In today’s digital world, cybersecurity threats are more frequent and advanced, making it essential for organizations to ensure their systems and data are secure. Vulnerability Assessment (VA) and Penetration Testing (Pen Testing) are two critical components of a strong cybersecurity defense. This guide will walk you through these processes, explaining their importance, methodologies, tools, and best practices.
1. Understanding Vulnerability Assessment & Penetration Testing
1.1 What are Vulnerability Assessment and Penetration Testing?
Vulnerability Assessment and Penetration Testing are two vital components of a robust cybersecurity strategy. Vulnerability Assessment refers to the process of identifying, quantifying, and prioritizing vulnerabilities in a system, while Penetration Testing simulates a real-world attack to exploit these vulnerabilities. Understanding the distinction between the two is essential for implementing effective security measures.
1.2 Why are Both Crucial for Cybersecurity?
In today’s digital landscape, where cyber threats are increasingly sophisticated, relying solely on a firewall or antivirus software is insufficient. Organizations must regularly assess their systems to identify potential weaknesses. A Vulnerability Assessment provides a clear picture of security gaps, while Penetration Testing helps organizations understand the potential impact of those vulnerabilities by mimicking a cyber-attack. Here’s a rephrased version of your sentence to make it unique: Collectively, they establish a robust strategy for defense.”
1.3 Real-World Examples of Security Breaches
Numerous high-profile security breaches underscore the importance of these practices. For example, the 2017 Equifax breach affected over 147 million people due to unpatched vulnerabilities. Similarly, the Marriott breach exposed the personal information of around 500 million guests, primarily due to inadequate vulnerability management. These incidents illustrate the dire consequences of neglecting VA and Pen Testing in maintaining cybersecurity.
2. The Basics of Vulnerability Assessment
2.1 What is Vulnerability Assessment?
Here’s a rephrased version of your sentence:
A Vulnerability Assessment involves a methodical process for detecting and assessing security flaws within an organization’s infrastructure.This process involves using various tools and techniques to scan systems, applications, and networks for known vulnerabilities.
2.2 Types of Vulnerabilities
- Network Vulnerabilities: These are weaknesses in a network’s security architecture that can be exploited by attackers. Examples include open ports, weak passwords, and outdated software.
- Software Vulnerabilities: Flaws in application code, such as SQL injection or cross-site scripting (XSS), can lead to unauthorized access and data breaches.
- Physical Vulnerabilities: These vulnerabilities arise from inadequate physical security measures, such as poor access control or unmonitored server rooms.
2.3 Common Tools and Software for Vulnerability Scanning
Several tools can assist in conducting a Vulnerability Assessment. Nessus is one of the most popular tools for scanning network vulnerabilities, while QualysGuard provides cloud-based vulnerability management. OpenVAS is another open-source solution that helps organizations identify potential security issues effectively. Each tool offers unique features, allowing organizations to choose the right one based on their specific needs.
2.4 The Process of Vulnerability Assessment
Conducting a Vulnerability Assessment involves several key steps:
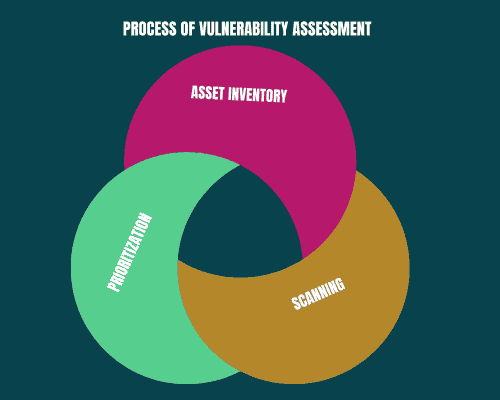
- Asset Inventory: Identify all devices, applications, and data assets in your environment. This step is crucial for understanding what needs to be assessed.
- Scanning: Utilize automated tools to examine the identified assets for any existing vulnerabilities. This process helps uncover potential weaknesses that may not be apparent through manual inspection.
