1. Introduction to Network Security Hardware
In the modern digital world, security is more important than ever. With so many businesses running online, the need for network security hardware has grown. This hardware protects networks from threats like hackers, viruses, and malware. In simple words, network security hardware refers to physical devices that help secure your network and keep it safe from attacks.
Let’s take a closer look at what this hardware is and why it’s so important for businesses today.
What is Network Security Hardware?
Network security hardware is made up of physical devices that help protect your business’s network. These devices include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and VPN routers. Each device has a job to do in keeping your network safe.
- Firewalls: These devices monitor and control the traffic coming in and out of your network. They act like a wall, blocking harmful traffic and allowing safe traffic.
- IDS and IPS: These systems detect and stop suspicious activities on your network. They alert you when something looks wrong and prevent potential attacks.
- VPN Routers: Virtual Private Network (VPN) routers secure your data when it’s being transferred over the internet. They ensure that your connection is private and secure, especially for remote workers.
Why Network Security Hardware is Important
There are many reasons why network security hardware is a must-have for businesses. Here are the top four reasons why it’s essential for safe networks:
- Protection from Cyber Threats
Every day, businesses face cyberattacks from hackers, malware, and viruses. Network security hardware helps block these threats and keeps your data safe. It ensures that your network is secure from both outside attacks and internal threats. - Monitoring Your Network
Security hardware constantly watches over your network. It tracks all the data flowing in and out, helping to spot any unusual activity. By catching these issues early, your business can act quickly to stop a threat before it causes damage. - Meeting Compliance Requirements
Many industries, such as healthcare and finance, have strict rules for keeping data safe. Network security hardware helps businesses meet these requirements. By using the right hardware, you can stay compliant with industry regulations and avoid legal problems. - Preventing Downtime
Cyberattacks can cause your network to shut down, resulting in lost revenue and time. With the right network security hardware in place, you reduce the risk of downtime caused by an attack, keeping your business running smoothly.
How Network Security Hardware Works with Software
While network security hardware is vital, it works even better when paired with software solutions. Software, such as antivirus programs or firewalls, adds another layer of protection. Together, hardware and software make sure your network is secure from both simple and complex attacks.
For example, a hardware firewall blocks suspicious traffic, while antivirus software scans files for viruses. Both work together to give your network strong, all-around protection.
2. Types of Network Security Hardware
There are several types of network security hardware that help keep networks safe from threats. Each type has a specific role in protecting your network. Let’s explore the most common types of hardware and how they work.
Firewalls: The First Line of Defense
A firewall is one of the most well-known pieces of network security hardware. It acts as a barrier between your network and the outside world, allowing only safe traffic to pass through.
- How it works: Firewalls monitor all incoming and outgoing data. They block harmful or unauthorized traffic while allowing safe traffic to pass. Think of a firewall like a gatekeeper for your network.
- Why it’s important: Without a firewall, your network is open to all types of cyberattacks. A firewall is the first step to keeping your network secure.
Intrusion Detection and Prevention Systems (IDS/IPS)
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are essential for spotting and stopping attacks on your network.
- How they work: IDS monitors your network for any suspicious activity, while IPS goes one step further by automatically stopping potential threats.
- Why they’re important: IDS and IPS provide an extra layer of security. They can detect unusual patterns that might signal a cyberattack and act fast to block the threat.
VPN Routers: Secure Remote Access
VPN (Virtual Private Network) routers are important for businesses that have remote workers or need secure connections between offices.
- How it works: A VPN router allows employees to connect to your business network from anywhere, securely. It encrypts data so that it can’t be intercepted by hackers.
- Why it’s important: In today’s world, where many people work from home, having a secure way to access the company network is essential. VPN routers ensure that all data transferred over the internet remains private and secure.
Unified Threat Management (UTM) Appliances
A Unified Threat Management (UTM) appliance combines multiple security functions into one device. It often includes a firewall, IDS/IPS, VPN, and more.
- How it works: UTM appliances provide all-around protection by combining several security tools in one piece of hardware. They simplify network security management by offering everything in one place.
- Why it’s important: For businesses that want a complete security solution without managing multiple devices, UTM appliances are an excellent option.
Network Access Control (NAC) Devices

Network Access Control (NAC) devices are used to control who can access your network.
- How it works: NAC devices check the identity of anyone trying to connect to the network. They ensure that only authorized users and devices can get in.
