1. Cyber Vulnerabilities in DoD Systems: Threats & Solutions
Cybersecurity has become an integral part of military operations, and with the increasing reliance on digital networks, the U.S. Department of Defense (DoD) must prioritize the protection of its systems. Given the high stakes involved, any cyber vulnerability can have disastrous effects on national security, affecting military readiness, operational efficiency, and the integrity of classified data. In this article, we explore various cyber vulnerabilities in DoD systems, outline the most common threats they face, and suggest robust solutions to mitigate these risks.
2. Understanding Cyber Vulnerabilities in DoD Systems
Cyber vulnerabilities refer to weaknesses or flaws in a system’s defenses that could be exploited by attackers to gain unauthorized access, steal information, or disrupt operations. The DoD’s extensive use of technology to run military operations has made its systems a prime target for cybercriminals and hostile nations. Identifying and addressing these vulnerabilities is key to maintaining national security.
2.1 Types of Cyber Vulnerabilities in DoD Systems
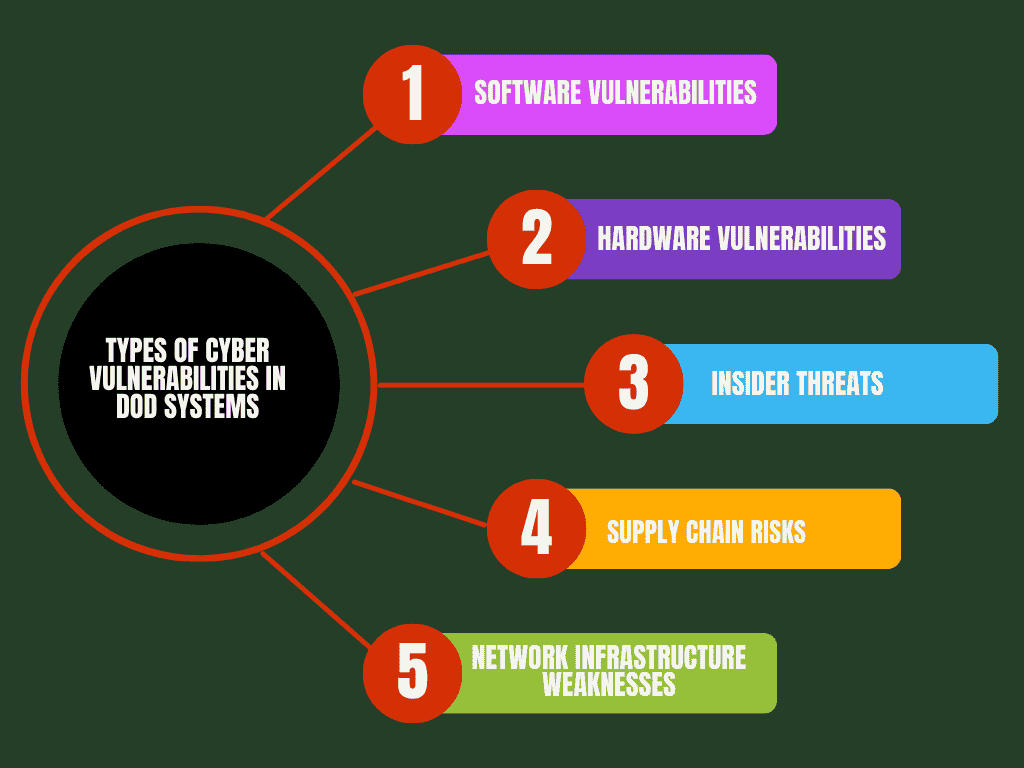
1 Software Vulnerabilities
The use of outdated software or lack of regular patching is one of the most common vulnerabilities found in military systems. Software vulnerabilities occur when there is a flaw or gap in a program’s code that attackers can exploit. Hackers often take advantage of these gaps to gain access to military networks. For instance, malware like viruses, Trojans, or worms can be introduced into the system through unpatched software. The DoD’s reliance on legacy systems, which may not be updated as frequently as newer systems, increases the risk of attacks.
To mitigate this risk, the DoD should implement a robust software patch management process that includes regular updates and vulnerability scanning. A proactive approach would significantly reduce the possibility of cyber intrusions exploiting known vulnerabilities.
2 Hardware Vulnerabilities
Hardware vulnerabilities refer to weaknesses or defects within physical devices or infrastructure. This includes vulnerabilities in servers, routers, and communications equipment used by the military. Some of these vulnerabilities may arise during the manufacturing process, where malicious actors can implant backdoors into hardware components. These backdoors could allow hackers to infiltrate the system without detection.
