In today’s interconnected world, understanding the basic concepts of risk, vulnerability, and threat is crucial for safeguarding businesses, systems, and individuals. These three elements form the foundation of security strategies and protocols, helping to manage potential dangers effectively.
1: What is Risk?
Definition of Risk in Security
Risk is the likelihood of a negative event that can harm an organization. In security, risk arises when a threat actor takes advantage of a vulnerability, potentially leading to data loss, financial damage, or operational disruption. It’s important to note that risk is a combination of two factors: the likelihood of the event occurring and the impact it will have if it does.
Types of Risk
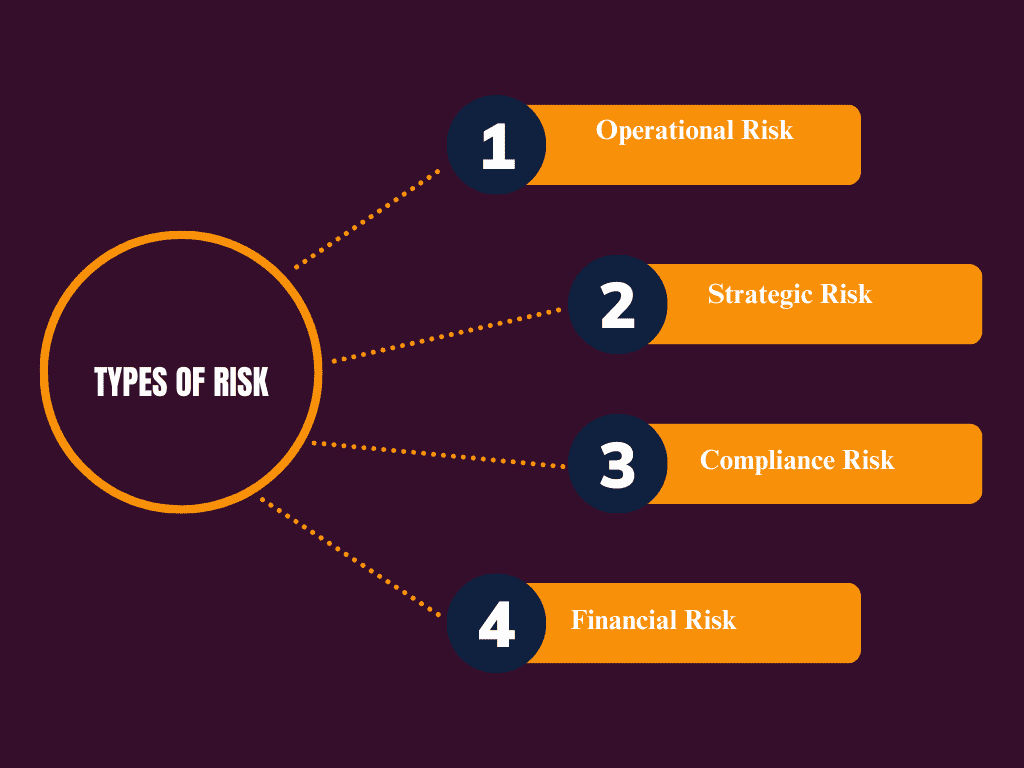
- Operational Risk: Refers to day-to-day risks related to business operations. For example, a cyber-attack that disrupts an organization’s website would be considered an operational risk.
- Strategic Risk: This involves long-term threats to a business’s success, like a change in market conditions or the introduction of a new competitor.
- Compliance Risk: Failure to follow laws and regulations can lead to compliance risk, which might result in legal penalties, fines, or damage to reputation.
- Financial Risk: Financial losses from theft, fraud, or investment risks. This is particularly important for companies dealing with sensitive financial information.
Examples of Risk
An e-commerce company may face the risk of a hacker stealing customer payment information. The hacker could exploit a vulnerability in the company’s payment processing system, causing financial loss, legal consequences, and damage to customer trust. Understanding these potential risks is critical for businesses that rely on secure transactions.
