1 Introduction to Vulnerability Management
1 Definition and Importance
Vulnerability management is a critical aspect of cybersecurity that involves identifying, assessing, and addressing security weaknesses within an organization’s IT environment. These weaknesses, known as vulnerabilities, can exist in software, hardware, and network configurations. The importance of vulnerability management cannot be overstated; it helps organizations protect their sensitive data and maintain their reputation.
In a world where cyber threats are increasingly sophisticated, vulnerability management serves as a frontline defense. By proactively identifying vulnerabilities, organizations can mitigate potential risks before they can be exploited by malicious actors. This not only safeguards critical assets but also ensures compliance with industry regulations and standards, which often require organizations to maintain a robust vulnerability management program.

Moreover, effective vulnerability management can reduce the costs associated with data breaches and security incidents. By addressing vulnerabilities promptly, organizations can avoid the financial and reputational damage that often accompanies such events. In essence, vulnerability management is not just a technical process but a strategic imperative for any organization aiming to thrive in the digital age.
2 Overview of Digital Safety
Digital safety encompasses a wide range of practices designed to protect electronic information and systems from unauthorized access, attacks, and damage. This includes not only the security of data but also the integrity of systems and the trustworthiness of applications used within an organization.
Digital safety is increasingly relevant as businesses continue to integrate technology into every facet of their operations. From cloud computing to mobile devices, the expansion of digital resources has created new avenues for potential vulnerabilities. Organizations must take a holistic approach to digital safety, incorporating not just technology solutions but also policies, procedures, and employee training.
In this landscape, vulnerability management plays a vital role in digital safety. It ensures that organizations are not only aware of existing vulnerabilities but also equipped to respond to emerging threats. By creating a culture of vigilance and preparedness, organizations can enhance their overall security posture and protect their digital assets.
2. Understanding Vulnerabilities
1 Types of Vulnerabilities
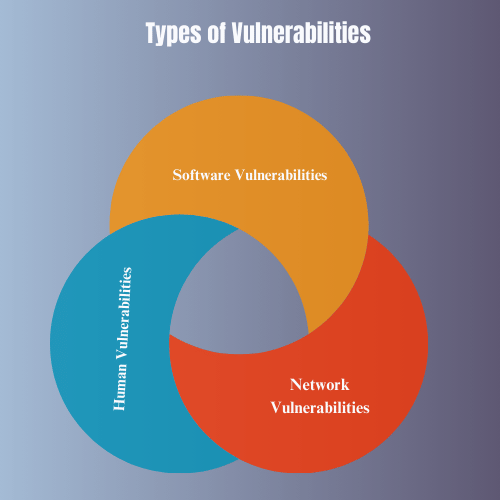
Vulnerabilities can be categorized into several types, each requiring different management strategies:
- Software Vulnerabilities: These are flaws in applications or operating systems that can be exploited by attackers. Examples include buffer overflows, SQL injection flaws, and unpatched software. Software vulnerabilities are often targeted in attacks because they can provide direct access to sensitive data or systems.
- Network Vulnerabilities: Weaknesses in network infrastructure, such as insecure protocols or poorly configured firewalls, can leave systems open to attack. Network vulnerabilities can allow attackers to intercept data, launch denial-of-service attacks, or gain unauthorized access to internal systems.
- Human Vulnerabilities: Often overlooked, human factors play a significant role in security. Phishing attacks, social engineering tactics, and insider threats exploit human behavior, making it essential to address these vulnerabilities through training and awareness programs.
2 Common Sources of Vulnerabilities
Organizations face vulnerabilities from various sources, including:
- Outdated Software: Failing to regularly update software can lead to vulnerabilities that attackers can exploit. Software vendors frequently release patches to address known issues, and neglecting these updates can have serious consequences.
- Misconfigured Systems: Configuration errors can create security holes. For example, leaving default settings in place can expose systems to unnecessary risks. Regular audits and configuration reviews can help identify and rectify these issues.
- Lack of Employee Training: Employees are often the weakest link in an organization’s security. Without proper training, they may fall victim to phishing attacks or make poor security choices. Regular training sessions can help cultivate a more security-conscious workforce.
To effectively manage these vulnerabilities, organizations must adopt a proactive approach that includes regular assessments and a commitment to continuous improvement.