A significant concern with hardware vulnerabilities is the supply chain. The DoD relies on multiple contractors and manufacturers for its hardware, and if any of these suppliers are compromised, it could have a ripple effect throughout the military network. For instance, hardware tampering can lead to the introduction of malware or even spyware. Securing the hardware supply chain through rigorous vetting and security checks for all components is essential.
3 Insider Threats
Insider threats are among the most dangerous types of cyber vulnerabilities because they involve individuals who already have legitimate access to the network. This could be a DoD employee, contractor, or supplier with malicious intent or an employee who unintentionally causes harm through negligence. For example, a person with administrative privileges might inadvertently leak sensitive data or be coerced into assisting an external adversary.
To counter insider threats, the DoD should adopt a strict policy of least privilege, ensuring individuals only have access to information necessary for their job. Regular employee training on recognizing phishing attempts and maintaining good cybersecurity hygiene is essential. Additionally, monitoring user activity with advanced behavioral analytics tools can help detect suspicious actions within the network.
4 Supply Chain Risks
Supply chain risks are particularly critical in defense sectors where vendors and contractors play a large role in providing both hardware and software. When a third-party supplier is compromised, it can create vulnerabilities that extend into the DoD’s internal systems. An attacker could introduce a backdoor or malware into a software update that is subsequently installed on DoD systems. The SolarWinds cyberattack is a recent example of a supply chain attack that affected multiple government agencies and organizations.
To reduce the risk of such incidents, the DoD must implement stronger vetting procedures for suppliers and contractors. This should include conducting regular security audits of third-party systems and enforcing compliance with cybersecurity standards.
5 Network Infrastructure Weaknesses
Network infrastructure forms the backbone of military operations, providing connectivity for communications, data sharing, and tactical systems. However, network infrastructure can also harbor vulnerabilities. For instance, poorly configured firewalls, insufficient encryption, and lack of access control mechanisms can make networks easier to breach. Without effective monitoring and threat detection systems, cyberattacks can go undetected for extended periods.
To mitigate these risks, the DoD must focus on configuring robust firewalls, implementing multi-layered encryption, and continuously monitoring for suspicious activities. Additionally, employing intrusion detection systems (IDS) and intrusion prevention systems (IPS) can provide early warning signals in case of a breach.
3. Major Cyber Threats to DoD Systems
Cyber threats have evolved, and today, they are more sophisticated than ever. The DoD faces several serious threats that can compromise its operations, sensitive data, and strategic objectives. These threats can be state-sponsored or carried out by criminal organizations, and they often leverage advanced techniques to bypass security measures.
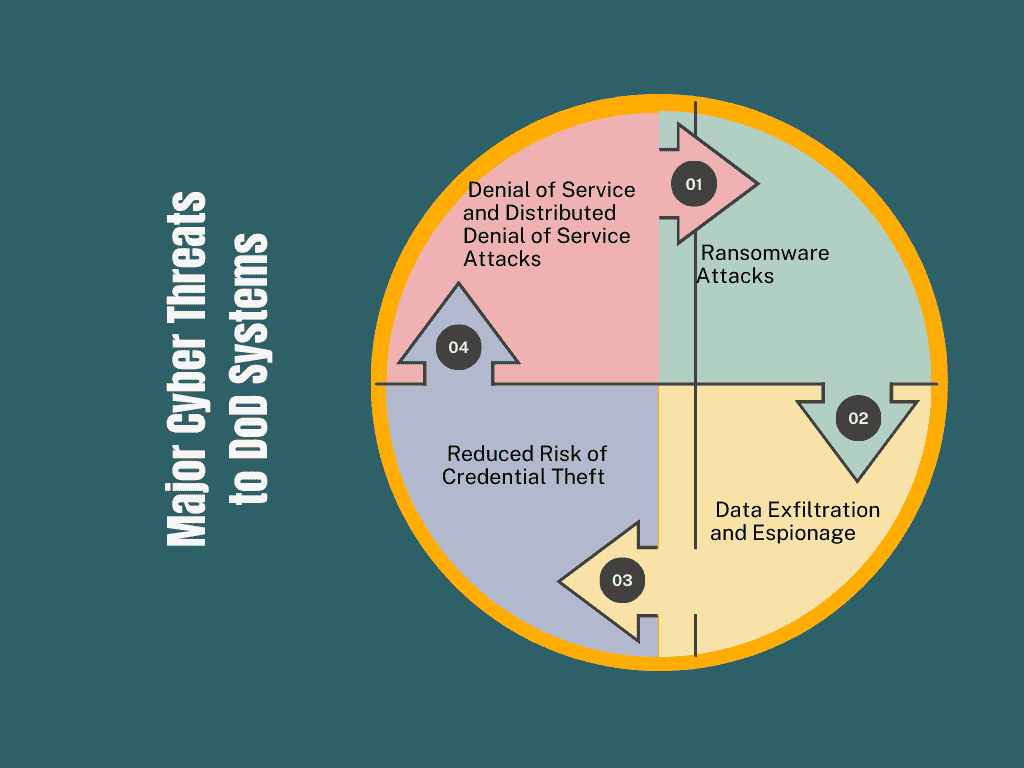
3.1 Advanced Persistent Threats (APTs)
APTs are one of the most significant threats to DoD systems. These threats involve long-term, highly sophisticated attacks aimed at infiltrating a system and staying undetected for an extended period. Typically, APTs are carried out by state-sponsored hackers with significant resources at their disposal. They often use multiple stages to compromise systems, starting with phishing emails or malware to gain entry and escalating to advanced techniques such as spear-phishing and social engineering.