2: Understanding Vulnerability
Definition of Vulnerability
Vulnerability is any weakness in a system, process, or human behavior that can be exploited by a threat. These weaknesses can exist in software, hardware, or within the actions of employees. Managing vulnerabilities is an ongoing task that requires constant monitoring and quick responses to emerging threats.
Types of Vulnerabilities
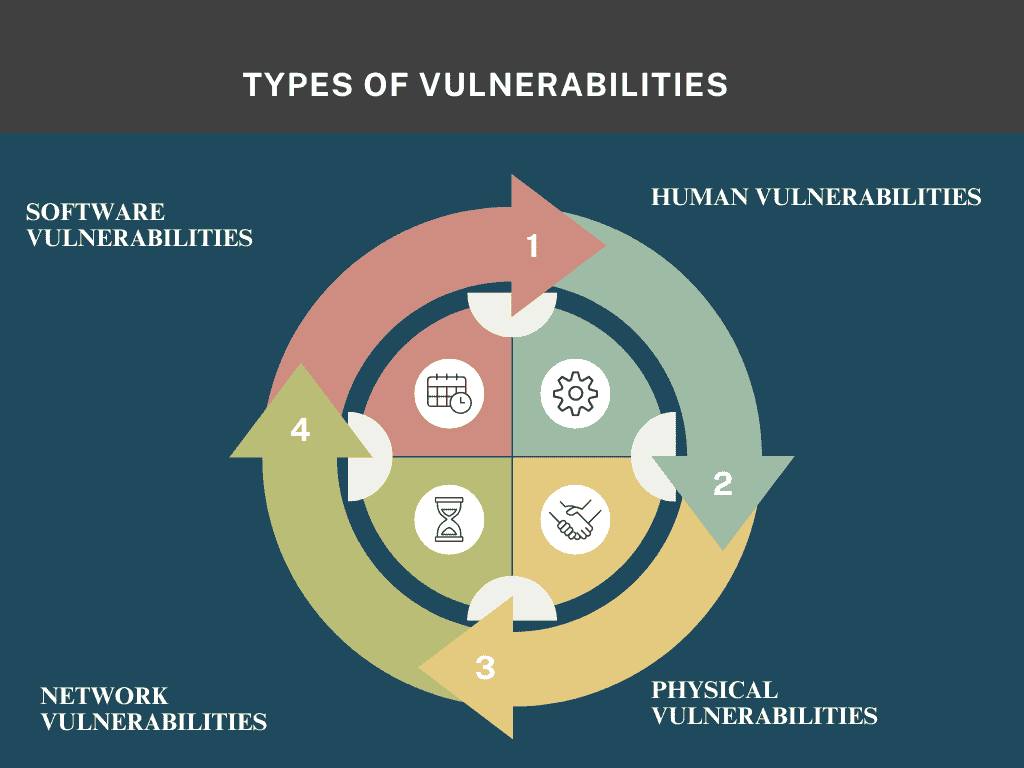
- Software Vulnerabilities: Errors or bugs in software code that make it easier for attackers to gain unauthorized access. For example, outdated operating systems or unpatched applications are common sources of software vulnerabilities.
- Human Vulnerabilities: Often referred to as the “human element,” these include mistakes made by employees or users, such as falling for phishing attacks or using weak passwords.
- Physical Vulnerabilities: These occur when physical security measures are lacking, such as insufficiently protected data centers or easily accessible hardware that holds sensitive data.
- Network Vulnerabilities: Flaws in network configurations, such as unsecured Wi-Fi networks or unencrypted data transmissions, which could be intercepted by malicious actors.
How Vulnerabilities Are Exploited
When a vulnerability is discovered, threat actors can use various tactics to exploit it. For instance, if a company fails to update its software, attackers might use a known vulnerability to inject malware. Similarly, employees who click on phishing emails unknowingly open the door for malicious software to enter company systems. These exploited vulnerabilities can lead to breaches, data theft, or operational damage.
