1: Introduction to Vulnerability Assessment
Vulnerability assessment is the process of identifying, quantifying, and prioritizing security vulnerabilities within an IT infrastructure. This proactive approach helps organizations understand their security weaknesses and take the necessary steps to address them, thereby protecting sensitive data, maintaining user trust, and ensuring the continuity of business operations.
Definition and Importance
Vulnerability assessments are crucial in today’s digital age where cyber threats are constantly evolving. By identifying potential vulnerabilities before attackers can exploit them, organizations can prevent data breaches, service disruptions, and potential financial losses. Whether for small businesses or large enterprises, vulnerability assessments are a foundational element of cybersecurity strategies.

Key Objectives of Vulnerability Assessment
The main objectives of a vulnerability assessment include:
- Identifying Weak Points: Locating security flaws in hardware, software, and system configurations.
- Evaluating Risk: Understanding the potential impact and likelihood of vulnerabilities being exploited.
- Prioritizing Remediation: Focusing on the most critical issues first to optimize resource allocation.
- Supporting Compliance: Ensuring adherence to industry standards and regulations like GDPR, HIPAA, and PCI-DSS.
- Enhancing Overall Security: Strengthening an organization’s security posture by addressing vulnerabilities before they become a risk.
By achieving these objectives, organizations can protect their assets, secure their data, and build resilience against cyber threats.
2: Types of Vulnerability Assessments
Understanding the different types of vulnerability assessments helps organizations select the best approach for their specific needs. Each type targets different areas of an IT environment to ensure comprehensive coverage.
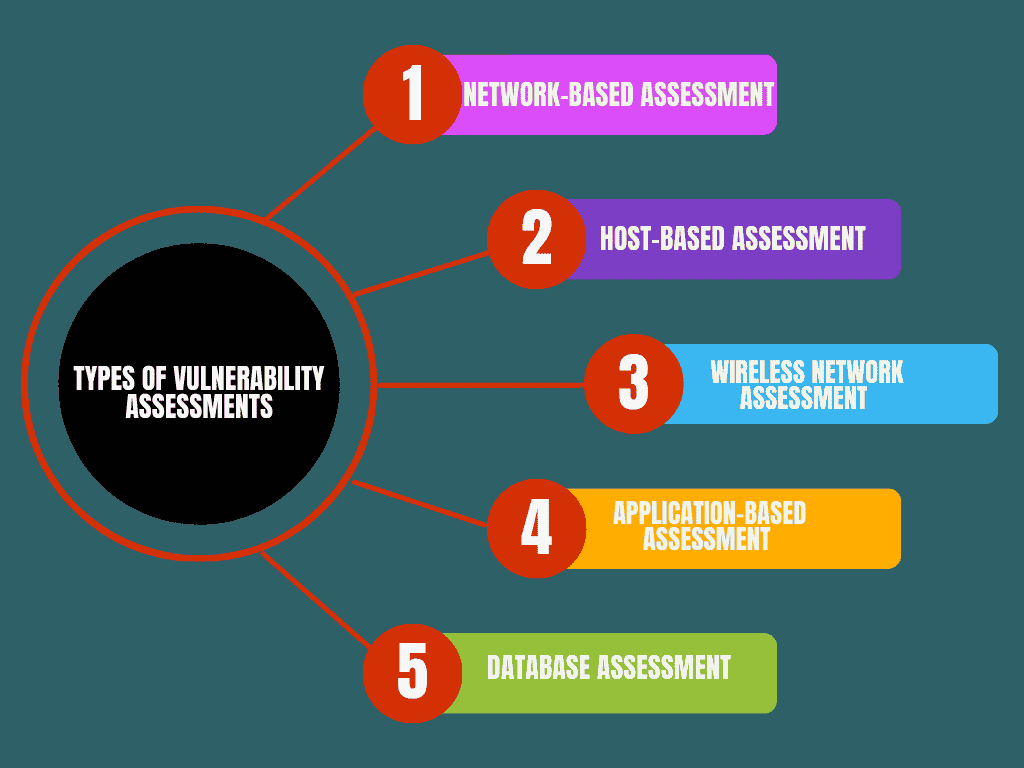
1 Network-Based Assessment
A network-based assessment involves scanning an organization’s internal and external networks to identify vulnerabilities that attackers could potentially exploit. This type of assessment helps detect open ports, outdated protocols, and weak firewall configurations.
