1. Network Vulnerability Assessment Overview
1.1 Definition and Importance
Network Vulnerability Assessment (NVA) is a systematic evaluation of a network’s security infrastructure. This assessment identifies, quantifies, and prioritizes vulnerabilities within a network. In today’s digital age, where cyber threats are increasing in sophistication, the importance of NVA cannot be overstated. Organizations store sensitive data, including personal information and financial records, which makes them prime targets for cybercriminals.
Conducting an NVA helps organizations understand their security posture and the effectiveness of existing security measures. It enables companies to proactively identify weaknesses before they can be exploited by attackers. Furthermore, regular assessments contribute to compliance with industry regulations, fostering trust with clients and stakeholders.
1.2 Core Objectives of Network Vulnerability Assessment
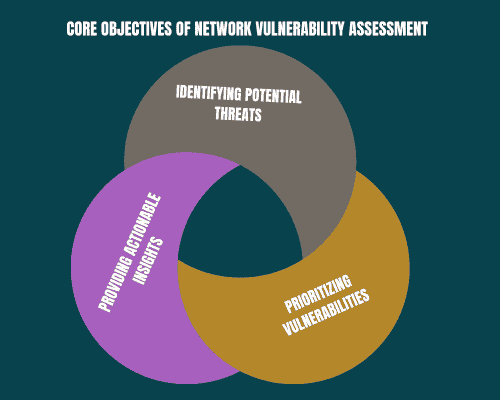
The core objectives of NVA include:
- Identifying Potential Threats: By assessing the network for vulnerabilities, organizations can identify threats that could compromise security. This includes understanding how different vulnerabilities could be exploited.
- Prioritizing Vulnerabilities: Not every vulnerability carries an equivalent degree of risk. NVA helps organizations prioritize these vulnerabilities based on their potential impact on business operations.
- Providing Actionable Insights: The ultimate goal of an NVA is to provide organizations with actionable insights. These insights guide decision-makers in developing strategies to mitigate identified risks effectively.
1.3 Role in Modern Cybersecurity
NVA is a foundational element of a comprehensive cybersecurity strategy. With the rise of remote work and cloud services, the attack surface has expanded significantly. NVA helps organizations adapt to this new landscape by identifying areas that require additional protection. Furthermore, it plays a crucial role in integrating security practices into the organization’s culture, ensuring that cybersecurity is a shared responsibility among all employees.
2. Understanding Network Vulnerabilities
2.1 Common Types of Network Vulnerabilities
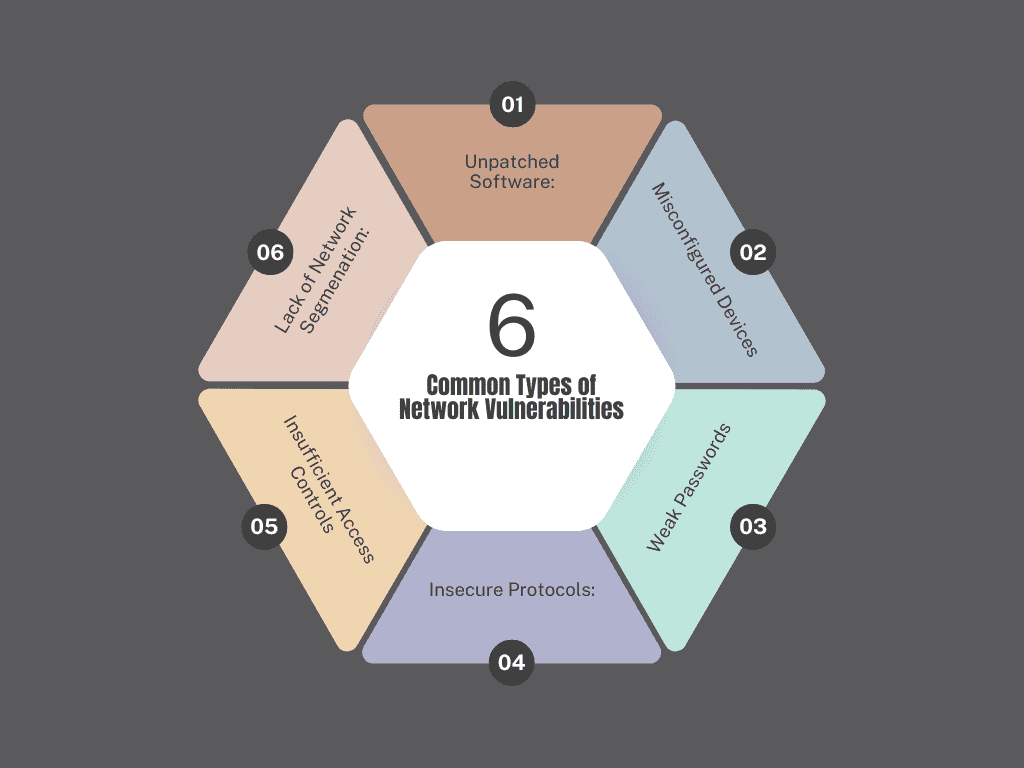
Network vulnerabilities can manifest in various forms, making them difficult to manage. Understanding these types is essential for effective risk mitigation. Some common types include:
1 Unpatched Software: Failure to apply security patches to software can leave systems exposed. Attackers often exploit known vulnerabilities that have not been addressed, leading to data breaches or system compromise.
2 Misconfigured Devices: Network devices, such as routers and firewalls, must be configured correctly. Misconfigurations can create entry points for attackers, allowing them to bypass security measures and gain unauthorized access to the network.