3: Defining a Threat
What Constitutes a Threat?
A threat is any event, condition, or actor that has the potential to harm an organization by exploiting vulnerabilities. Threats can originate from many sources, including malicious individuals, natural disasters, or even unintentional human errors. The goal of threat management is to anticipate, detect, and mitigate these dangers before they cause significant damage.
Internal vs. External Threats
- Internal Threats: These are threats that come from within the organization. Insider threats may include employees, contractors, or partners who intentionally or unintentionally cause harm. An example of an internal threat is an employee misusing their access to steal sensitive company data.
- External Threats: These originate from outside the organization, including hackers, competitors, or even natural events like hurricanes. Cyber-attacks such as Distributed Denial of Service (DDoS) or ransomware are classic examples of external threats.

Types of Threats
- Cyber Threats: These include hacking, phishing, malware, and ransomware attacks that target digital systems and networks.
- Environmental Threats: Natural events like floods, fires, and earthquakes can destroy physical infrastructures, such as servers, leading to data loss or system downtime.
- Human Threats: This can include intentional acts such as theft or sabotage by employees, as well as external actors trying to exploit an organization’s vulnerabilities.
- Technological Threats: System failures, hardware malfunctions, or outdated technology can lead to vulnerabilities being exposed to threats, making organizations more susceptible to attacks.
4: Relationship Between Risk, Vulnerability, and Threat
How These Concepts Interact
The interaction between risk, vulnerability, and threat forms the foundation of any security strategy. Risk exists when a threat actor can exploit a vulnerability. For example, a company may have a vulnerability in its network configuration (weakness), which can be exploited by a cyber-criminal (threat), leading to potential loss or damage (risk).
The Role of Vulnerabilities in Risk Assessment
During a risk assessment, identifying and prioritizing vulnerabilities is crucial. An organization’s security posture depends on understanding where its weaknesses lie and how likely they are to be targeted. Fixing critical vulnerabilities reduces the overall risk, even if the threat landscape remains unchanged.
Examples of How Threats Exploit Vulnerabilities
Consider a company with a vulnerability in its employee password policy—employees use weak or easily guessable passwords. A threat actor can exploit this by launching a brute-force attack, trying different password combinations until they gain access to the system. The consequence is a data breach that exposes sensitive information.
5: Risk Assessment
Internal vs. External Threats
- Identify Potential Threats: The first step in assessing risk is recognizing potential threats. This can include both internal and external threats, such as cyber-attacks or natural disasters.
- Evaluate Vulnerabilities: Identify areas where the organization is weak, such as unpatched software, unsecured networks, or insufficient employee training.
- Calculate Risk Levels: Risk is a combination of the likelihood of a threat and the severity of its potential impact. A high likelihood of a major impact represents a high risk.
- Prioritize Risk: Not all risks are equal. Prioritize those with the highest potential to cause significant harm and address them first.
Tools for Identifying Risks, Vulnerabilities, and Threats
Risk management frameworks like NIST or ISO 27001 are used to assess and manage risks. Tools like Nessus, OpenVAS, and Qualys scan for vulnerabilities, helping organizations determine which risks to address first.
Case Studies of Risk Assessment
In the financial sector, risk assessments are crucial for preventing fraud and ensuring data protection. For example, a bank may assess the risk of unauthorized access to customer accounts through phishing attacks. By implementing stronger authentication measures, they reduce the risk of such threats causing harm.