Once an APT has gained access to a system, it can remain hidden while gathering sensitive data, including intelligence and military plans. The key characteristic of an APT is its persistence—these attacks are designed to maintain access for months or even years, slowly harvesting information.
To defend against APTs, the DoD must implement advanced detection tools like behavior analytics and artificial intelligence (AI) to spot abnormal network activity. Additionally, employing strong endpoint protection and continuous monitoring can help identify compromised devices or users.
3.2 Ransomware Attacks
Ransomware is a form of malicious software that locks users out of their systems or encrypts their data, demanding payment to restore access. These attacks can target both civilian and military systems, causing significant operational disruptions. The DoD has been a target of ransomware attacks, with adversaries attempting to hold critical data hostage in exchange for payment.
In the military context, ransomware could compromise command and control systems, delay military operations, or even steal classified information. The best defense against ransomware is a comprehensive backup strategy that ensures that even if systems are compromised, operations can continue from a secure backup.
3.3 Data Exfiltration and Espionage
Data exfiltration involves the unauthorized transfer of sensitive data from a system to an external location. In the context of the DoD, this threat often involves stealing classified information, intelligence, or strategic military data. Espionage can be state-sponsored or carried out by criminal organizations seeking to gain an advantage in a geopolitical conflict or financial market.
To mitigate the risk of data exfiltration, the DoD needs robust encryption methods, both in transit and at rest. Additionally, implementing strict access controls and data loss prevention systems can help prevent unauthorized transfers of sensitive data.
3.4 Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
Denial of Service (DoS) attacks, particularly Distributed Denial of Service (DDoS) attacks, aim to overwhelm a system’s resources, causing it to crash and become inaccessible. These attacks are often used to disrupt critical operations or distract security teams while other attacks are carried out. A DDoS attack could disrupt communications between military units or shut down critical systems used in defense operations.
To prevent DoS and DDoS attacks, the DoD should employ network traffic monitoring tools that can detect unusual spikes in data traffic and take immediate action to block malicious requests. Additionally, leveraging cloud-based DDoS mitigation services can help distribute traffic loads and absorb attacks.
4. Impact of Cyber Vulnerabilities on DoD Operations
Cyber vulnerabilities in DoD systems can have wide-ranging effects, not just on military operations but on national security as a whole. The potential impacts of cyber breaches are significant, and even minor disruptions could have catastrophic consequences. In this chapter, we explore how cyber vulnerabilities affect the DoD’s ability to carry out its missions.
4.1 Operational Disruptions
A successful cyberattack can halt or delay military operations, compromising mission-critical tasks. For example, if an adversary takes control of a military satellite or disrupts air traffic control systems, it could impede the movement of personnel, equipment, and resources, putting lives at risk and delaying strategic objectives.
Additionally, cyberattacks could disrupt communications between military units, preventing them from coordinating effectively. This could lead to confusion, miscommunication, and, ultimately, failure to complete objectives.
To mitigate these risks, the DoD must develop strong contingency plans and invest in resilient communication systems that can continue operating even under attack.

4.2 National Security
Cyber vulnerabilities in the DoD also pose a direct threat to national security. If adversaries gain access to classified military information, they could compromise the U.S. government’s strategic advantages, including its intelligence, defense plans, and technological capabilities. Data breaches could undermine the U.S.’s geopolitical position, damaging international alliances and enabling adversaries to gain an upper hand in negotiations or warfare.