3 Weak Passwords: Using easily guessable passwords can lead to unauthorized access. Organizations should enforce strong password policies, including the use of complex passwords and regular updates, to reduce the risk of credential theft.
4 Insecure Protocols: The use of outdated or insecure communication protocols can expose data during transmission. Protocols like Telnet or FTP do not encrypt data, making it vulnerable to interception. Secure alternatives like SSH and HTTPS should be used instead.
5 Insufficient Access Controls: Inadequate access controls can allow unauthorized users to gain access to sensitive data or systems. Implementing the principle of least privilege ensures that users only have access to the resources necessary for their roles.
6 Lack of Network Segmentation: Failing to segment a network can allow attackers to move freely across the entire network once they gain access. Proper segmentation limits the spread of malware and restricts access to sensitive systems.
2.2 Software and Application Weaknesses
Software vulnerabilities frequently stem from coding mistakes or using outdated software. To reduce these vulnerabilities in applications, developers should implement secure coding techniques. Additionally, routine updates and patches are crucial for ensuring the security of applications. Additionally, organizations should conduct regular assessments of third-party applications to ensure they do not introduce vulnerabilities.
2.3 Operating System and Firmware Vulnerabilities
Operating systems and firmware require continuous monitoring and updates. Vulnerabilities in these areas can lead to severe security breaches. Organizations must have a strategy for regularly updating their operating systems and firmware, including implementing automated update processes wherever possible.
2.4 Network Configuration Flaws
Improperly configured network devices can create significant security gaps. Organizations should establish baseline configurations for all network devices and regularly review them for compliance. Implementing a configuration management process helps ensure that configurations remain secure over time.
3. Network Vulnerability Assessment Techniques
3.1 Manual vs. Automated Assessment Approaches

NVA techniques can be categorized into manual and automated assessments.
- Manual Assessments: These assessments involve security professionals performing hands-on evaluations. They provide detailed insights into vulnerabilities that automated tools might miss. However, manual assessments are time-consuming and may require specialized skills.
- Automated Assessments: Automated tools streamline the assessment process by scanning networks for known vulnerabilities. They are efficient but may overlook nuanced vulnerabilities. A combined approach, using both manual and automated methods, often yields the best results.
3.2 Internal vs. External Assessments
NVA can be conducted internally or externally.
- Internal Assessments: These focus on identifying vulnerabilities within the organization’s network. Internal assessments help uncover vulnerabilities that may not be visible from the outside.