6: Mitigating Risk
Strategies to Address and Reduce Risk
There are several methods for managing risk, each with its advantages depending on the organization’s priorities:
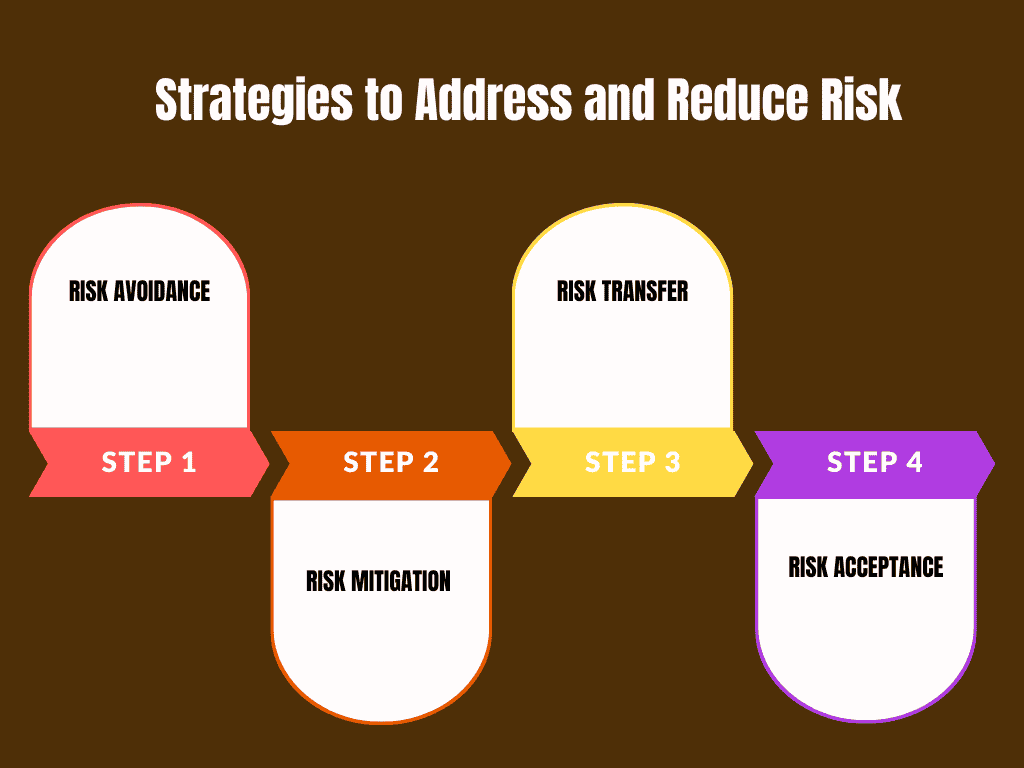
- Risk Avoidance: Avoiding activities that introduce risk altogether. For example, a company might decide not to store sensitive customer data if the risks associated with a data breach are too high.
- Risk Mitigation: Reducing the impact or likelihood of a threat by taking preventive measures. This can include applying software patches, improving employee training, and strengthening network security.
- Risk Transfer: Shifting the risk to a third party, such as through insurance or outsourcing security functions to a managed service provider.
- Risk Acceptance: In some cases, organizations may choose to accept certain risks if the cost of mitigating them outweighs the potential damage.
Addressing Vulnerabilities to Minimize Risk
Managing vulnerabilities is a proactive approach to reducing risk. Regular vulnerability scanning and patch management are essential for maintaining strong defenses against threats. Employees should also be trained regularly to recognize and avoid social engineering attacks like phishing.
Threat Detection and Prevention Techniques
Early detection of threats is key to preventing them from causing damage. Intrusion Detection Systems (IDS) and firewalls act as the first line of defense, while Security Information and Event Management (SIEM) tools provide real-time monitoring and alerts for potential threats.
7: Vulnerability Management
Identifying and Managing Vulnerabilities
Vulnerability management is a continuous cycle that involves discovering, assessing, addressing, and documenting weaknesses in software and systems. This proactive approach ensures that organizations can effectively mitigate risks and enhance their security posture. It is essential because even a small weakness can lead to severe consequences if exploited. Organizations must regularly scan their networks and systems to uncover new vulnerabilities and act quickly to mitigate them.