- Why it’s important: NAC devices help prevent unauthorized access to your network, reducing the risk of insider threats and keeping sensitive data safe.
3. How to Choose the Right Network Security Hardware
Choosing the right network security hardware for your business is crucial to ensuring your network is safe and secure. In this chapter, we’ll guide you through the steps to select the best hardware for your specific needs.
Factors to Consider: Speed, Scalability, and Cost
When selecting network security hardware, there are several key factors to keep in mind:
- Speed: The hardware you choose must handle the amount of data traffic your network generates. If your security hardware is too slow, it could bottleneck your network, causing delays in data transfer. Make sure to choose hardware that can keep up with your network’s speed.
- Scalability: As your business grows, so will your network. You need security hardware that can scale up with your business. This means selecting devices that can easily expand to cover more users, devices, and data without requiring a complete overhaul of your system.
- Cost: Budget is always a consideration when making a purchase. While you don’t want to compromise on security, it’s important to find hardware that fits within your financial limits. Compare options based on both upfront cost and long-term maintenance expenses.
Network Security Hardware vs. Software Solutions
There’s often a debate about whether hardware or software solutions are better for network security. Both have their advantages, but here’s a comparison to help you decide:
- Hardware solutions: These are physical devices like firewalls and UTM appliances. They provide robust security and can handle large-scale attacks more effectively than software alone. However, they require regular maintenance and updates, which can be costly.
- Software solutions: Security software can be installed on computers and servers to provide protection. These are generally easier to update and cheaper than hardware. However, they may not be as effective in large networks or against more sophisticated attacks.
The best approach: For most businesses, a combination of both hardware and software solutions works best. Hardware provides strong defense at the network level, while software adds extra protection for individual devices.
Evaluating Compatibility with Existing Systems
When choosing new network security hardware, it’s essential to ensure it will work well with the systems you already have in place. Here’s how to check for compatibility:

- Network Infrastructure: Ensure the hardware integrates seamlessly with your current routers, switches, and servers. The new device should be able to communicate smoothly with other components of your network.
- Software Integration: If you are using specific security software or monitoring tools, make sure the hardware can support them. Some hardware may come with built-in software, but it should still allow you to use other tools you rely on.
- Ease of Deployment: If your business has limited IT resources, choose hardware that is easy to set up and maintain. Some devices offer plug-and-play functionality, making them easy to install without needing extensive technical expertise.
Balancing Security Needs and Business Goals
Lastly, when selecting network security hardware, balance your business’s security needs with its goals. If your business handles sensitive data (like financial or health records), you will need stronger, more expensive security hardware. On the other hand, small businesses with fewer resources might opt for more affordable solutions that provide adequate security.
- High-Security Needs: Businesses that deal with sensitive customer information should invest in advanced network security hardware such as UTM appliances, IDS/IPS systems, and encrypted VPN routers.
- Standard Security Needs: Small businesses that don’t handle highly sensitive data can often get by with simpler, more affordable hardware solutions like basic firewalls and VPN routers. Top Brands in Network Security
4. Top Brands in Network Security Hardware

When it comes to network security hardware, choosing the right brand is just as important as selecting the right device. There are several well-known brands in the industry that provide reliable and effective security solutions for businesses of all sizes. In this chapter, we’ll cover the top brands you should consider when investing in network security hardware.
Cisco: Leading in Network Security Hardware
Cisco is one of the biggest names in network security hardware. It is known for providing high-quality, reliable devices that cater to both small businesses and large enterprises.
- Why Cisco? Cisco offers a wide range of security solutions, including firewalls, routers, and advanced security appliances. Their products are designed to protect against various types of cyber threats, including malware, phishing, and unauthorized access. Cisco also offers excellent customer support, which is important for businesses that need help setting up or maintaining their hardware.
- Popular Cisco Products:
- Cisco ASA Firewalls: These firewalls provide strong protection against network attacks and are commonly used by businesses of all sizes.
- Cisco Meraki: A cloud-managed security solution that combines hardware with cloud-based monitoring and management, perfect for businesses looking for ease of use.
Fortinet: Trusted Security Hardware Solutions
Fortinet is another top player in the world of network security hardware. Known for its high-performance firewalls and comprehensive security solutions, Fortinet is a go-to choice for businesses looking for affordable yet powerful protection.