Benefits:
- Enhances network security by uncovering misconfigurations and outdated software.
- Identifies potential entry points for unauthorized access.
- Strengthens the perimeter defense of the organization.
Common Tools:
- Nmap: An open-source network scanning tool known for its flexibility and power.
- Nessus: A widely used tool that provides comprehensive network vulnerability scanning capabilities.
2 Host-Based Assessment
Host-based assessments focus on individual devices, such as servers, computers, and workstations. These assessments involve reviewing system configurations, installed software, and user permissions to identify potential vulnerabilities within each device.
Advantages:
- Detects vulnerabilities at the device level that could be exploited locally or remotely.
- Verifies that systems are up-to-date with patches and security updates.
- Identifies misconfigured permissions and inappropriate user privileges.
Recommended Tools:
- OSSEC: An open-source host-based intrusion detection system.
- Tripwire: A tool for monitoring and auditing changes to system files and configurations.
3 Wireless Network Assessment
Wireless network assessments evaluate the security of wireless connections to ensure they are protected against unauthorized access and eavesdropping. These assessments check the strength of encryption, network protocols, and overall network configuration.
Why They Matter:
- Protects wireless networks from interception and unauthorized access.
- Helps ensure robust encryption standards are in place.
- Identifies weak passwords and misconfigured access points.
Tools:
- Aircrack-ng: A widely used suite for assessing wireless network security.
- Kismet: A tool for wireless network detection and analysis.
4 Application-Based Assessment
Applications, whether web-based or mobile, can contain vulnerabilities that expose an organization to risk. Application-based assessments look for common issues such as SQL injection, cross-site scripting (XSS), and broken authentication mechanisms.
Key Benefits:
- Helps ensure applications are secure and adhere to best coding practices.
- Detects weaknesses that may result in data breaches or unauthorized access.
- Provides insights into the secure development of future applications.
Common Tools:
- OWASP ZAP: An open-source web application security scanner.
- Burp Suite: A comprehensive tool for finding vulnerabilities in web applications.
5 Database Assessment
Databases hold critical and sensitive information, making them a prime target for attackers. Database assessments focus on identifying vulnerabilities such as unpatched software, weak access controls, and misconfigured permissions.
Why Database Assessments Are Crucial:
- Protects confidential data from unauthorized access and possible security breaches.
- Ensures that database systems have proper access controls and encryption settings.
- Identifies out-of-date software and patches to reduce risk.
Recommended Tools:
- SQLmap: SQLmap is an automated tool designed to identify and exploit SQL injection vulnerabilities. It assists in detecting security flaws in web applications by thoroughly scanning and analyzing databases for potential breaches, offering detailed insights for exploitation and penetration testing.
- DBProtect: A solution for comprehensive database security.
3: Phases of Vulnerability Assessment Methodology
Conducting a thorough vulnerability assessment involves multiple phases, each essential for ensuring a comprehensive review.