3. Vulnerability Management Framework
1 Key Components of a Vulnerability Management Program
A comprehensive vulnerability management program should encompass the following key components:
- Identification: This involves scanning systems and networks to detect vulnerabilities. Automated tools can streamline this process, but manual assessments are also essential for a thorough evaluation.
- Prioritization: Once vulnerabilities are identified, organizations must prioritize them based on factors such as severity, potential impact, and exploitability. This ensures that resources are focused on the most critical issues first.
- Remediation: This step involves addressing the identified vulnerabilities. Remediation can take various forms, including applying patches, changing configurations, or implementing compensating controls.
- Verification: After remediation, it’s crucial to verify that vulnerabilities have been effectively addressed. This can be done through follow-up scans and assessments to confirm that the vulnerabilities are no longer present.
- Reporting: Keeping detailed records of identified vulnerabilities, actions taken, and results is essential for compliance and auditing purposes. Regular reporting also helps stakeholders understand the organization’s security posture.
2 The Vulnerability Management Lifecycle
The vulnerability management lifecycle is a continuous process that includes:
- Discovery: Regularly scanning systems and networks to identify vulnerabilities.
- Assessment: Evaluating the potential impact of each vulnerability on the organization.
- Prioritization: Ranking vulnerabilities based on risk factors.
- Remediation: Implementing fixes and changes to address vulnerabilities.
- Monitoring: Continuously monitoring systems for new vulnerabilities and changes.
- Reporting and Review: Keeping records and reviewing the effectiveness of the program.
This lifecycle ensures that vulnerability management is an ongoing effort rather than a one-time task, allowing organizations to stay ahead of emerging threats.
4. Identifying Vulnerabilities
1 Tools and Techniques for Vulnerability Assessment
Identifying vulnerabilities requires a combination of tools and techniques. Some commonly used methods include:
- Automated Scanners: These tools can quickly scan systems for known vulnerabilities. Popular options include Nessus, Qualys, and Rapid7. Automated scanners help streamline the discovery process, but they should be supplemented with manual assessments for a more comprehensive approach.
- Manual Testing: Security professionals can conduct manual tests to identify vulnerabilities that automated tools may miss. This includes techniques like penetration testing, where ethical hackers simulate attacks to uncover weaknesses.
- Code Reviews: For organizations that develop their software, conducting regular code reviews can help identify vulnerabilities during the development process. This proactive approach can reduce the risk of vulnerabilities making it into production.
2 Conducting Vulnerability Scans
Regular vulnerability scans are essential for identifying weaknesses in an organization’s systems. Here’s how to effectively conduct vulnerability scans:
- Schedule Regular Scans: Establish a routine for conducting scans, such as monthly or quarterly, depending on the organization’s size and complexity.
- Choose the Right Tools: Select tools that are appropriate for the organization’s environment. Some tools are better suited for network scans, while others excel in application security.
- Scan Configurations: Ensure that scans are configured correctly to cover all relevant assets. This includes network devices, servers, and applications.
- Review and Analyze Results: After scanning, carefully review the results to identify vulnerabilities that require action. Pay attention to high-severity issues that pose an immediate risk.
By conducting thorough vulnerability scans, organizations can maintain a clear understanding of their security posture and address weaknesses proactively.
5. Prioritizing Vulnerabilities
1 Risk Assessment and Impact Analysis
Not all vulnerabilities pose the same level of risk. A thorough risk assessment is essential to determine the potential impact of a vulnerability if exploited. This process involves:
- Identifying Assets: Understanding what assets are at risk, such as sensitive data or critical systems.
- Evaluating Potential Impacts: Assessing the potential consequences of a vulnerability being exploited. This can include financial loss, reputational damage, and operational disruptions.
- Determining Likelihood of Exploitation: Evaluating how likely it is that a vulnerability will be targeted by attackers. Factors such as recent exploit activity and the existence of public exploits should be considered.
5.2 Factors for Effective Prioritization
When prioritizing vulnerabilities, organizations should consider several factors:
- Severity of the Vulnerability: Use scoring systems like the Common Vulnerability Scoring System (CVSS) to assess the severity of vulnerabilities. Higher scores indicate more critical issues.
- Impact on Business Operations: Determine how a vulnerability could affect business operations. Vulnerabilities affecting critical systems should be prioritized over those with minimal impact.