- Why Fortinet? Fortinet is particularly well-known for its FortiGate firewalls, which provide excellent protection against a wide range of cyber threats. Fortinet also offers unified threat management (UTM) solutions, combining multiple security functions in one device, making it a great choice for businesses that need all-in-one protection.
- Popular Fortinet Products:
- FortiGate Firewalls: These firewalls are known for their speed, scalability, and ability to handle advanced threats like ransomware and botnets.
- FortiWiFi: A wireless firewall solution that combines security with WiFi connectivity, perfect for small businesses or remote offices.
Palo Alto Networks: Innovative Security Devices
Palo Alto Networks is a newer but highly innovative player in the network security hardware space. They are known for pushing the boundaries of traditional network security with their next-generation firewalls and security appliances.
- Why Palo Alto Networks? Palo Alto’s firewalls offer advanced features such as application-level monitoring, threat detection powered by AI, and cloud-based management. These features make Palo Alto Networks a popular choice for businesses that need cutting-edge security.
- Popular Palo Alto Products:
- Palo Alto Next-Generation Firewalls: These firewalls go beyond simple traffic monitoring, providing deep packet inspection and integrated threat intelligence to stop sophisticated cyberattacks.
- Prisma Cloud: Palo Alto’s cloud security platform that integrates with their hardware to provide seamless protection for businesses that rely on cloud-based operations.
Check Point and Sophos: Reliable Security Hardware Brands
Both Check Point and Sophos are widely trusted names in network security hardware. They offer robust, reliable devices that protect businesses from a wide range of threats.
Sophos Intercept X: A powerful anti-ransomware solution that works with their hardware to provide full protection against modern threats.
Why Check Point? Check Point provides advanced firewall technology, intrusion prevention, and network segmentation, all in one package. Their hardware is easy to set up and manage, making it a popular choice for small to medium-sized businesses.
Popular Check Point Products:
Check Point Firewalls: Known for their simplicity and effectiveness, these firewalls are a great choice for businesses that need strong security without complicated setups.
SandBlast: A threat detection solution that works with Check Point firewalls to stop malware before it enters the network.
Why Sophos? Sophos offers strong security hardware combined with easy-to-use management software. Their focus on simplicity makes them ideal for small and medium-sized businesses that need robust protection without the need for a large IT team.
Popular Sophos Products:
Sophos XG Firewalls: These firewalls are known for their advanced threat detection capabilities and simple management interface, perfect for small businesses.
5. Network Security Hardware for Small and Medium Enterprises (SMEs)
Small and medium-sized enterprises (SMEs) face unique challenges when it comes to securing their networks. With fewer resources and smaller IT teams compared to large corporations, they need network security hardware that is both affordable and easy to manage. However, they still require strong protection to defend against growing cyber threats. In this chapter, we’ll explore the best network security hardware solutions for SMEs and how they can benefit your business.
Affordable Network Security Hardware for SMEs

Budget is often a major concern for small and medium businesses. While SMEs may not have the same financial flexibility as larger companies, it’s still possible to find affordable security hardware that provides robust protection. Here are some affordable options that won’t compromise security:
- Entry-Level Firewalls: Basic firewalls from brands like Cisco, Fortinet, and Sophos offer strong protection without the high cost. These firewalls can monitor and block unauthorized traffic, ensuring that your network stays secure.
- Unified Threat Management (UTM) Appliances: UTM devices are great for SMEs because they combine multiple security functions into one device, such as firewalls, VPN, and antivirus. This all-in-one solution is cost-effective and easy to manage. Fortinet’s FortiGate UTM and Sophos UTM are popular choices for small businesses.
- VPN Routers: For SMEs that have remote workers or multiple offices, VPN routers ensure that data is transferred securely between locations. VPN routers can be relatively inexpensive and provide essential encryption to protect sensitive data.
Scalable Options for Growing Networks
As small businesses grow, their security needs also increase. One of the key factors to consider when choosing network security hardware is scalability. It’s important to invest in solutions that can grow alongside your business without requiring costly upgrades every few years.
Here’s how SMEs can ensure they have scalable solutions:
- Modular Firewalls: Some firewalls offer modular designs, allowing businesses to add features as they grow. For example, Cisco offers firewalls that let you add advanced features like intrusion prevention and VPN capabilities over time, meaning you don’t have to buy a new firewall as your business expands.