- External Assessments: These evaluate the network’s exposure to outside threats. External assessments simulate attacks from an outsider’s perspective, identifying vulnerabilities that could be exploited by malicious actors.
3.3 Penetration Testing within Network Vulnerability Assessment
Penetration testing is a specialized form of NVA that simulates real-world attacks. It helps organizations identify vulnerabilities that standard assessments might miss. Penetration testing provides deeper insights into potential exploit paths and the effectiveness of existing security measures. Regular penetration tests can help organizations stay ahead of emerging threats.
4. Essential Tools for Network Vulnerability Assessment
4.1 Best Open-Source Tools
Open-source tools provide an excellent starting point for organizations looking to conduct vulnerability assessments without significant financial investment. Some popular open-source tools include:
- Nmap: A powerful network scanning tool that identifies devices on a network and their associated vulnerabilities.
- OpenVAS: A comprehensive vulnerability scanner that provides detailed reports on identified vulnerabilities.
- Wireshark: A network protocol analyzer that allows users to capture and analyze network traffic, helping identify unusual patterns or potential threats.
4.2 Leading Commercial Solutions
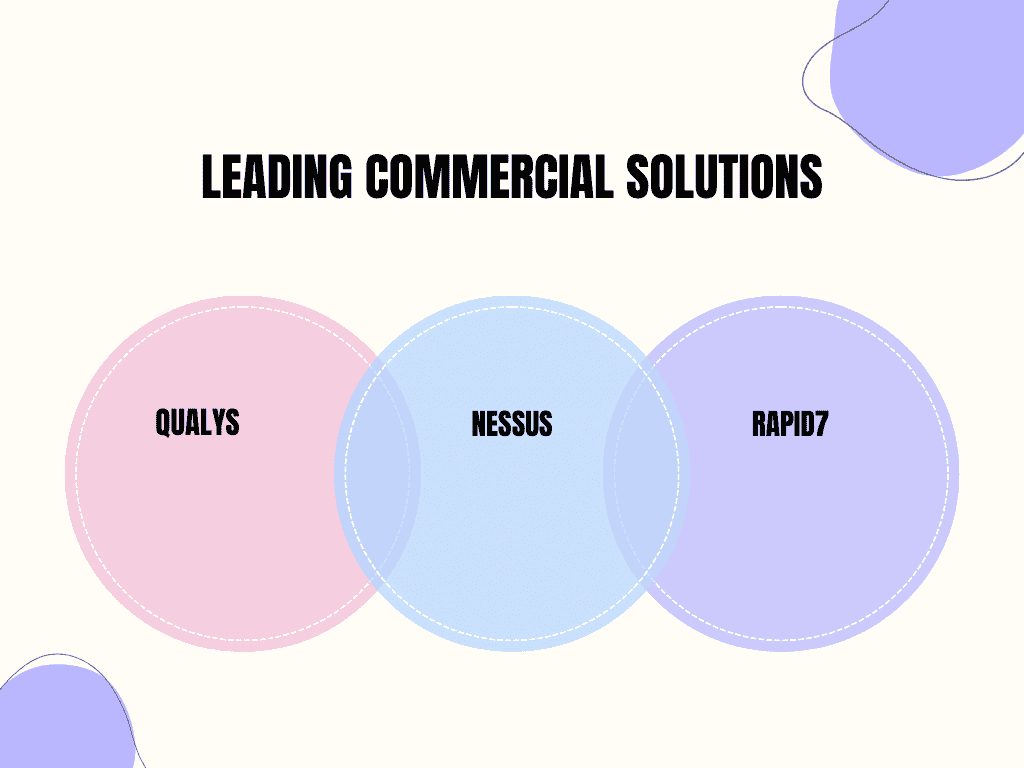
Commercial tools often offer more advanced features and customer support. Some leading solutions include:
- Qualys: A cloud-based vulnerability management solution that provides continuous monitoring and reporting.
- Nessus: A widely used vulnerability scanner known for its extensive plugin library and ease of use.
- Rapid7: Offers a suite of security solutions, including vulnerability management and incident response.
