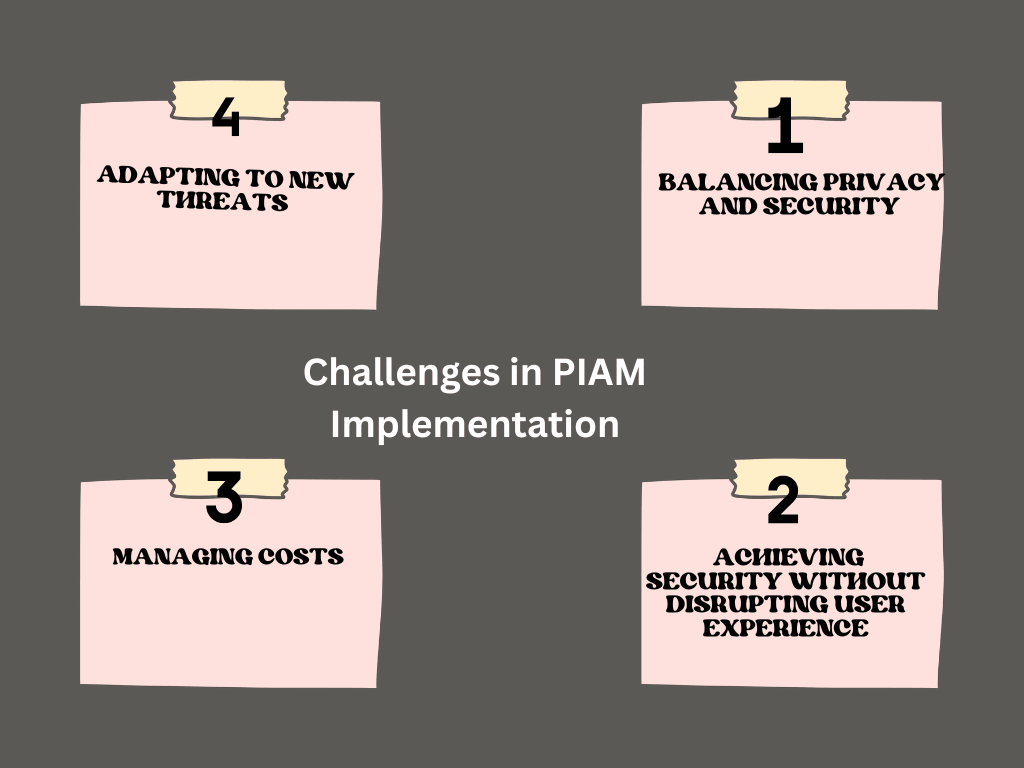
7.1 Balancing Privacy and Security
One challenge with PIAM is balancing the need for security with privacy concerns. Collecting personal data for identity verification, especially biometrics, can raise privacy issues. It’s essential to comply with privacy laws and protect individual data.
Organizations should implement strict data handling practices, such as encryption and limited access to sensitive data. Ensuring transparency with employees about how their data is used and stored also helps build trust and alleviate privacy concerns.
7.2 Achieving Security Without Disrupting User Experience
Another challenge is implementing strong security without impacting user convenience. If a PIAM system requires too many steps or takes too long, it can frustrate users and reduce productivity.
To balance this, organizations can implement single sign-on (SSO) or multi-factor authentication (MFA), which allows for quick yet secure access. Training users to use the system efficiently can also make the process smoother and improve the overall experience.
7.3 Managing Costs
PIAM systems can be costly to implement and maintain, especially in large organizations. Planning and budgeting carefully are crucial to ensure that the investment is sustainable over time.
Some companies start with a smaller-scale implementation and expand it gradually. Additionally, choosing scalable solutions reduces the need for costly replacements in the future.
7.4 Adapting to New Threats
Security threats evolve continuously, requiring organizations to keep their PIAM systems up-to-date. Regularly updating software, conducting audits, and staying informed about new security trends are crucial to staying prepared for new challenges.
This adaptability is essential to maintaining a robust security posture, as even a small vulnerability can expose the organization to risk if not addressed promptly.
Chapter 8: PIAM in Action: Case Studies
Real-Life Examples of PIAM Success
8.1 Corporate Security
In the corporate world, PIAM is invaluable for securing sensitive areas and protecting proprietary data. For example, a large tech company might use PIAM to restrict access to research and development labs, data centers, and executive offices. Employees are assigned access levels based on their roles, ensuring that only qualified personnel can enter these high-security zones.