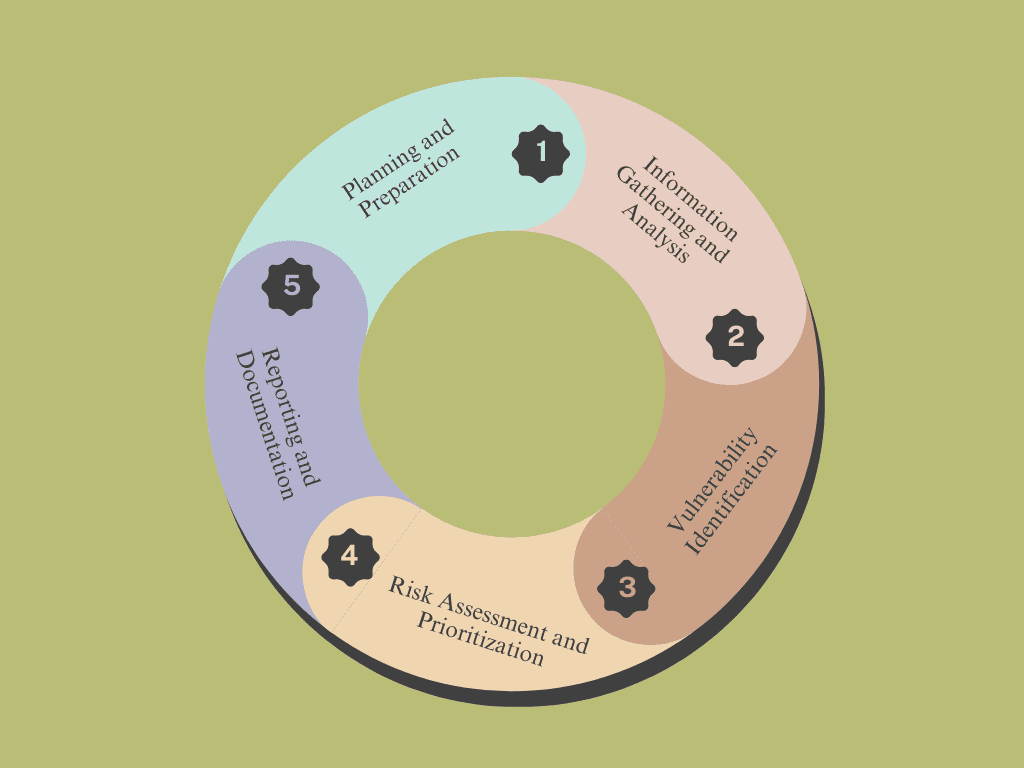
1 Planning and Preparation
Before beginning an assessment, it’s vital to set clear objectives, define the scope, and obtain necessary permissions. This phase lays the groundwork for a successful and efficient assessment.
Steps:
- Define Scope: Determine which systems and networks will be assessed.
- Set Objectives: Clarify the goals, such as identifying misconfigurations or outdated software.
- Assemble Resources: Ensure the right tools and personnel are available.
- Gain Approval: Secure all necessary legal agreements and permissions.
2 Information Gathering and Analysis
Gathering data about the system being assessed is crucial for understanding its structure and identifying vulnerabilities effectively. This step involves:
- Reviewing network diagrams and system architecture.
- Collecting details about operating systems, installed software, and user roles.
- Performing initial scans to establish a baseline understanding.
3 Vulnerability Identification
In this phase, various tools and manual techniques are employed to uncover vulnerabilities. Automated tools provide a broad sweep, while manual inspections are valuable for identifying unique or more complex vulnerabilities.
4 Risk Assessment and Prioritization
Each identified vulnerability should be assessed for its risk level, which combines the potential impact and likelihood of exploitation. This aids in prioritizing vulnerabilities that require urgent attention.
Risk Assessment Factors:
- Impact: The damage that could occur if exploited.
- Likelihood: The chance of the vulnerability being exploited.
5 Reporting and Documentation
A detailed report is created to summarize findings, risk levels, and recommended mitigation steps. The report should be straightforward, brief, and actionable.
Elements to Include:
- Executive Summary: Key takeaways for decision-makers.
- Detailed Findings: In-depth analysis of vulnerabilities.
- Recommendations: Steps for addressing the vulnerabilities.
4: Tools and Techniques for Vulnerability Assessment
Effective vulnerability assessment relies heavily on the tools and techniques used to identify and analyze vulnerabilities.
Popular Vulnerability Scanning Tools
Nessus, OpenVAS, and QualysGuard are among the most popular tools. Each offers unique features and benefits tailored for different assessment needs.
Manual vs. Automated Assessments
Automated tools are efficient for detecting known vulnerabilities quickly. However, manual assessments are important to uncover more nuanced security issues that automated tools might overlook.
Best Practices for Tool Utilization
- Update Tools Regularly: Ensure tools are updated to identify the latest vulnerabilities.
- Combine Approaches: Use both automated tools and manual inspection for comprehensive coverage.
- Document Results: Keep records of scans and findings for future reference.
5: Conducting an Effective Vulnerability Assessment
A successful vulnerability assessment is more than running a scan; it involves a systematic approach.
Step-by-Step Process
- Define Objectives and Scope: Outline what the assessment aims to achieve and the systems involved.
- Collect Data: Gather information on system components, software, and users.