4.3 Tool Selection Guidelines for Effective Assessment
When selecting tools, consider factors such as the organization’s size, budget, specific requirements, and ease of integration with existing systems. It’s crucial to choose tools that align with the organization’s security goals and provide the necessary capabilities for effective assessments.
5. Preparing for a Network Vulnerability Assessment
5.1 Setting Goals and Scope
Before conducting an NVA, it’s essential to define clear goals and the scope of the assessment. Goals may include identifying specific vulnerabilities, testing the effectiveness of security controls, or complying with regulatory requirements. A well-defined scope helps focus the assessment on critical areas, ensuring efficient use of resources.
5.2 Identifying Critical Network Assets
Identifying critical network assets is vital for effective vulnerability management. Organizations should prioritize assets based on their importance to business operations and the sensitivity of the data they handle. This prioritization allows teams to allocate resources efficiently during assessments and remediation efforts.
5.3 Pre-Assessment Checklist and Planning
A pre-assessment checklist can streamline the preparation process. It should include items such as:
- Ensuring all necessary permissions are obtained.
- Gathering relevant documentation, including network diagrams and asset inventories.
- Communicating with stakeholders to set expectations regarding the assessment process.
6. Executing a Network Vulnerability Assessment
6.1 Step-by-Step Assessment Procedure
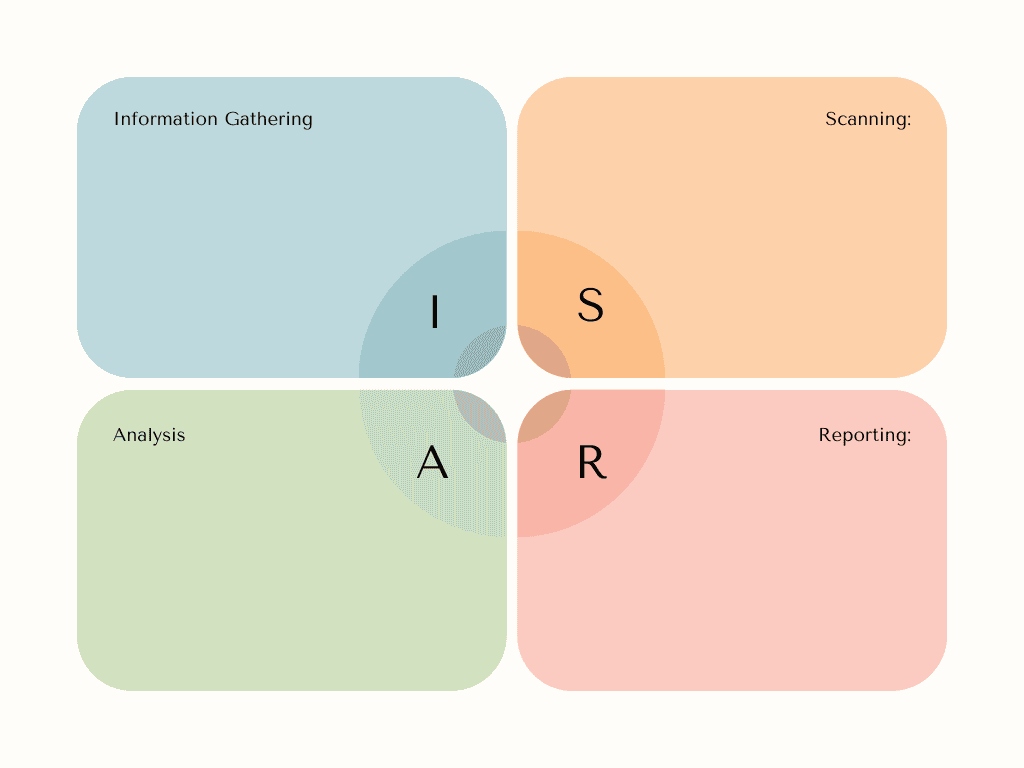
Executing an NVA involves a structured approach:
- Information Gathering: Collect data about the network, including IP addresses, operating systems, and software in use.
- Scanning: Use tools to scan for vulnerabilities across the network.