- Prioritization: Once vulnerabilities are identified, prioritize them based on their severity and potential impact on your organization. Prioritize tackling high-risk vulnerabilities to effectively reduce the most pressing threats.
3. Steps to Conduct an Effective Vulnerability Assessment
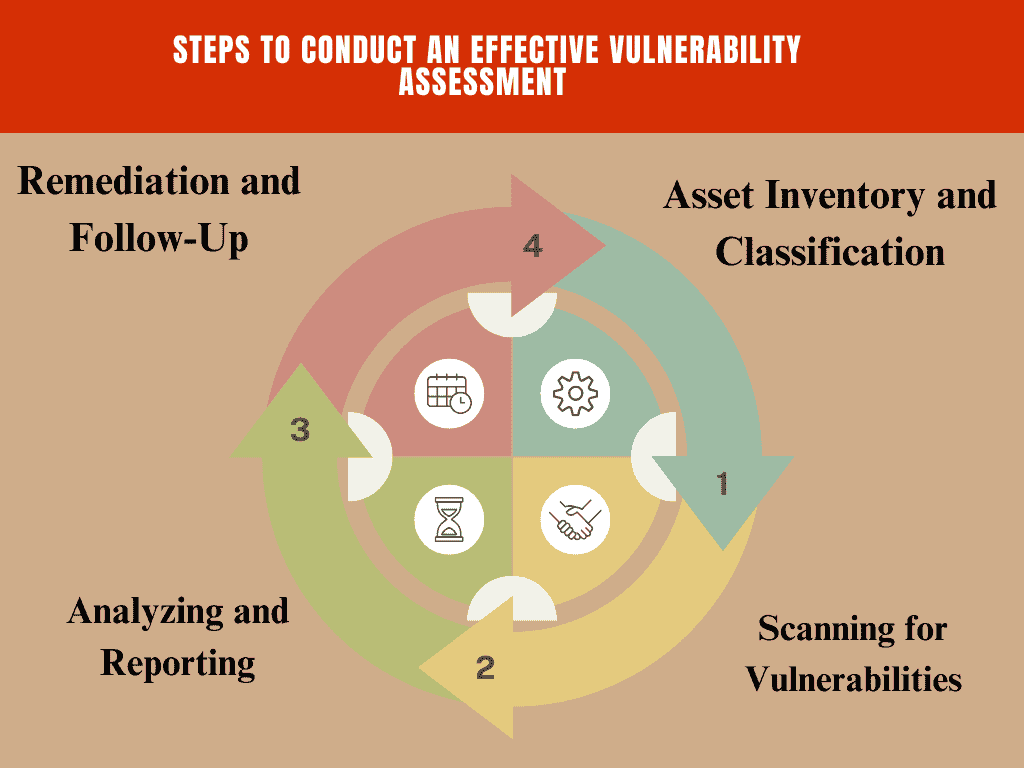
3.1 Step 1: Asset Inventory and Classification
The first step in any Vulnerability Assessment is to create an inventory of all assets within your organization. This includes hardware (servers, routers, switches), software applications, databases, and even physical locations. Understanding your assets will help you focus your assessment efforts where they matter most.
3.2 Step 2: Scanning for Vulnerabilities
After compiling an inventory, it’s time to scan your systems. Use tools like Nessus or OpenVAS to perform automated scans. These tools will check for known vulnerabilities and provide a report detailing the weaknesses discovered.
In addition to automated scanning, manual checks are vital. Review configuration settings, ensure strong password policies are in place, and examine logs for unusual activity. Manual checks can often uncover issues that automated tools might miss.
3.3 Step 3: Analyzing and Reporting
Once the scanning is complete, analyze the results. Classify vulnerabilities according to their severity and possible consequences. Create a detailed report that outlines the vulnerabilities, their risks, and recommended remediation steps. This report is essential for communicating findings to stakeholders and guiding remediation efforts.