Vulnerability Patching and Fixing
Patching vulnerabilities means applying updates or “patches” to software that close security gaps. However, patch management is not always simple. Some organizations may delay patches due to compatibility issues or concerns about downtime. Nonetheless, failing to apply patches exposes systems to risks. An effective patch management strategy involves prioritizing critical patches and scheduling regular updates to minimize disruptions.
Tools for Vulnerability Scanning
Several tools assist organizations in identifying and managing vulnerabilities:
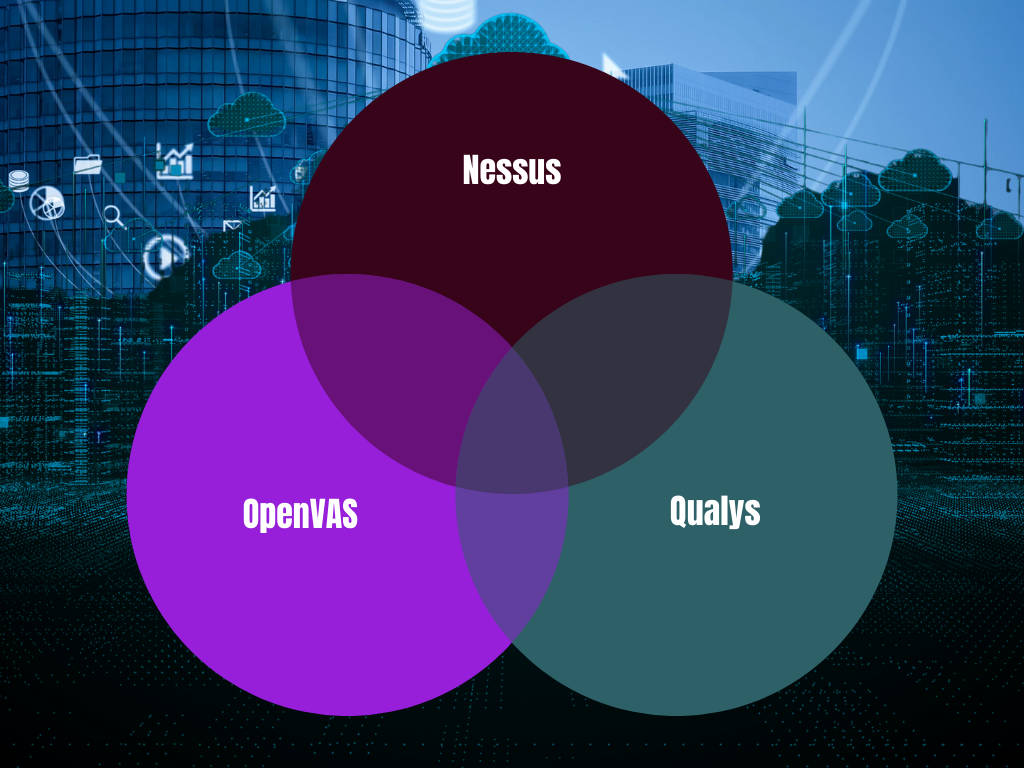
- Nessus: A highly effective vulnerability scanner that helps in detecting issues like outdated software, insecure settings, and misconfigurations.
- Qualys: A cloud-based platform that performs regular scans and reports on vulnerabilities, allowing organizations to focus on addressing the most critical issues.
- OpenVAS: An open-source alternative for vulnerability scanning that is flexible and robust, offering a comprehensive solution for identifying weaknesses in a network.
Vulnerability management tools enable organizations to stay ahead of potential threats by finding and fixing vulnerabilities before attackers can exploit them.
8: Threat Detection and Response
Threat Intelligence and Monitoring
Threat detection and response require continuous monitoring of systems to detect any unusual activities that might indicate an attack. Threat intelligence refers to the process of collecting, analyzing, and acting on data regarding potential or current threats. Organizations use threat intelligence to understand attacker behavior, methods, and motivations.