- Analysis: Evaluate the results to identify potential risks.
- Reporting: Document findings and provide actionable recommendations.
6.2 Collecting and Validating Data
Data collected during the assessment must be accurate and relevant. Use multiple sources of information to validate findings, ensuring that the assessment reflects the true state of the network’s security.
6.3 Ensuring Comprehensive Coverage
To achieve comprehensive coverage, utilize a variety of tools and techniques. This may include network scans, configuration reviews, and penetration tests. A holistic approach ensures that no vulnerabilities are overlooked.
7. Analyzing Results of a Network Vulnerability Assessment
7.1 Interpreting Findings
Interpreting the results requires an understanding of the context behind each vulnerability. Analyze the potential impact of each vulnerability on the organization’s operations, reputation, and compliance status.
7.2 Documenting Results for Stakeholders
What_is_RiskClear documentation is crucial for effective communication with stakeholders. Reports should be concise, highlighting key findings, risk levels, and recommended actions. Utilize visual tools like charts and graphs to improve comprehension.
7.3 Risk Prioritization and Management
Once vulnerabilities are identified, prioritize them based on their risk levels. High-risk vulnerabilities should be addressed immediately, while lower-risk issues can be scheduled for later remediation. This approach ensures that resources are allocated effectively and that the organization maintains a strong security posture.
8. Remediation and Mitigation Strategies
8.1 Applying Patches and Software Updates
One of the most effective ways to mitigate vulnerabilities is through regular patching and updates. Organizations should establish a schedule for applying patches and ensure that all software is kept up to date. This includes operating systems, applications, and third-party integrations.
8.2 Network Configuration Enhancements
Review and enhance network configurations to close security gaps. This may involve changing default settings, disabling unused services, and implementing access controls. Establish baseline configurations and regularly review them to ensure compliance with security best practices.
8.3 Long-Term Vulnerability Management Plans
Developing a long-term vulnerability management plan is essential for ongoing security. This plan should outline procedures for continuous monitoring, regular assessments, and incident response. By adopting a proactive approach, organizations can adapt to emerging threats and maintain a resilient security posture.
9. Maintaining Security Post-Assessment
9.1 Continuous Monitoring for Vulnerabilities
Implementing continuous monitoring solutions helps detect vulnerabilities in real-time. This includes using automated tools to scan for new vulnerabilities and monitoring network traffic for unusual patterns. Regular monitoring allows organizations to respond quickly to potential threats.
9.2 Implementing Ongoing Security Improvements
Organizations should regularly update security protocols and practices. This may involve adopting new technologies, revising policies, and providing ongoing training for employees. A culture of continuous improvement enhances overall security and resilience.
9.3 Scheduling Regular Network Vulnerability Assessments
Conducting assessments on a scheduled basis helps ensure that vulnerabilities are continuously identified and addressed. Regular assessments provide insights into the effectiveness of security measures and help organizations stay ahead of emerging threats.
10. Future Trends in Network Vulnerability Assessment
10.1 Impact of AI and Automation
Artificial intelligence (AI) and automation are transforming cybersecurity. AI can rapidly process large volumes of data, detecting patterns and anomalies that could signal potential vulnerabilities. Automated tools can streamline the assessment process, allowing organizations to conduct assessments more efficiently.
10.2 New and Emerging Network Threats
As technology evolves, so do cyber threats. Organizations must stay informed about new and emerging threats, such as ransomware and phishing attacks. Ongoing training and awareness initiatives enable employees to identify potential threats and react effectively.
10.3 Future-Proofing Network Security
Investing in scalable and flexible security solutions helps organizations prepare for future challenges. This may involve adopting cloud-based security solutions, implementing zero-trust architectures, and fostering a culture of security awareness among employees.
11. Compliance and Regulatory Considerations
11.1 Key Compliance Standards (e.g., GDPR, ISO 27001)
In today’s digital landscape, organizations must navigate a complex web of compliance Establishing standards and regulations is essential for safeguarding data protection and security. Key compliance standards include:
- General Data Protection Regulation (GDPR): Enforced in the European Union (EU), GDPR mandates strict guidelines for data handling, storage, and processing. Organizations must obtain explicit consent from individuals before collecting personal data, implement robust security measures to protect this data, and provide individuals with rights over their data, including access and deletion. Non-compliance can result in significant fines, reaching up to 4% of annual global turnover or €20 million, whichever is higher.