- Exploitability: Evaluate how easily an attacker could exploit the vulnerability. Vulnerabilities that are easy to exploit and have high potential impact should be addressed first.
By prioritizing vulnerabilities based on these factors, organizations can allocate resources more effectively and reduce their overall risk.
6. Remediation Strategies
1 Patch Management Best Practices
Patching is a key remediation strategy for addressing software vulnerabilities. Effective patch management involves:
- Regularly Applying Updates: Organizations should keep software up to date by applying patches as soon as they are released. This minimizes the window of opportunity for attackers.
- Testing Patches Before Deployment: Before applying patches, organizations should test them in a controlled environment to ensure they don’t disrupt operations or introduce new issues.
- Creating a Patch Management Schedule: Develop a routine schedule for patch management to ensure that systems remain secure. This can include monthly patch cycles or ad-hoc patches for critical vulnerabilities.
2 Mitigation Techniques
In situations where immediate remediation isn’t possible, organizations can implement mitigation techniques to reduce risk. These include:
- Firewalls: Deploying firewalls to control incoming and outgoing network traffic can help block unauthorized access to systems.
- Access Controls: Implementing strict access controls ensures that only authorized personnel can access sensitive systems and data. This can include multi-factor authentication and role-based access controls.
- Intrusion Detection Systems (IDS): IDS can monitor network traffic for suspicious activity, alerting administrators to potential breaches or attacks.
3 Developing an Incident Response Plan
An incident response plan is crucial for managing security incidents effectively. Key components of a robust incident response plan include:
- Roles and Responsibilities: Clearly define who is responsible for what during a security incident. This ensures that everyone knows their role when an incident occurs.
- Communication Protocols: Establish communication protocols for internal teams and external stakeholders. Effective communication is vital during a crisis.
- Post-Incident Review: After an incident, conduct a review to analyze what happened, what worked, and what could be improved. This helps organizations learn from incidents and strengthen their response in the future.
By implementing these remediation strategies, organizations can effectively address vulnerabilities and enhance their overall security posture.
7. Continuous Monitoring and Review
1 Importance of Ongoing Vulnerability Management
Vulnerability management is not a one-time task; it requires continuous attention. The importance of ongoing vulnerability management lies in the dynamic nature of the threat landscape. New vulnerabilities are discovered regularly, and cyber attackers are always looking for ways to exploit weaknesses.
Continuous monitoring allows organizations to stay ahead of potential threats. It ensures that any new vulnerabilities are identified and addressed promptly. By treating vulnerability management as an ongoing process, organizations can adapt to changing risks and maintain a strong security posture.
2 Setting Up a Vulnerability Monitoring System
To establish an effective vulnerability monitoring system, organizations should consider the following steps:
- Select Monitoring Tools: Choose tools that can provide real-time alerts for new vulnerabilities, compliance issues, or unauthorized changes.
- Define Monitoring Parameters: Determine which systems and applications need to be monitored. This should include critical infrastructure and any areas with sensitive data.
- Establish Alerting Mechanisms: Configure alerts to notify relevant personnel when new vulnerabilities are detected or when compliance issues arise.
- Regularly Review Monitoring Results: Schedule regular reviews of monitoring results to ensure that vulnerabilities are being addressed and that the monitoring system is functioning correctly.
By implementing a robust vulnerability monitoring system, organizations can maintain an active defense against emerging threats and ensure ongoing digital safety.
8. Training and Awareness
1 Educating Staff on Vulnerability Management
Employee training is a cornerstone of effective vulnerability management. Educating staff on security best practices can significantly reduce the likelihood of human-related vulnerabilities. Training should cover topics such as:
- Recognizing Phishing Attempts: Employees should learn how to identify phishing emails and avoid falling victim to scams that can compromise security.
- Creating Strong Passwords: Training on creating strong passwords and the importance of using different passwords for different accounts can help mitigate risks associated with weak passwords.
- Understanding Security Policies: Employees should be familiar with the organization’s security policies and procedures, ensuring they understand their roles in maintaining security.
2 Building a Culture of Security Awareness
Creating a culture of security awareness involves fostering an environment where security is a shared responsibility. Here are some strategies to build this culture:
- Regular Training Sessions: Conduct periodic training sessions to reinforce security practices and keep employees informed about new threats.