In modern security environments, advanced monitoring tools are crucial for identifying potential security incidents in real-time. These tools use machine learning and AI to recognize patterns that may indicate malicious activity.
Developing an Effective Threat Response Plan
A well-structured threat response plan helps mitigate damage when a security breach occurs. An effective plan should include:
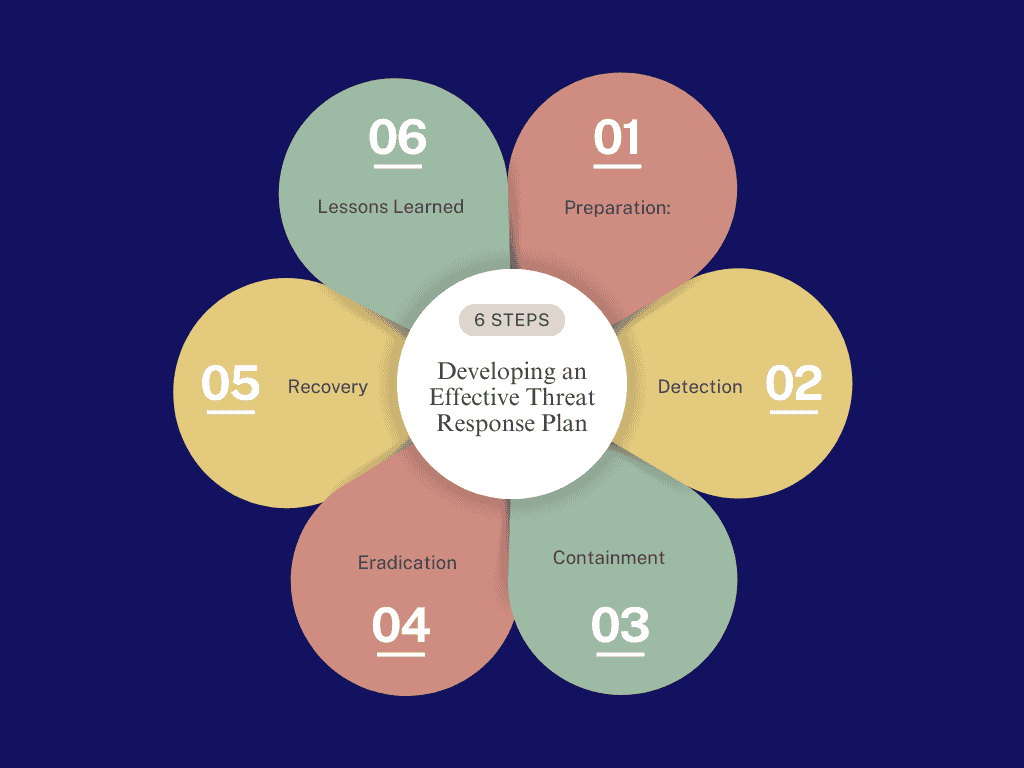
- Preparation: Define roles and responsibilities within the organization and ensure that all employees are trained on security protocols.
- Detection: Use monitoring tools and alert systems to identify threats as early as possible.
- Containment: Once a threat is detected, contain it to prevent further spread or damage. This could involve isolating affected systems or blocking certain network traffic.
- Eradication: Remove the threat from the system entirely, whether it’s a piece of malware, a compromised account, or an insider threat.
- Recovery: Restore affected systems, data, and operations while ensuring that security gaps are closed to prevent future attacks.
- Lessons Learned: Post-incident reviews are critical to understanding what happened and improving the organization’s defenses for the future.
Case Studies of Successful Threat Mitigation
One notable case of threat mitigation occurred when a large retail company successfully defended against a massive ransomware attack by using AI-based threat detection systems. The systems detected the attack early on and initiated an automated response that isolated the infected systems, preventing the spread of ransomware to the rest of the network. This proactive strategy helped the company avoid millions in potential losses.