- ISO 27001: This global standard defines best practices for the establishment, implementation, maintenance, and ongoing enhancement of an information security management system (ISMS). ISO 27001 emphasizes risk management and requires organizations to assess their security risks, implement appropriate controls, and regularly review and update these measures. Obtaining ISO 27001 certification can strengthen an organization’s reputation and foster trust among clients and partners.
- Health Insurance Portability and Accountability Act (HIPAA): For organizations in the healthcare sector, HIPAA sets the standard for protecting sensitive patient information. It mandates secure storage and transmission of protected health information (PHI) and requires organizations to implement administrative, physical, and technical safeguards to ensure compliance.
- Payment Card Industry Data Security Standard (PCI DSS): Organizations that handle credit card transactions must comply with PCI DSS, which establishes security measures to protect cardholder data. This involves ensuring a secure network, enforcing robust access control measures, and consistently monitoring and testing network systems.
11.2 Best Practices for Meeting Regulatory Requirements
To effectively meet regulatory requirements and ensure compliance, organizations should adopt the following best practices:
- Conduct Regular Audits: Periodic audits help organizations assess their compliance status and identify areas for improvement. Audits should evaluate data handling practices, security measures, and adherence to relevant regulations.
- Maintain Comprehensive Documentation: Documenting all processes, policies, and procedures related to data management and security is essential. This documentation should include data protection policies, incident response plans, and records of employee training on compliance topics.
- Implement Employee Training Programs: Regular training sessions for employees on compliance requirements and data protection best practices help foster a culture of security awareness. Employees should understand their roles in protecting sensitive data and the consequences of non-compliance.
- Develop a Response Plan for Data Breaches: Organizations must have a clear response plan in place to address data breaches promptly. This plan should outline the steps for investigating the breach, notifying affected individuals, and reporting the incident to regulatory authorities as required by law.
- Use Compliance Management Tools: Leveraging technology can streamline compliance efforts. Compliance management tools can help organizations track regulatory changes, manage audits, and ensure that policies are up to date.
11.3 Consequences of Non-Compliance
Failing to comply with relevant regulations can lead to severe consequences for organizations, including:
- Financial Penalties: Non-compliance can result in hefty fines. For instance, under GDPR, organizations may face fines up to €20 million or 4% of their annual global revenue. Other regulations, such as HIPAA, also impose substantial penalties for violations.
- Legal Actions: Organizations may face lawsuits from affected individuals or regulatory bodies for non-compliance. Legal actions can result in additional financial burdens and reputational damage.
- Reputational Damage: Non-compliance can erode customer trust and damage an organization’s reputation. Consumers are increasingly aware of data privacy issues, and a history of non-compliance can lead to loss of business and difficulty attracting new customers.
- Operational Disruptions: Investigations into compliance failures can disrupt business operations. Organizations may need to divert resources to address compliance issues, impacting productivity and profitability.
- Increased Scrutiny from Regulators: Non-compliance may lead to heightened scrutiny from regulatory bodies. Organizations may be subject to more frequent audits and investigations, creating additional operational challenges.
12. Building a Culture of Cybersecurity
12.1 Training and Awareness Programs
Building a robust culture of cybersecurity begins with effective training and awareness programs. Organizations must recognize that their employees are often the first line of defense against cyber threats. Therefore, comprehensive training initiatives are essential to equip staff with the knowledge and skills needed to identify and respond to potential security threats.
- Regular Training Sessions: Conducting regular training sessions on various cybersecurity topics, such as phishing attacks, password management, and data protection, helps employees stay informed about the latest threats and best practices. These sessions should be interactive, incorporating real-world scenarios to engage participants effectively.