3.4 Step 4: Remediation and Follow-Up
Address the identified vulnerabilities promptly. Develop a remediation plan that prioritizes fixing the most critical vulnerabilities first. After remediation, conduct follow-up assessments to ensure that vulnerabilities have been successfully addressed and that new ones have not emerged.
4. An Overview of Penetration Testing
4.1 What is Penetration Testing?
Penetration Testing is an authorized simulated attack on a system to evaluate its security. Unlike Vulnerability Assessments, which identify weaknesses, Pen Testing attempts to exploit those weaknesses to determine how far an attacker could penetrate your defenses.
4.2 Goals of Penetration Testing
The primary goal of Pen Testing is to identify vulnerabilities that could be exploited by malicious actors. This proactive approach helps organizations understand their security posture better and improve their defenses against real-world attacks.
4.3 Types of Penetration Tests
- Network Penetration Testing: Focuses on identifying vulnerabilities within the network infrastructure, such as firewalls, routers, and switches.
- Web Application Testing: Targets web applications to find vulnerabilities like SQL injection, XSS, and insecure APIs.
- Social Engineering: Tests how susceptible an organization is to social engineering attacks, such as phishing and pretexting. This type of testing evaluates employee awareness and response to potential threats.
4.4 Key Differences Between VA and Pen Testing
While both processes aim to enhance security, they have different methodologies and outcomes. A Vulnerability Assessment provides a broad view of potential weaknesses, while Penetration Testing offers in-depth insights into how those weaknesses can be exploited. Both methods are essential for a thorough security strategy.
5. The Penetration Testing Process
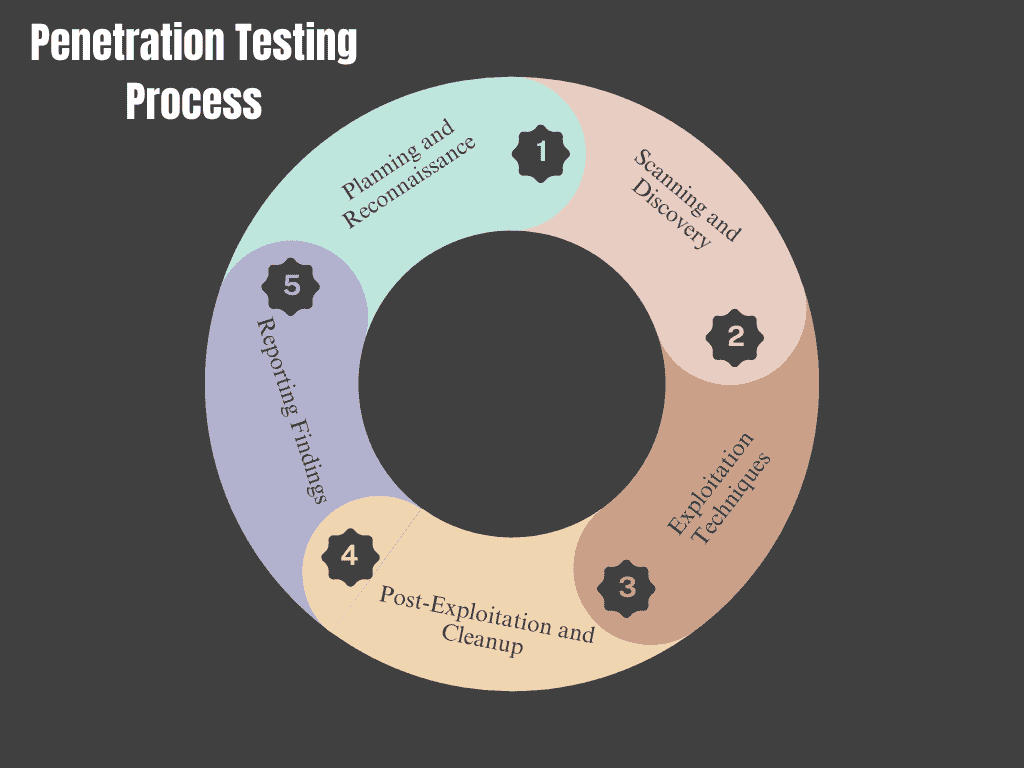
5.1: Planning and Reconnaissance
The initial stage of Penetration Testing consists of collecting data regarding the target system. This step, known as reconnaissance, helps testers understand the architecture and identify potential entry points. Tools like Nmap can be used to scan for open ports and active services.