Biometric systems, like facial recognition and fingerprint scanning, are frequently used in corporate PIAM systems. This ensures that only the right employees have access and that unauthorized individuals can’t use lost or stolen ID badges. Corporations also benefit from the real-time monitoring PIAM offers, which allows security teams to quickly address unusual activity, like attempts to access restricted areas outside of normal working hours.
8.2 Government and Military Applications
Government and military facilities require strict security protocols, as they often house confidential or classified information. PIAM helps manage who can access different levels of security clearance areas, minimizing the risk of unauthorized access. In these environments, PIAM often includes advanced biometric verification systems, like iris scanning or even DNA identification, for maximum security.
For example, a military base might use PIAM to control access to secure zones, ensuring that only personnel with specific security clearances can enter certain areas. Additionally, PIAM systems in government facilities track all access events, creating a detailed audit trail. This trail is crucial for accountability and supports investigations if any security incidents occur.

8.3 Healthcare Facilities
In healthcare settings, PIAM plays a critical role in protecting patient privacy and ensuring safe access to medical facilities. Hospitals and clinics handle sensitive patient data, and access to these records must be carefully controlled. PIAM systems allow hospitals to restrict access to areas with sensitive data, such as patient records or pharmacy stockrooms.
For example, only doctors and authorized personnel can access specific floors or rooms in a hospital. Biometric verification, such as fingerprint scanning, is often used to verify identities before granting access. PIAM also aids in compliance with healthcare privacy regulations, like HIPAA in the United States, by providing records of who accessed patient data or entered secure areas.
8.4 Educational Institutions
Schools and universities also benefit from PIAM, using these systems to secure student dorms, classrooms, and administrative offices. For instance, only enrolled students may access dormitories, preventing unauthorized individuals from entering. PIAM provides peace of mind for students and staff, especially during off-hours when access may be restricted.
Some universities use RFID student IDs combined with PIAM systems to allow secure, easy access to facilities. During emergencies, PIAM also helps security personnel quickly identify and locate students, enhancing the institution’s ability to respond effectively and ensure safety.
9: Future Trends in Physical Identity and Access Management
What’s Next for PIAM?
9.1 Biometric Advancements
Biometric technology is continuously advancing, with new systems like touchless fingerprint scanners, voice recognition, and enhanced facial recognition becoming more accessible. These technologies are more accurate and user-friendly, making them a natural fit for PIAM. Touchless biometrics, for example, allow users to access secure areas without direct contact, which is both convenient and hygienic, a significant benefit in healthcare and food production environments.
In the near future, more organizations are likely to adopt multi-biometric systems that use multiple biometric traits, such as combining facial and fingerprint recognition for higher security. This approach provides an additional layer of identity verification, making unauthorized access even more difficult.
9.2 AI in PIAM
Artificial intelligence (AI) is transforming PIAM systems by enabling predictive analysis and anomaly detection. AI can help detect unusual behavior, such as repeated failed access attempts, and flag them for security teams before a breach occurs. This capability enhances real-time monitoring, allowing for quick responses to potential security threats.
AI can also improve user experience by learning individual user patterns and streamlining the authentication process. For instance, AI can detect when an authorized employee regularly enters a building at specific times and adaptively streamline the access process, making it both more secure and convenient.
9.3 Cloud-Based PIAM
Cloud-based PIAM solutions are gaining popularity, especially among small and mid-sized organizations, as they provide scalability and remote management capabilities. Cloud-based systems allow security teams to manage PIAM from virtually anywhere, which is beneficial for companies with multiple locations or remote facilities. These solutions are also easier to update and maintain, ensuring that the latest security features and patches are always in place.
Cloud-based PIAM systems typically integrate well with other cloud services, creating a cohesive and unified approach to security. As cloud technology advances, more companies are expected to migrate their PIAM solutions to the cloud, benefiting from reduced hardware costs and easier management.
9. 4 Merging Physical and Cybersecurity
As physical and digital security become increasingly intertwined, PIAM systems are playing a role in bridging this gap. Unified security solutions that combine PIAM with cybersecurity tools allow organizations to monitor and manage access across both digital and physical domains. For example, if an employee’s digital access to a database is restricted, their physical access to related areas can automatically be adjusted, providing seamless security across all access points.
This trend toward cyber-physical security integration helps organizations detect and respond to threats holistically. As a result, businesses are better equipped to handle complex security challenges that span both physical and digital environments.