- Perform the Assessment: Use a mix of automated tools and manual checks.
- Analyze Results: Check for false positives and validate findings.
- Document Findings: Create a comprehensive report with details on vulnerabilities and recommended fixes.
Challenges and Solutions
False Positives: Verify flagged issues manually to confirm their legitimacy.
New Threats: Keep up with cybersecurity news and update tools regularly to adapt to emerging threats.
Complex Environments: Break down assessments into manageable sections for large, complex systems
6: Risk Analysis and Prioritization Strategies
Risk analysis helps determine which vulnerabilities to address first. It evaluates the potential impact and the likelihood of a vulnerability being exploited.
Evaluating Risk Impact and Likelihood
- Impact: Consider the consequences of an exploited vulnerability. Could it lead to data loss or service interruption?
- Likelihood: Assess how easy it is for an attacker to exploit the vulnerability.
Assigning Severity Levels
Use severity levels like critical, high, medium, and low to rank vulnerabilities:
- Critical: Needs immediate action.
- High: Important and should be addressed soon.
- Medium: Can wait until more critical issues are resolved.
- Low: Minimal threat but should still be fixed over time.
7: Reporting and Documenting Findings
A detailed, clear report is crucial to communicate the results of a vulnerability assessment effectively.
Structuring the Report
Include:
- Executive Summary: A snapshot of findings for non-technical stakeholders.
- Detailed Analysis: Technical explanations for IT teams.
- Recommendations: Practical steps for addressing vulnerabilities.
Tips for Effective Communication
- Use plain language for non-experts.
- Include visuals like charts and graphs.
- Highlight urgent vulnerabilities and recommended fixes for easy action.
8: Mitigation and Remediation Techniques
Mitigation and remediation are essential for reducing or removing identified risks.
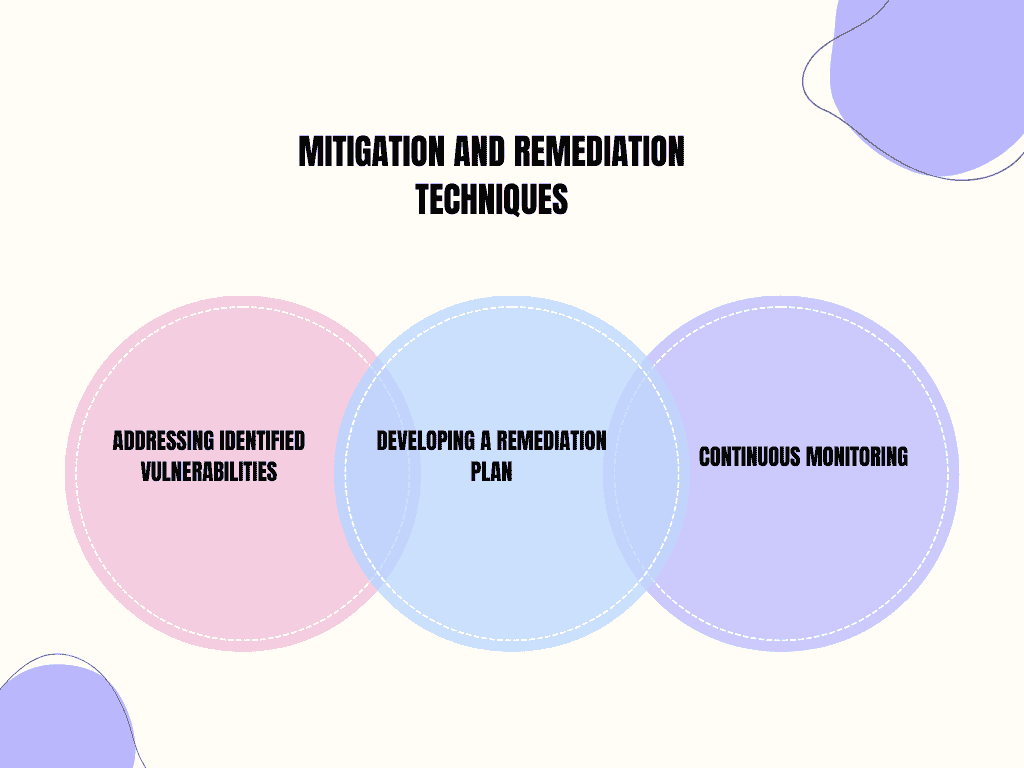
1 Addressing Identified Vulnerabilities
- Patch Management: Apply updates to fix known vulnerabilities.