The DoD must ensure the protection of sensitive data, particularly regarding nuclear capabilities, defense strategies, and intelligence operations. Implementing stringent cybersecurity measures such as end-to-end encryption, multi-factor authentication, and real-time threat intelligence can protect against espionage and data exfiltration.
4.3 Financial Losses
Cyber vulnerabilities can also result in substantial financial losses. Aside from the direct costs associated with responding to cyberattacks, such as recovery and system repairs, there are long-term financial implications. These may include reputational damage, loss of public trust, and legal fees associated with breach notifications or lawsuits.
Investing in proactive cybersecurity measures, such as threat intelligence and continuous monitoring, is essential for minimizing these financial impacts. By identifying vulnerabilities before they are exploited, the DoD can reduce the likelihood of costly security breaches.
5. Solutions for Enhancing Cybersecurity in DoD Systems
To protect its systems and ensure continued operational success, the DoD must implement comprehensive solutions to address cyber vulnerabilities. In this chapter, we provide an overview of strategies and technologies that can be adopted to enhance cybersecurity.
5.1 Continuous Monitoring and Threat Detection
Continuous monitoring and real-time threat detection are critical components of a robust cybersecurity strategy. By employing advanced tools like intrusion detection systems (IDS), the DoD can identify suspicious activities and respond to threats before they escalate. Machine learning and AI-powered analytics can help identify patterns in network traffic and user behavior, enabling proactive threat management.
5.2 Advanced Encryption and Authentication
Encryption is essential for protecting sensitive data in transit and at rest. The DoD must adopt end-to-end encryption for all communications and ensure that all classified data is securely stored. Additionally, multi-factor authentication (MFA) must be enforced for all users accessing DoD systems to prevent unauthorized access.

5.3 Employee Training and Awareness
A significant portion of cyber vulnerabilities can be mitigated through employee training. By educating personnel on best practices for cybersecurity, such as identifying phishing emails and using strong passwords, the DoD can reduce the risk of human error leading to a security breach. Regular training sessions should be held to keep personnel updated on the latest threats and tactics used by cybercriminals.
5.4 Collaboration with Private Sector
The private sector is home to some of the world’s leading cybersecurity experts and technologies. The DoD must strengthen its partnerships with private companies to share threat intelligence and access cutting-edge solutions. Collaborative efforts can provide the DoD with a more comprehensive defense strategy, helping it stay ahead of emerging threats.
6. Recent Cybersecurity Incidents in DoD Systems
Cybersecurity incidents in the U.S. Department of Defense (DoD) have highlighted the vulnerabilities of military systems and the critical need for continuous improvement in defense measures. These incidents provide valuable lessons in understanding the nature of cyber threats and the importance of maintaining robust cybersecurity protocols.
6.1 Case Studies of High-Profile Cyber Attacks
6.1.1 The SolarWinds Hack (2020)
One of the most significant cybersecurity breaches in recent history, the SolarWinds attack, involved a sophisticated supply chain compromise. Hackers, believed to be Russian state-sponsored actors, infiltrated the SolarWinds Orion software platform, which is used by multiple U.S. government agencies, including the DoD. The attackers inserted a backdoor into the software updates, allowing them to monitor and access sensitive systems undetected for several months.
This incident highlighted vulnerabilities in software supply chains, where attackers can infiltrate trusted vendors to gain access to multiple systems at once. The SolarWinds breach compromised classified data and government communications, emphasizing the importance of securing both internal systems and external suppliers.
6.1.2 The OPM Breach (2015)
The 2015 Office of Personnel Management (OPM) breach is another significant example of a cyberattack against U.S. government systems. Hackers, reportedly from China, gained access to the personal data of over 21 million individuals, including security clearance information. The breach exposed sensitive details about DoD personnel, contractors, and others with access to classified information.
The breach showed that personal and background information could be exploited to target government employees and contractors, raising concerns over insider threats. It also underscored the need for better data protection, particularly concerning sensitive personal and security clearance records.
6.2 Lessons Learned from Past Incidents
The SolarWinds and OPM incidents, among others, have provided critical lessons on the vulnerabilities in DoD systems. Key takeaways include:
- Supply Chain Security: Attacks on trusted vendors can be as devastating as direct attacks on government systems. The DoD must enforce stronger vetting and continuous monitoring of all third-party vendors.