5.2: Scanning and Discovery
Once information has been gathered, the next step is to perform active scans on the target system. This phase helps identify live systems, open ports, and running services. Understanding the attack surface is crucial for planning the next steps.
5.3: Exploitation Techniques
During this stage, testers try to take advantage of the vulnerabilities that have been identified. This could involve using tools like Metasploit to gain unauthorized access or test how far they can penetrate the system. The goal is to assess the potential damage a real attacker could inflict.
5.4: Post-Exploitation and Cleanup
After successfully exploiting vulnerabilities, testers will gather evidence of their findings and document the process. It’s essential to remove any access points created during testing and ensure that no changes have left the system vulnerable. This step helps maintain the integrity of the system and prevents unauthorized access after testing.
5.5 Reporting Findings
Finally, a comprehensive report should detail the testing process, findings, and recommendations for remediation. This report is vital for informing stakeholders and guiding future security measures.
6. VA & Pen Testing Tools and Technologies
6.1 Vulnerability Assessment Tools
- Nessus: A widely-used vulnerability scanner that helps identify potential security risks in systems and applications.
- OpenVAS: An open-source tool that offers powerful scanning capabilities for detecting vulnerabilities in various environments.
- QualysGuard: A cloud-based solution providing comprehensive vulnerability management, including continuous monitoring and reporting features.
6.2 Penetration Testing Tools
- Metasploit: A powerful framework for developing and executing exploit code against remote target machines.
- Burp Suite: A popular tool for web application security testing, allowing testers to identify vulnerabilities in web applications effectively.
- Nmap: A network discovery and security auditing tool used for scanning networks and identifying hosts and services.
6.3 Automated vs. Manual Testing
While automated tools can save time and provide broad coverage, manual testing is crucial for detecting complex vulnerabilities. Both approaches should be used in tandem for a comprehensive security evaluation.
7. Analyzing and Documenting Findings
7.1 Writing an Effective VA & Pen Testing Report
An effective report should be clear, concise, and actionable. Start with an executive summary that outlines the key findings and recommendations. Use straightforward language to ensure stakeholders can understand the results.
Key Components of the Report
- Executive Summary: A high-level overview of the assessment’s objectives and key findings.
- Methodology: A description of the testing approach and tools used.
- Findings: Detailed information on identified vulnerabilities, their severity, and potential impact.
- Recommendations: Actionable steps for remediation, prioritized by risk level.
7.2 Presenting Results to Stakeholders
Presenting findings to stakeholders is crucial for ensuring buy-in for remediation efforts. Use visuals, such as graphs and charts, to illustrate vulnerabilities and potential risks. Clearly communicate the importance of addressing identified issues and the potential impact on the organization.
8. Remediation Strategies
8.1 Closing Security Gaps and Fixing Vulnerabilities
Once vulnerabilities have been identified through assessments and testing, organizations must take action to remediate these issues. This step is crucial for improving overall security posture and minimizing the risk of exploitation.
Prioritizing Vulnerabilities
Begin by prioritizing the vulnerabilities based on their risk level. High-severity vulnerabilities that could lead to significant data breaches or system compromise should be addressed first. Use a risk management framework to categorize vulnerabilities based on factors such as:
- Impact: What would happen if the vulnerability were exploited?
- Likelihood: How probable is it that the vulnerability will be exploited?
- Exposure: How exposed is the system to potential threats?
Remediation Steps
- Patching: Make sure all software and systems are updated with the latest security patches. Regular patch management is essential for addressing vulnerabilities before they can be exploited.