- Encouraging Reporting: Encourage employees to report suspicious activities or potential vulnerabilities without fear of repercussions. This promotes a proactive approach to security.
- Incentives for Good Practices: Consider implementing incentive programs that reward employees for adopting good security practices or identifying vulnerabilities.
By investing in employee training and building a culture of security awareness, organizations can significantly enhance their vulnerability management efforts.
9. Compliance and Best Practices
1 Understanding Industry Standards and Regulations
Many industries have specific standards and regulations governing vulnerability management. Understanding these requirements is crucial for ensuring compliance. Key regulations include:
- General Data Protection Regulation (GDPR): For organizations operating in the European Union, GDPR mandates the protection of personal data and requires regular vulnerability assessments.
- Payment Card Industry Data Security Standard (PCI DSS): Businesses that handle credit card transactions must adhere to PCI DSS, which includes strict guidelines for vulnerability management.
- Health Insurance Portability and Accountability Act (HIPAA): Healthcare organizations must comply with HIPAA, which requires safeguarding patient information and conducting regular risk assessments.
2 Best Practices for Effective Vulnerability Management
To establish a robust vulnerability management program, organizations should adopt the following best practices:
- Regular Audits: Conducting regular audits ensures that vulnerability management policies and practices are followed consistently.
- Documentation: Maintaining detailed records of identified vulnerabilities, assessments, and remediation efforts is essential for compliance and accountability.
- Collaboration Across Departments: Encourage collaboration between IT, security, and other departments to ensure a comprehensive approach to vulnerability management.
- Stay Informed: Keep up with the latest trends in cybersecurity and emerging threats to adapt vulnerability management strategies accordingly.
By adhering to compliance requirements and implementing best practices, organizations can enhance their vulnerability management efforts and reduce their overall risk.
10 Difference between vulnerability management and other related practices
| Aspect | Vulnerability Management | Other Security Practices |
|---|
| Focus | Identifying, assessing, and addressing system weaknesses | Broader security measures like access control and monitoring |
| Process | Continuous cycle of identification, prioritization, remediation, and verification | Can be one-time assessments or ongoing security protocols |
| Goal | Reduce risk by fixing vulnerabilities before they are exploited | Protect overall security posture through various means |
| Tools | Vulnerability scanners, risk assessment tools | Firewalls, intrusion detection systems, antivirus software |
| Approach | Proactive; seeks to discover and remediate before incidents occur | Can be reactive; often responds to incidents as they happen |
11 FAQs
1: What is vulnerability management?
Answer: Vulnerability management is the process of identifying, assessing, and addressing security weaknesses in an organization’s IT environment. It involves regularly scanning systems for vulnerabilities, prioritizing them based on risk, and implementing remediation strategies to mitigate those risks.
2 : Why is vulnerability management important?
Answer: Vulnerability management is crucial because it helps organizations protect sensitive data, maintain compliance with regulations, and reduce the risk of cyberattacks. By proactively addressing vulnerabilities, organizations can prevent data breaches and minimize potential damage from security incidents.
3: How often should vulnerability assessments be conducted?
Answer: Vulnerability assessments should be conducted regularly, typically at least once a month. However, organizations may choose to conduct assessments more frequently based on their specific risk profile, the sensitivity of their data, and any changes in their IT environment.
4: What are common tools used in vulnerability management?
Answer: Common tools used in vulnerability management include automated scanners like Nessus, Qualys, and Rapid7 for detecting vulnerabilities. Other tools may include penetration testing software and configuration management tools that help identify and remediate weaknesses in systems.
5: How can organizations prioritize vulnerabilities effectively?
Answer: Organizations can prioritize vulnerabilities by assessing their severity, potential impact on business operations, and likelihood of exploitation. Using scoring systems like the Common Vulnerability Scoring System (CVSS) can help in ranking vulnerabilities to ensure that the most critical issues are addressed first.
12 Conclusion
In summary, effective vulnerability management practices are essential for maintaining digital safety. By understanding and addressing vulnerabilities, organizations can protect their sensitive information, maintain compliance, and reduce the risk of cyber threats. The continuous process of identifying, prioritizing, and remediating vulnerabilities is critical in today’s fast-paced digital environment. By investing in employee training, monitoring systems, and compliance efforts, organizations can foster a culture of security awareness and preparedness.
Let me know if you need any more changes or additional content!