- Data Protection: Sensitive data, particularly information related to personnel and operations, must be safeguarded through encryption and access controls. Storing classified information in more secure environments reduces the risk of data breaches.
- Incident Response: Early detection and rapid response are crucial to mitigating the effects of a breach. The DoD must continue to invest in real-time monitoring and AI-driven threat detection systems to identify and neutralize threats quickly.
7. Cyber Defense Strategies for DoD Systems
To protect against the growing array of cyber threats, the DoD needs a comprehensive approach to cybersecurity. This involves implementing multiple layers of defense, ensuring robust endpoint security, and investing in the development of secure software and systems.
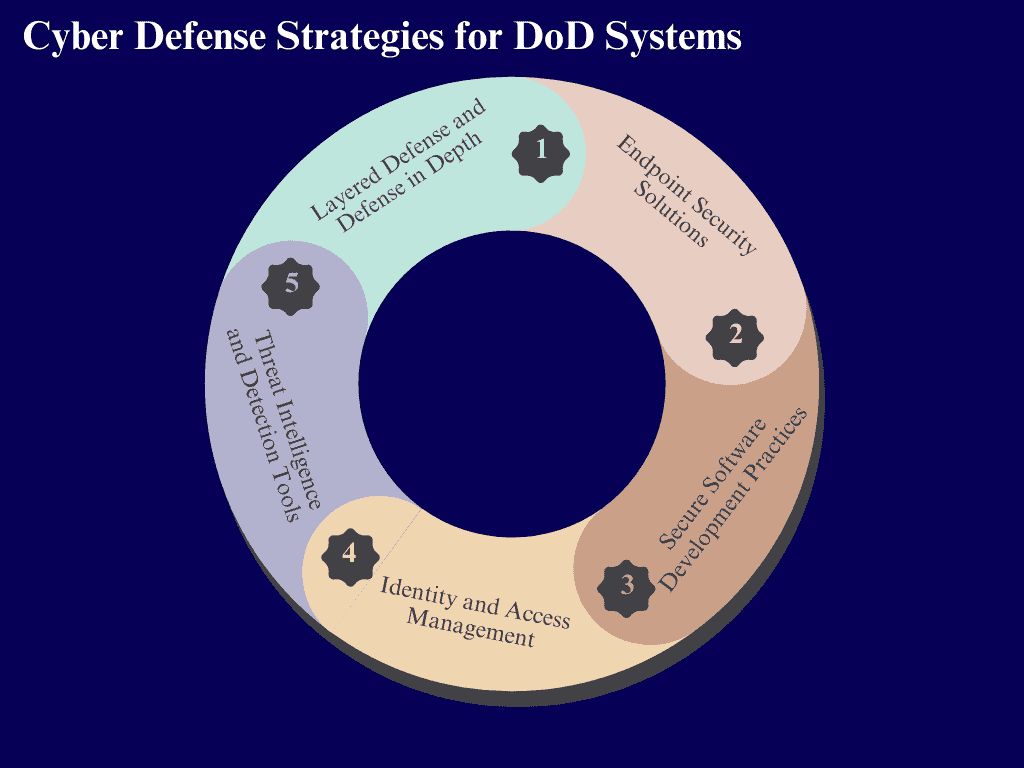
7.1 Layered Defense and Defense in Depth
A layered defense strategy is a multi-tiered approach to security that involves multiple lines of defense, making it more difficult for cyber attackers to breach systems. This concept, known as “defense in depth,” involves adding redundant layers of protection throughout the entire system architecture. These layers include firewalls, intrusion detection systems (IDS), endpoint protection, and encryption protocols.
By implementing defense in depth, the DoD can ensure that even if one layer is compromised, there are other protective measures in place to stop further infiltration and minimize damage. This approach also helps with incident detection and response, enabling faster identification and mitigation of cyber threats.
7.2 Endpoint Security Solutions
Endpoint security focuses on protecting individual devices (such as computers, smartphones, and servers) that connect to the DoD network. Securing endpoints is critical because these devices are often the entry points for cyberattacks.
The DoD must employ advanced endpoint protection solutions, including antivirus software, device encryption, and security patches. Regular updates to endpoint security software ensure that known vulnerabilities are patched before they can be exploited.
7.3 Secure Software Development Practices
Secure software development practices are essential for reducing vulnerabilities in custom applications used within DoD systems. Implementing secure coding standards, conducting regular code reviews, and using automated security testing tools can help identify and mitigate flaws before deployment.
Moreover, adopting secure software development lifecycle (SDLC) practices ensures that security is built into the software from the start. This includes regular vulnerability assessments and patch management to address issues as they arise.