- Configuration Changes: Review and modify system configurations to enhance security. Disable unnecessary services, change default passwords and implement strong authentication methods.
- Access Control: Implement strict access controls to limit who can access sensitive data and systems. Use the principle of least privilege (PoLP) to ensure that users have only the permissions they need to perform their jobs.
- Training and Awareness: Conduct regular training sessions for employees to raise awareness about security best practices and common threats, such as phishing attacks. Educated employees are your first line of defense against many cyber threats.
8.2 Best Practices for Patching and System Hardening
Developing a robust patch management strategy is essential. Establish a routine schedule for checking for updates and applying patches promptly. Additionally, consider implementing system hardening techniques, which involve reducing the system’s attack surface by minimizing the software installed, disabling unnecessary services, and configuring security settings to the most secure options.

8.3 Regular Assessments
Cybersecurity is an ongoing process, not a one-time task. Schedule regular vulnerability assessments and penetration tests to identify new vulnerabilities and validate that previous remediation efforts were successful. Ongoing improvement is essential for sustaining a robust security posture.
9. Legal and Ethical Considerations
When conducting Vulnerability Assessments and Penetration Testing, it is crucial to understand the legal implications. Unauthorized testing can lead to severe consequences, including legal action and financial penalties. Therefore, organizations must ensure they have permission before conducting any tests.
Regulatory Standards and Compliance
Many industries are governed by strict regulatory standards that mandate regular security assessments. For example:
- Payment Card Industry Data Security Standard (PCI-DSS) requires organizations that handle credit card information to perform vulnerability scans regularly.
- Health Insurance Portability and Accountability Act (HIPAA) outlines security requirements for protecting patient information in healthcare.
Organizations must ensure they comply with these regulations to avoid legal repercussions and protect sensitive data.
9.2 Ethical Hacking and Responsible Disclosure
Penetration testers must adhere to ethical guidelines to ensure their work is responsible and does not cause harm. This includes:
- Getting Authorization: Always obtain written consent from stakeholders before conducting tests.
- Limiting Scope: Clearly define the scope of testing to avoid unintended consequences.
- Responsible Disclosure: If vulnerabilities are discovered during testing, they should be reported to the organization promptly and not disclosed publicly until remediation is complete.
10. Advanced Concepts in VA & Pen Testing
10.1 Red Team vs. Blue Team Exercises
Red Team and Blue Team exercises simulate real-world attacks to improve security defenses.
- Red Team: This group acts as the attacker, employing tactics, techniques, and procedures (TTPs) to exploit vulnerabilities and breach security measures.
- Blue Team: The Blue Team is responsible for defending against these attacks. They analyze the Red Team’s techniques, improve security protocols, and develop incident response strategies.
These exercises provide invaluable insights into the effectiveness of security measures and help organizations prepare for actual cyber threats.
10.2 Continuous Monitoring and Threat Intelligence
Implementing continuous monitoring of networks and systems is crucial for early threat detection. Automated tools can help identify unusual behavior or indicators of compromise (IOCs).
Moreover, integrating threat intelligence into your security strategy can enhance your ability to defend against new threats. By staying informed about emerging threats and vulnerabilities, organizations can proactively adjust their defenses to mitigate risks.
11. Best Practices for Successful VA & Pen Testing
11.1 Creating a Robust Testing Schedule
To maximize the effectiveness of Vulnerability Assessments and Penetration Testing, organizations should establish a regular testing schedule. Depending on the organization’s size and risk profile, consider conducting assessments quarterly or bi-annually. Additionally, perform assessments after significant changes to the infrastructure or when new applications are deployed.
11.2 Ongoing Training and Skill Development
Cybersecurity is a rapidly evolving field. To stay ahead of potential threats, invest in ongoing training for your cybersecurity team. Encourage them to pursue certifications such as Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP) to enhance their skills.
11.3 Integrating VA & Pen Testing into a Security Framework
VA and Pen Testing should be integral components of your overall security strategy. By regularly assessing vulnerabilities and testing defenses, organizations can create a proactive security posture that reduces the likelihood of successful attacks.