9: The Future of Risk, Vulnerability, and Threat Management
Emerging Threats in Cybersecurity
As technology continues to evolve, so do the threats that accompany it. Emerging threats include:
- AI-Powered Cyber Attacks: Cybercriminals are using AI and machine learning to create more sophisticated attacks, such as AI-driven phishing or social engineering attacks.
- Deepfake Technology: Malicious actors are now using deepfake technology to create convincing fake videos or audio, which can be used for fraud, misinformation, or blackmail.
- Quantum Computing Threats: Quantum computers, which are currently under development, have the potential to break encryption algorithms that protect sensitive data today. This poses a major security threat to future systems unless encryption techniques evolve accordingly.
The increasing reliance on IoT (Internet of Things) devices also introduces new attack surfaces. These devices, often less secure than traditional systems, provide opportunities for cybercriminals to infiltrate networks.
The Role of AI and Machine Learning in Risk Management
AI and machine learning (ML) are transforming the way organizations approach risk management. AI-based tools can analyze vast amounts of data and identify potential threats much faster than human analysts. For example:
- Automated Risk Assessment: AI systems can automatically scan networks for vulnerabilities and assess risk based on historical data, potential impact, and current threat trends.
- Predictive Analytics: By analyzing past attacks, AI can predict potential future threats, allowing organizations to proactively strengthen their defenses.
- Real-Time Monitoring: AI and ML tools continuously monitor systems and networks, detecting and responding to threats in real-time, often faster than traditional methods.
The integration of AI into risk management provides a more dynamic, proactive approach to security, helping organizations stay ahead of emerging threats.
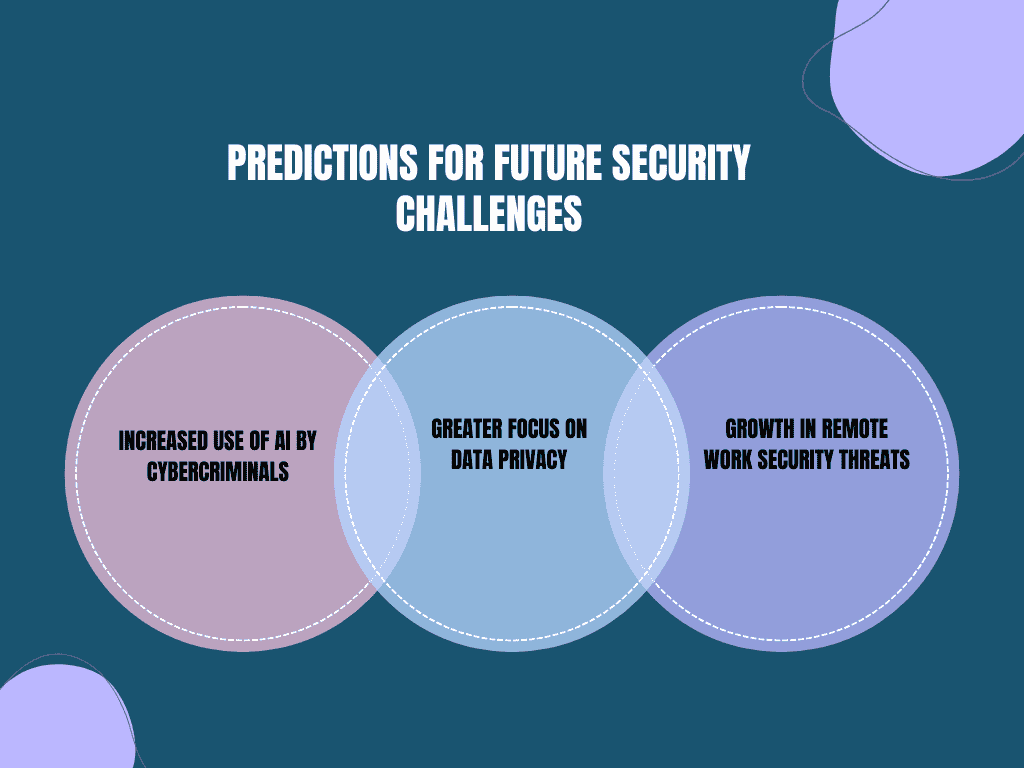
Predictions for Future Security Challenges
As the digital world expands, security challenges will continue to grow. Some predictions include:
- Increased Use of AI by Cybercriminals: As AI becomes more prevalent in defenses, attackers will also adopt AI to find vulnerabilities and launch more targeted, sophisticated attacks.