7.4 Identity and Access Management
Effective identity and access management (IAM) is crucial for ensuring that only authorized personnel have access to sensitive systems and data. The DoD must use multi-factor authentication (MFA) and strict access control policies to reduce the risk of unauthorized access, whether due to insider threats or external cyberattacks.
IAM solutions should include role-based access controls (RBAC), where access is granted based on the user’s role and necessity. This ensures that employees only have access to the data required for their work and no more.
7.5 Threat Intelligence and Detection Tools
Cyber threats are constantly evolving, making it essential for the DoD to invest in advanced threat intelligence tools. These tools aggregate data from various sources, including network traffic, system logs, and external threat intelligence feeds, to detect emerging threats and vulnerabilities.
Artificial intelligence (AI) and machine learning (ML) can help in automating the detection of abnormal activities, identifying new attack patterns, and improving response times. The DoD should also engage in collaborative intelligence sharing with other government agencies and private sector partners to enhance threat detection capabilities.
8. Mitigation Techniques and Solutions
To mitigate the risks posed by cyber vulnerabilities, the DoD must implement a range of strategies and solutions to prevent attacks and reduce the impact of breaches.
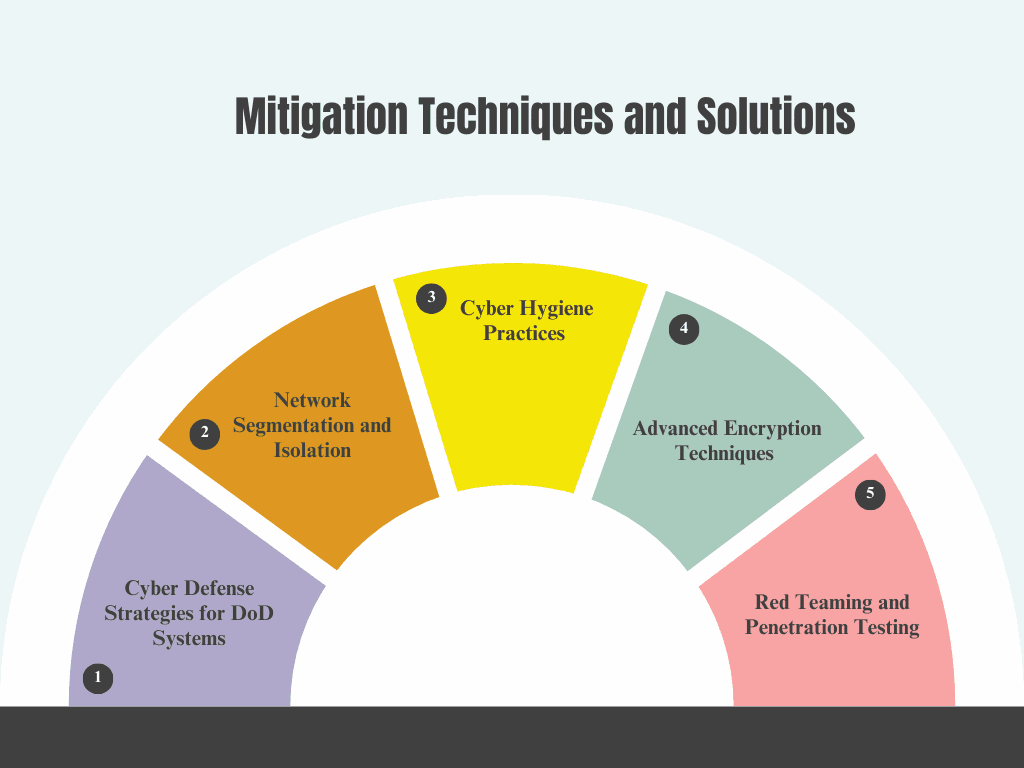
8.1 Patch Management and Vulnerability Scanning
Regular patch management is one of the most effective ways to address vulnerabilities in software and hardware systems. By applying patches as soon as they are released, the DoD can ensure that critical vulnerabilities are fixed before they can be exploited by attackers.
Vulnerability scanning tools can help identify unpatched systems or software, ensuring that patches are applied in a timely manner. Automated scanning and patch management solutions can streamline this process.
8.2 Network Segmentation and Isolation
Network segmentation involves dividing the network into smaller, isolated segments to limit the impact of a cyberattack. If one segment is compromised, the attacker is unable to move freely across the entire network. This technique helps contain attacks and prevents attackers from gaining access to mission-critical systems.