12 Differences between Vulnerability Assessment and Penetration Testing
| Criteria | Vulnerability Assessment | Penetration Testing |
|---|
| Objective | Identify and evaluate security weaknesses in systems. | Simulate real-world attacks to exploit vulnerabilities. |
| Approach | Automated scanning and manual checks to find vulnerabilities. | Hands-on testing to determine how far an attacker can penetrate. |
| Outcome | A comprehensive report listing vulnerabilities and their severity. | A detailed report on exploited vulnerabilities and the potential impact. |
| Frequency | Regular assessments (e.g., quarterly or bi-annually). | Conducted periodically or after significant changes in the system. |
| Tools | Tools like Nessus, OpenVAS, and QualysGuard are commonly used. | Tools like Metasploit, Burp Suite, and Nmap are used for testing. |
| Depth of Testing | Broad coverage of potential vulnerabilities. | In-depth exploration of specific vulnerabilities. |
| Risk Level | Generally lower risk as it does not involve exploitation. | Higher risk as it involves attempting to breach security defenses. |
| Skills Required | Primarily requires knowledge of security tools and vulnerability management. | Requires skills in ethical hacking and knowledge of exploitation techniques. |
13 FAQs
1: What is the difference between Vulnerability Assessment and Penetration Testing?
Answer:
Vulnerability Assessment involves identifying and prioritizing vulnerabilities in systems, applications, and networks. It focuses on scanning and analyzing potential weaknesses without attempting to exploit them. In contrast, Penetration Testing simulates real-world attacks to exploit identified vulnerabilities, assessing how deep an attacker could penetrate your systems. Both practices are essential for a comprehensive cybersecurity strategy.
2: How often should organizations conduct Vulnerability Assessments and Penetration Testing?
Answer:
Organizations should conduct Vulnerability Assessments at least quarterly or bi-annually, depending on their size and risk profile. Penetration Testing should be performed periodically, particularly after significant changes in the IT environment or the introduction of new applications. Continuous monitoring and assessments are recommended to adapt to evolving threats.
3: Are Vulnerability Assessment and Penetration Testing legally required?
Answer:
While not universally mandated, many industries have regulations that require organizations to perform regular security assessments. For instance, standards like PCI-DSS for payment card data and HIPAA for healthcare data require vulnerability assessments. Organizations should understand their specific regulatory obligations and best practices for maintaining compliance.
4: What tools are commonly used for Vulnerability Assessment and Penetration Testing?
Answer:
Common tools for Vulnerability Assessment include Nessus, OpenVAS, and QualysGuard, which help identify potential security risks. For Penetration Testing, tools like Metasploit, Burp Suite, and Nmap are frequently used to exploit vulnerabilities and assess the effectiveness of security measures.
5: How can organizations ensure the effectiveness of their Vulnerability Assessment and Penetration Testing?
Answer:
To ensure effectiveness, organizations should establish a comprehensive testing strategy that includes regular assessments, proper scoping, and adherence to legal and ethical guidelines. Involving skilled professionals and continually updating methodologies based on emerging threats and vulnerabilities is crucial. Additionally, prioritizing findings for remediation and conducting follow-up tests will help maintain a strong security posture.
14 Conclusion
Conclusion
In today’s digital landscape, Vulnerability Assessment and Penetration Testing are essential for maintaining strong cybersecurity. These practices help organizations identify and remediate security weaknesses before they can be exploited. By regularly assessing vulnerabilities and simulating real-world attacks, businesses can significantly reduce the risk of cyber threats. Integrating both practices into a comprehensive security strategy ensures ongoing monitoring and improvement, aligning with industry regulations. Additionally, fostering a culture of security awareness among employees is crucial for enhancing overall defense. Ultimately, prioritizing Vulnerability Assessment and Penetration Testing is vital for protecting sensitive information and maintaining trust with clients and stakeholders in an ever-evolving threat environment.