- Configuration Adjustments: Modify system settings to remove security gaps.
- Access Controls: Limit access rights to critical data and systems.
2 Developing a Remediation Plan
Create a structured plan that outlines:
- Priorities: Tackle the most severe vulnerabilities first.
- Responsibilities: Assign tasks to appropriate team members.
- Deadlines: Set clear timelines for completion.
3 Continuous Monitoring
Keep monitoring systems regularly to catch any new vulnerabilities that may arise and confirm previous fixes are still effective.
9: Best Practices for Ongoing Vulnerability Management
Maintaining strong cybersecurity requires consistent effort. Vulnerability management isn’t a one-time project but an ongoing process that needs to adapt as new threats emerge and technology evolves. Implementing best practices for continuous management helps ensure that an organization’s security posture remains effective over time.
Implementing a Routine Assessment Schedule
Regular assessments are essential to identify and address vulnerabilities as they arise. Here’s how to establish an effective schedule:
- Regular Assessments: Conduct vulnerability assessments at least quarterly. This helps organizations stay proactive in identifying potential security risks before they can be exploited.
- After Major Changes: Run assessments whenever significant updates or changes occur in the IT infrastructure, such as installing new software, upgrading hardware, or integrating new systems.
- Compliance Requirements: Align assessment frequency with any regulatory standards that apply to the organization, such as GDPR or PCI-DSS.
Staying Informed About Emerging Threats
Cyber threats evolve rapidly, making it essential to stay informed and up-to-date:
- Follow Trusted Sources: Subscribe to cybersecurity bulletins from reliable organizations such as OWASP and NIST. These sources provide updates on new vulnerabilities, best practices, and industry trends.
- Security Alerts and News: Keep track of new threats by following cybersecurity news outlets and threat intelligence platforms.
- Regular Training: Invest in ongoing training and certification programs for IT and security teams to ensure they are aware of the latest attack methods and defensive strategies.

Maintaining Clear Documentation
Documenting each vulnerability assessment and its findings is critical for future reference and audits:
- Assessment Records: Keep detailed records of each assessment, including the tools used, vulnerabilities found, and steps taken to address them.
- Action Logs: Maintain logs that track who is responsible for specific remediation tasks and the completion status of each.
- Audit Preparation: Comprehensive documentation is invaluable during external audits and for meeting compliance requirements.
Automating Where Possible
Automation can significantly enhance the efficiency of ongoing vulnerability management:
- Use Automated Tools: Implement tools that provide continuous monitoring and real-time vulnerability detection. Automated tools can quickly scan and flag potential security issues without requiring constant manual input.
- Integrate with SIEM Systems: Security Information and Event Management (SIEM) systems can provide centralized visibility of security data, helping identify and respond to vulnerabilities more effectively.
- Patch Management Automation: Use tools that automate patch deployment to keep systems up-to-date with the latest security patches and updates.
Building a Security Culture
Cybersecurity isn’t just the responsibility of the IT department; it’s an organization-wide effort. Creating a culture of security awareness among all employees can greatly reduce the risk of security incidents.
- Training Programs: Regularly train employees on best practices for cybersecurity, including how to recognize phishing attempts and avoid risky online behavior.
- Clear Policies: Develop and enforce clear policies for password management, data handling, and acceptable use of company resources.
- Encourage Reporting: Create a safe and straightforward way for employees to report any suspicious activities or potential vulnerabilities they encounter.
Continuous Improvement and Adaptation
Ongoing vulnerability management must evolve to meet new challenges:
- Regular Policy Review: Periodically review and update security policies to ensure they remain effective against current threats.
- Feedback Loop: After each assessment and remediation cycle, gather feedback on what worked well and what could be improved. Use this feedback to refine the process for the future.
- Adapt to New Technologies: As new technologies are adopted, ensure that the organization’s vulnerability management practices adapt to include these new elements in assessments.