The DoD should implement network segmentation for sensitive systems, ensuring that only authorized users and devices can access certain network segments. This also helps with monitoring and incident response, as attackers are more likely to be detected in smaller, isolated environments.
8.3 Cyber Hygiene Practices
Cyber hygiene refers to the practice of maintaining good cybersecurity habits to prevent attacks. For the DoD, this includes ensuring that all devices are updated with the latest security patches, using strong passwords, and adhering to cybersecurity best practices.
The DoD must promote a culture of cybersecurity awareness among all personnel, ensuring that they understand the importance of regularly updating software, using secure networks, and avoiding risky online behavior.
8.4 Advanced Encryption Techniques
Encryption is essential for protecting sensitive data both in transit and at rest. The DoD must implement strong encryption algorithms to secure communications and prevent unauthorized access to critical information. This includes encrypting email communications, data backups, and classified documents.
In addition to traditional encryption methods, the DoD should explore the use of quantum-safe encryption, which will offer even greater security in the future.
8.5 Red Teaming and Penetration Testing
Red teaming involves simulating real-world cyberattacks to identify vulnerabilities in systems before malicious actors can exploit them. Penetration testing is a similar approach, where ethical hackers attempt to breach DoD systems to discover weaknesses.
Both techniques are valuable for identifying hidden vulnerabilities and testing the effectiveness of current defense mechanisms. The DoD should conduct regular red team exercises and penetration tests to ensure that systems remain secure against evolving threats.
9. Collaboration and Information Sharing
Collaboration between the public and private sectors, as well as between different government agencies, is crucial for combating cyber threats. The DoD must strengthen its partnerships with external organizations to improve threat detection, response, and overall cybersecurity.
9.1 Public-Private Partnerships in Cybersecurity
Public-private partnerships (PPPs) play a vital role in enhancing cybersecurity by combining government resources with the expertise and technology of private companies. The DoD should continue to work closely with private sector companies to share threat intelligence, best practices, and advanced security solutions.
9.2 Role of Intelligence Agencies and Cybersecurity Task Forces
Intelligence agencies, such as the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI), play a key role in identifying cyber threats and responding to incidents. The DoD should collaborate with these agencies to gather actionable intelligence on cyber threats and to launch coordinated responses.
Cybersecurity task forces, such as U.S. Cyber Command, are instrumental in protecting military networks and conducting offensive cyber operations. The DoD must continue to invest in these task forces to ensure national security.
9.3 Cross-Agency Collaboration within the DoD
Within the DoD itself, cross-agency collaboration is essential for addressing cybersecurity issues across different branches of the military. Information sharing between the Army, Navy, Air Force, and other agencies ensures a unified approach to cybersecurity and reduces the risk of operational silos.
10. Legal and Ethical Considerations
As cyber threats evolve, the DoD must navigate complex legal and ethical considerations when defending against cyberattacks and engaging in offensive operations.
10.1 International Laws and Cyber Warfare
International laws on cyber warfare are still
developing, but existing frameworks, such as the United Nations’ guidelines on international cyber law, offer some guidance. The DoD must adhere to these laws while engaging in cyber defense and offensive operations, ensuring that actions do not violate international norms or lead to unintended consequences.
10.2 Privacy and Civil Liberties
The balance between cybersecurity and privacy is a critical issue. The DoD must ensure that its cybersecurity measures do not infringe upon the privacy rights of individuals, particularly when monitoring personnel or conducting surveillance. Ensuring transparency and accountability in these practices is essential.
10.3 Ethical Implications of Cyber Defense Strategies
The ethical implications of cyber defense strategies include the use of surveillance, data collection, and offensive cyber operations. The DoD must ensure that its actions are proportionate, justifiable, and consistent with national and international ethical standards.
11. Future Directions and Emerging Technologies
As technology advances, the DoD must continue to adapt its cybersecurity strategies to protect against emerging threats.
11.1 Artificial Intelligence in Cyber Defense
Artificial intelligence (AI) is playing an increasing role in cybersecurity by automating threat detection and response. The DoD should continue to invest in AI-based systems that can predict and identify cyberattacks in real-time, improving the overall speed and efficiency of defense operations.
11.2 Quantum Computing and Cryptography
Quantum computing has the potential to break traditional encryption methods. However, it also offers the opportunity to develop quantum-safe encryption algorithms that will provide stronger protection against future cyber threats. The DoD should begin researching quantum computing and its potential impact on cybersecurity.