- Onboarding Programs: Integrating cybersecurity training into the onboarding process for new employees is crucial. New hires should receive training on the organization’s security policies, procedures, and expectations from the outset, establishing a strong foundation for security awareness.
- Refresher Courses: Cybersecurity is a constantly evolving field, with new threats emerging regularly. Organizations should offer refresher courses and updates to ensure employees remain aware of the latest threats and security protocols.
- Gamification: Implementing gamification techniques, such as quizzes, competitions, and simulations, can make training more engaging and enjoyable. This approach not only enhances learning retention but also fosters a sense of camaraderie among employees as they work together to complete challenges.
12.2 Establishing Security Protocols
Establishing clear and comprehensive security protocols is essential for creating a culture of cybersecurity within an organization. These protocols serve as guidelines for employees, helping them understand their responsibilities regarding data protection and security.
- Developing Security Policies: Organizations should create detailed security policies that outline acceptable use of technology, data handling procedures, and incident response protocols. These policies must be readily accessible and clearly communicated to all employees.
- Incident Response Plans: Having a well-defined incident response plan ensures that employees know how to respond in the event of a security breach or incident. This plan should include steps for reporting incidents, assessing damage, and communicating with stakeholders.
- Access Control Measures: Implementing strict access control measures helps limit the exposure of sensitive data. Employees should have access only to the information necessary for their roles. Regular reviews of access permissions can help identify any potential risks.
- Regular Policy Reviews: Security policies and protocols should be reviewed and updated regularly to ensure they remain relevant and effective. Engaging employees in this process can provide valuable insights and foster a sense of ownership over the organization’s security practices.
12.3 Encouraging a Proactive Security Mindset
Fostering a proactive security mindset among employees is crucial for building a culture of cybersecurity. When employees feel empowered to take an active role in maintaining security, organizations can significantly enhance their defenses against cyber threats.
- Open Communication: Encourage open communication about security concerns and incidents. Employees should feel at ease reporting suspicious activities or potential vulnerabilities without fear of retaliation. Fostering an environment that encourages this openness is essential. A supportive environment fosters a culture of vigilance.
- Recognition and Rewards: Implementing a recognition and rewards system for employees who demonstrate exceptional commitment to cybersecurity can reinforce positive behavior. This could include acknowledging employees who identify potential threats or contribute to improving security protocols.
- Involvement in Security Initiatives: Involve employees in cybersecurity initiatives, such as conducting vulnerability assessments or participating in cybersecurity awareness campaigns. This engagement fosters a sense of responsibility and ownership over the organization’s security efforts.
- Leadership Commitment: Leadership plays a crucial role in shaping organizational culture. When leaders prioritize cybersecurity and model secure behaviors, employees are more likely to follow suit. Regular communication from leadership about the importance of cybersecurity reinforces its significance within the organization.
12.4 Monitoring and Continuous Improvement
Cultivating a culture of cybersecurity is a continuous effort that demands regular monitoring and enhancement. Organizations should regularly assess their cybersecurity practices and make necessary adjustments to enhance their defenses.
- Feedback Mechanisms: Implementing feedback mechanisms allows employees to provide input on security practices and training programs. This feedback can help identify areas for improvement and foster a culture of collaboration.
- Performance Metrics: Establishing performance metrics to measure the effectiveness of training programs and security initiatives helps organizations track progress. Metrics may include the number of reported incidents, employee participation rates in training, and the effectiveness of incident response.
- Adapting to Emerging Threats: Cybersecurity is a rapidly evolving field, and organizations must stay informed about emerging threats and trends. Regularly reviewing industry best practices and adapting security measures accordingly ensures that organizations remain resilient against new challenges.