10 Differences between Biometric Access Control and RFID Badge Access Control
| Feature | Biometric Access Control | RFID Badge Access Control |
|---|
| Identification Method | Uses unique physical traits (e.g., fingerprints, facial recognition) | Uses radio-frequency identification (RFID) through a badge or card |
| Security Level | High – Difficult to forge or duplicate, providing a robust level of security | Moderate – Can be compromised if badge/card is lost or stolen |
| User Convenience | High – Users don’t need to carry anything, only provide biometrics | Moderate – Requires users to carry and keep track of a physical card |
| Implementation Cost | Higher – Requires investment in biometric scanners and specialized software | Lower – RFID readers and badges are more affordable and easier to implement |
| Risk of Unauthorized Access | Low – Biometric traits are unique and harder to replicate | Moderate – Badges can be lost, shared, or stolen, increasing the risk |
| Data Privacy Concerns | High – Collecting and storing biometric data raises privacy concerns | Low – Stores only badge information without personal biometrics |
| Speed of Access | Moderate – May take a few seconds for biometric scanning and verification | High – Quick access by simply swiping or tapping the RFID badge |
| Ideal Use Cases | High-security areas (e.g., data centers, government facilities, labs) | Medium-security or general office areas where convenience is prioritized |
11 FAQs
What is PIAM and how does it improve security?
- Answer: Physical Identity and Access Management (PIAM) is a security solution that manages and monitors access to physical spaces by verifying the identity of individuals. It integrates identity verification with access control tools, ensuring that only authorized personnel can enter restricted areas. By linking physical access to individual identities, PIAM adds an extra layer of security, reducing the risk of unauthorized access and enhancing overall safety.
What types of organizations benefit most from implementing PIAM?
- Answer: Organizations across various industries benefit from PIAM, especially those handling sensitive information or requiring high-security environments. This includes healthcare facilities, where patient privacy and restricted medical areas are prioritized; government and military institutions that need secure access control for classified information; corporate offices with sensitive data or intellectual property; and educational institutions managing campus access for students and staff. PIAM also benefits retail and manufacturing sectors by controlling access to stockrooms, warehouses, and production areas, enhancing both security and operational efficiency.
How does biometric access control differ from RFID badge access in PIAM?
- Answer: Biometric access control uses unique physical traits, like fingerprints or facial recognition, to verify identity, providing a high-security level due to its difficulty to forge. RFID badge access, on the other hand, relies on a card or badge that can be swiped or tapped for entry. While RFID is convenient and fast, it is less secure than biometrics, as badges can be lost or stolen.
Is it possible to integrate PIAM with existing IT and cybersecurity systems?
- Answer: Yes, PIAM can be integrated with IT and cybersecurity systems, creating a unified security approach across physical and digital domains. For example, PIAM can sync with an organization’s HR and IT systems, so when an employee leaves, their access to both physical locations and digital resources is automatically revoked. This integration ensures consistent security and reduces the risk of forgotten or outdated access permissions.
What are some challenges in implementing PIAM, and how can they be addressed?
Answer: Implementing PIAM can present challenges such as balancing privacy concerns with security, managing costs, and adapting to new security threats. Addressing these challenges involves transparent data policies to protect user privacy, careful budgeting to manage costs, and regular system updates to keep up with evolving threats. Training staff on proper use and following best practices for audits and monitoring can also enhance the effectiveness of PIA
12 Conclusion
Physical Identity and Access Management (PIAM) is a powerful solution for enhancing security across a wide range of industries. By linking physical access control with digital identity verification, PIAM ensures that only authorized individuals can enter sensitive areas, significantly reducing security risks. The flexibility of PIAM allows it to be tailored to meet the specific needs of different sectors—from healthcare to government, corporate offices, and educational institutions—providing a robust and adaptable security framework.
The implementation of PIAM brings numerous benefits, including regulatory compliance, operational efficiency, and improved user convenience. With advancements in technologies like biometrics, AI, and cloud-based solutions, PIAM systems are becoming even more effective, blending seamlessly with IT and cybersecurity frameworks to create unified security approaches. Although challenges exist, such as managing privacy concerns and balancing costs, careful planning and best practices can help organizations maximize the effectiveness of PIAM systems.As security threats continue to evolve, so too will PIAM solutions, incorporating emerging technologies to meet new challenges. For organizations seeking a comprehensive, efficient, and future-ready approach to securing their physical environments, PIAM represents a foundational strategy, ensuring both peace of mind and the highest standards of security.