11.3 Blockchain for Cybersecurity
Blockchain technology offers potential benefits for cybersecurity, such as enhancing data integrity, improving secure transactions, and enabling decentralized security models. The DoD should explore the use of blockchain for improving data protection and preventing tampering with critical military systems.
12 Difference between focus area and Key Distinction
| Chapter | Focus Area | Key Distinction |
|---|
| 1. Introduction to Cyber Vulnerabilities in DoD | Overview of cyber vulnerabilities and their impact on the DoD. | Focuses on the foundational understanding of cyber threats and risks faced by DoD systems. |
| 2. Recent Cybersecurity Incidents in DoD Systems | Case studies of past cyberattacks and lessons learned. | Provides concrete examples of high-profile cyberattacks and their repercussions. |
| 3. Financial Impacts of Cyber Vulnerabilities | Examines the financial consequences of security breaches in DoD systems. | Focuses specifically on the economic implications and long-term costs associated with cyber vulnerabilities. |
| 4. Solutions for Enhancing Cybersecurity in DoD Systems | Comprehensive solutions to bolster cybersecurity in the DoD. | Focuses on preventive and reactive strategies, emphasizing technology and human-centric solutions for enhancing security. |
| 5. Mitigation Techniques and Solutions | In-depth techniques for mitigating risks and addressing vulnerabilities in DoD systems. | Practical and technical solutions (e.g., patch management, encryption) that can directly reduce cyber vulnerabilities. |
| 6. Collaboration and Information Sharing | Discusses the role of collaboration between the public and private sectors, and government agencies. | Highlights the importance of collaboration in addressing cyber threats through information-sharing and strategic partnerships. |
| 7. Legal and Ethical Considerations | Legal, privacy, and ethical issues related to cybersecurity practices in defense systems. | Focuses on the legal boundaries, privacy issues, and ethical considerations of cyber defense strategies. |
| 8. Future Directions and Emerging Technologies | Exploration of emerging technologies that could shape the future of cybersecurity in the DoD. | Examines new and evolving technologies, such as AI, quantum computing, and blockchain, and their role in future defense strategies. |
13 FAQS
1. What are the main cybersecurity threats to DoD systems?
Answer: The primary cybersecurity threats to DoD systems include state-sponsored cyberattacks, insider threats, malware, phishing attacks, and supply chain vulnerabilities. These threats are constantly evolving, and the DoD must stay ahead of emerging tactics to protect sensitive military data and systems.
2. How does the DoD defend against cyber threats?
Answer: The DoD employs a multi-layered defense strategy known as “Defense in Depth.” This includes securing endpoints, implementing firewalls, using intrusion detection systems (IDS), and ensuring strict identity and access management policies. Additionally, the DoD utilizes threat intelligence tools and secure software development practices to proactively defend against cyberattacks.
3. What are mitigation techniques for reducing cyber vulnerabilities in DoD systems?
Answer: Key mitigation techniques include patch management, vulnerability scanning, and network segmentation. “These practices play a crucial role in detecting and addressing potential vulnerabilities before they are exploited.” The DoD also employs advanced encryption methods and conducts red teaming and penetration testing to detect weaknesses in the system.
4. Why is collaboration between the public and private sectors important for DoD cybersecurity?
Answer: Collaboration between the public and private sectors helps the DoD access advanced cybersecurity technologies and intelligence, improving threat detection and response capabilities. Public-private partnerships allow for sharing critical threat data and best practices, enhancing overall cybersecurity resilience.
5. How are emerging technologies like AI and quantum computing shaping the future of DoD cybersecurity?
Answer: Emerging technologies such as Artificial Intelligence (AI) and Quantum Computing are revolutionizing cybersecurity. AI helps automate threat detection and response, improving reaction times to cyber incidents. Quantum computing promises to enhance encryption methods, making them more secure against future cyberattacks. These technologies are expected to play a critical role in maintaining national security in the face of evolving cyber threats.
14 Conclusion
Conclusion
Cybersecurity is crucial for the Department of Defense (DoD) to protect sensitive military data and systems from evolving cyber threats. Key strategies like Defense in Depth, patch management, and secure software practices help prevent and mitigate attacks. Collaboration with the private sector and intelligence agencies enhances the DoD’s ability to respond to threats quickly. Emerging technologies such as Artificial Intelligence and Quantum Computing will continue to shape cybersecurity efforts, offering new ways to defend against future attacks. The DoD must stay adaptable, investing in both advanced technologies and skilled personnel to maintain robust defense against cyber risks.