13 Difference between Compliance and Regulatory Considerations and Building a Culture of Cybersecurity
| Aspect | Compliance and Regulatory Considerations | Building a Culture of Cybersecurity |
|---|
| Focus Area | Adherence to laws, regulations, and standards governing data protection and security. | Establishing an organizational culture that prioritizes cybersecurity practices. |
| Key Components | Compliance standards (e.g., GDPR, ISO 27001), best practices, consequences of non-compliance. | Training programs, security protocols, proactive security mindset, continuous improvement. |
| Objectives | Ensure legal compliance, avoid penalties, protect sensitive data, maintain organizational reputation. | Foster employee awareness, encourage responsible behavior, enhance overall security posture. |
| Employee Role | Employees must understand compliance requirements and follow established regulations. | Employees are encouraged to take an active role in security, identifying risks and reporting issues. |
| Training and Awareness | Focuses on educating employees about regulatory requirements and consequences of non-compliance. | Emphasizes ongoing cybersecurity training and awareness to identify threats. |
| Documentation | Requires comprehensive documentation of policies, procedures, and compliance efforts. | Promotes clear security protocols and documentation of security practices. |
| Incident Response | Outlines specific steps for responding to compliance-related incidents and breaches. | Develops an overall incident response plan focusing on security incidents. |
| Continuous Monitoring | Regular audits and assessments to ensure compliance with regulations. | Continuous improvement of security practices through feedback and performance metrics. |
| Management Involvement | Leadership must ensure compliance and support audit processes. | Leadership commitment is crucial in promoting cybersecurity culture and practices. |
| Consequences of Non-Adherence | Financial penalties, legal actions, reputational damage, operational disruptions. | Weakened security posture, increased vulnerability to attacks, potential data breaches. |
14 FAQS
1: What is the importance of compliance in cybersecurity?
Answer: Compliance in cybersecurity is crucial because it ensures that organizations adhere to laws and regulations designed to protect sensitive data. Meeting compliance requirements helps prevent legal penalties, protects against data breaches, and builds trust with customers and stakeholders. Compliance also establishes a framework for implementing effective security measures and managing risks.
2: What are some key compliance standards organizations should be aware of?
Answer: Organizations should be aware of several key compliance standards, including:
- General Data Protection Regulation (GDPR): Protects personal data of individuals within the EU.
- ISO 27001: Provides guidelines for establishing an information security management system (ISMS).
- Health Insurance Portability and Accountability Act (HIPAA): Governs the protection of patient health information in the healthcare sector.
- Payment Card Industry Data Security Standard (PCI DSS): Sets security standards for organizations handling credit card transactions.
3: How can organizations build a culture of cybersecurity?
Answer: Organizations can build a culture of cybersecurity by implementing comprehensive training and awareness programs, establishing clear security protocols, encouraging open communication about security issues, and involving employees in security initiatives. Leadership commitment is also essential, as it sets the tone for the organization’s security priorities and practices.
4: What role do employees play in maintaining compliance?
Answer: Employees play a critical role in maintaining compliance by understanding and following established policies and procedures related to data protection and security. They should be aware of regulatory requirements and the importance of safeguarding sensitive information. Regular training and clear communication of expectations help employees fulfill their compliance responsibilities effectively.
5: What are the consequences of non-compliance in cybersecurity?
Answer: The consequences of non-compliance in cybersecurity can be severe, including:
- Financial Penalties: Organizations may face hefty fines for failing to meet regulatory requirements.
- Legal Actions: Non-compliance can result in lawsuits from affected individuals or regulatory bodies.
- Reputational Damage: A history of non-compliance can erode customer trust and damage the organization’s reputation.
- Operational Disruptions: Investigations into compliance failures can divert resources and disrupt business operations.
15 Conclusion
In today’s digital landscape, building a strong cybersecurity framework is essential for organizations of all sizes. Compliance with regulatory standards, such as GDPR and ISO 27001, provides a foundation for protecting sensitive data and maintaining stakeholder trust. Regular audits and employee training are crucial to ensure adherence to these standards and to prevent penalties. Simultaneously, fostering a culture of cybersecurity empowers employees to recognize and respond to threats proactively. By implementing comprehensive training programs and clear security protocols, organizations can cultivate a security-first mindset among their workforce. Ultimately, integrating compliance with a proactive cybersecurity culture enhances an organization’s resilience against evolving threats, ensuring long-term security and success in a rapidly changing environment. Prioritizing these elements not only protects the organization but also builds a reputation for reliability and trustworthiness in the eyes of clients and partners.