Leveraging Third-Party Expertise
Sometimes, in-house teams may not have the capacity or expertise needed for comprehensive vulnerability management:
- Consultants and Managed Services: Engage with cybersecurity consultants or managed security service providers (MSSPs) to bolster your team’s efforts, especially for specialized assessments or complex environments.
- Penetration Testing: Conduct periodic penetration tests by third-party experts to simulate real-world attacks and identify vulnerabilities that may not have been caught by standard assessments.
Measuring Success
It’s important to track the effectiveness of your ongoing vulnerability management efforts:
- Metrics and KPIs: Use key performance indicators (KPIs) such as the number of vulnerabilities detected, average time to remediation, and the severity of vulnerabilities fixed.
- Reports and Dashboards: Use tools that can generate reports and dashboards for easy visualization of progress and ongoing risks.
- Regular Review Meetings: Hold regular meetings with stakeholders to discuss findings, current vulnerabilities, and improvements to the process.

Best Practices Summary
- Conduct regular and post-change assessments to keep security measures current.
- Stay updated with industry trends through trusted sources and security alerts.
- Document everything, from vulnerabilities found to steps taken for remediation.
- Leverage automation for continuous monitoring and patch management.
- Foster a culture of security with ongoing training and clear policies.
- Adapt and improve processes based on feedback and new technologies.
- Use external expertise for advanced testing and additional support.
- Measure success through metrics and regular review sessions.
By following these best practices, organizations can establish a robust and proactive approach to vulnerability management, ensuring long-term security and resilience against evolving cyber threats.
10 Differences between Network-Based Assessments and Host-Based Assessments
| Aspect | Network-Based Assessments | Host-Based Assessments |
|---|
| Focus | Scans entire networks, including external and internal | Examines individual devices like servers and workstations |
| Detection | Identifies open ports, protocols, and firewall issues | Finds vulnerabilities in system configurations and installed software |
| Scope | Broader, covering multiple devices at once | Narrower, focused on a single device or endpoint |
| Setup Complexity | Easier to configure for large-scale network scans | More complex, requires detailed configuration for each device |
| Resource Usage | Can be resource-intensive, depending on network size | Uses fewer resources but requires more time per device |
| Depth of Analysis | Provides a general overview of network vulnerabilities | Offers a deeper, more specific analysis of a device’s security |
| Common Tools | Nmap, Nessus | OSSEC, Tripwire |
| Best For | Identifying network-level security weaknesses | Analyzing critical devices and system-specific vulnerabilities |
11 FAQS
Here are 5 FAQs related to vulnerability assessment:
1. What is the main goal of a vulnerability assessment?
The main goal of a vulnerability assessment is to identify, evaluate, and prioritize security vulnerabilities within an organization’s IT environment. This helps prevent data breaches, protect sensitive information, and maintain compliance with industry regulations.
2. How often should vulnerability assessments be conducted?
Vulnerability assessments should be conducted at least quarterly or whenever there are significant changes in the IT infrastructure, such as system updates, new software installations, or major network modifications. Regular assessments help keep security measures up-to-date and effective.
3. What is the difference between vulnerability assessment and penetration testing?
A vulnerability assessment focuses on identifying and reporting security weaknesses without exploiting them, while penetration testing involves actively exploiting vulnerabilities to understand their impact. Penetration testing provides deeper insights into real-world attack scenarios.
4. Can automated tools detect all types of vulnerabilities?
Automated tools are excellent for quickly identifying common, known vulnerabilities, but they may miss complex or less obvious issues. Manual assessments are recommended alongside automated scans for a more thorough evaluation.
5. What should be included in a vulnerability assessment report?
A vulnerability assessment report should include an executive summary, detailed findings with technical explanations, risk levels (e.g., critical, high, medium, low), and clear recommendations for remediation. Visual aids like charts and graphs can help make the information more accessible for stakeholders.
12 Conclusion
In conclusion, vulnerability assessments are essential for maintaining robust cybersecurity. By systematically identifying and addressing security weaknesses, organizations can protect sensitive data, ensure compliance with industry standards, and build resilience against evolving cyber threats. Implementing regular assessments, staying informed about emerging vulnerabilities, and fostering a culture of security awareness are key practices that contribute to a strong security posture. By integrating these strategies, organizations can proactively manage risks and safeguard their digital assets effectively.