- Greater Focus on Data Privacy: With the implementation of more stringent data privacy regulations (e.g., GDPR), organizations will need to balance their security efforts with compliance, ensuring that personal data is both secure and handled according to legal requirements.
- Growth in Remote Work Security Threats: The rise of remote work has led to a broader attack surface, with employees accessing corporate networks from home or public Wi-Fi. Organizations will need to develop stronger remote work security policies to prevent breaches.
The future of security lies in innovation and adaptation, and organizations that invest in cutting-edge technologies like AI and ML will be better equipped to handle the challenges ahead.
10 Differences between Risk, Vulnerability
| Aspect | Risk | Vulnerability |
|---|
| Definition | The potential for loss or damage due to an exploit. | A weakness or flaw that can be exploited by threats. |
| Focus | Combines the likelihood of a threat and its impact. | Identifies gaps or weaknesses in a system. |
| Nature | Proactive – involves predicting potential issues. | Reactive – involves identifying existing weaknesses. |
| Impact | Depends on how severe and likely the threat is. | Can exist without being exploited until a threat acts. |
| Management | Involves mitigating and preparing for possible threats. | Managed by fixing or reducing weaknesses (e.g., patching). |
| Assessment | Evaluated by considering both vulnerabilities and threats. | Detected through security audits, scans, and testing. |
| Example | Data breach leading to financial loss or reputation damage. | Weak passwords or unpatched software allowing unauthorized access. |
| Role in Security | Helps prioritize actions based on potential outcomes. | Forms part of risk but does not cause direct harm by itself. |
11 FAQs
1. What is the difference between risk and vulnerability?
Risk refers to the possibility of loss or harm arising when a threat takes advantage of a vulnerability. Vulnerability is a specific weakness in a system that can be targeted but does not cause harm by itself.
2. How can vulnerabilities lead to risks?
Vulnerabilities, such as unpatched software, can be exploited by threats. When a threat takes advantage of a vulnerability, it becomes a risk that could lead to incidents like data breaches or system failures.
3. How can organizations manage risks and vulnerabilities?
Organizations manage risks by identifying potential threats and their impacts. They reduce vulnerabilities through regular software updates, applying security patches, and conducting employee training on security best practices.
4. Are all vulnerabilities considered risks?
Not all vulnerabilities are risks immediately. A vulnerability only becomes a risk when a relevant threat can exploit it, potentially leading to harm or loss for the organization.
5. What tools are used to assess risks and vulnerabilities?
Tools like Nessus and Qualys help identify vulnerabilities, while risk management frameworks such as ISO 27001 and NIST assist in systematic risk assessment and management.
Conclusion
Understanding the key differences between risk, vulnerability, and threat is fundamental to developing a comprehensive security strategy. Risk represents the potential for loss, vulnerability is the weakness that makes a system susceptible, and threat is the danger that exploits the vulnerability. Together, these concepts guide how businesses and organizations manage and mitigate security challenges.
By focusing on vulnerability management, threat detection, and risk assessment, companies can protect their systems from a wide range of attacks. As technology continues to advance, it’s crucial to remain vigilant and proactive, utilizing AI and machine learning to stay ahead of evolving threats.
Effective risk management is not a one-time task but an ongoing process that requires constant attention, updates, and learning from past incidents. By following these principles, organizations can reduce their exposure to risks, strengthen their defenses, and prepare for the future of cybersecurity.