- Cloud-Managed Security: Cloud-based security solutions are another scalable option for SMEs. Devices like Cisco Meraki and Fortinet Cloud allow businesses to manage their security hardware remotely. These cloud-based platforms are easy to scale as the number of users or offices increases, making them ideal for businesses looking to expand.
- Network Access Control (NAC) Devices: As businesses grow, so does the number of devices connected to the network. NAC devices ensure that only authorized users and devices can access the network, keeping it secure even as the network grows in size. NAC devices are scalable and easy to integrate into growing networks.
Why SMEs Need Strong Network Security Hardware
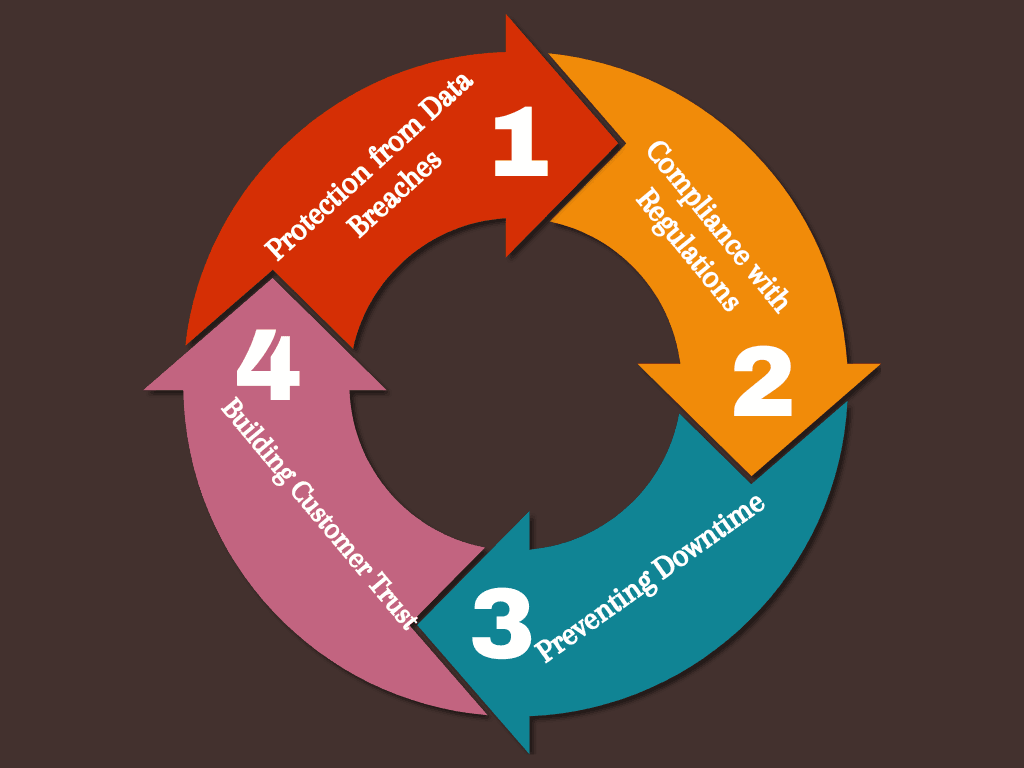
Many small and medium-sized businesses underestimate their need for strong network security. Some believe that because they are smaller, they aren’t likely to be targeted by cybercriminals. However, this isn’t true. In fact, SMEs are often targeted because they tend to have weaker security defenses. Here are a few reasons why strong network security hardware is essential for SMEs
- Protection from Data Breaches: Even a small data breach can cause significant financial and reputational damage to an SME. Cybercriminals often target small businesses to steal customer data, such as credit card information or personal details. Strong security hardware like firewalls and VPN routers helps protect this sensitive data from being stolen.
- Compliance with Regulations: Many industries, such as healthcare, finance, and e-commerce, have regulations that require businesses to protect customer data. Failing to comply with these regulations can lead to fines and legal issues. Using the right network security hardware ensures your business complies with industry standards and avoids penalties.
- Preventing Downtime: Cyberattacks can cause your network to go down, leading to lost productivity and revenue. For small businesses, even a few hours of downtime can have a serious impact. Strong network security hardware can prevent attacks and keep your business running smoothly.
- Building Customer Trust: Customers want to know that their data is safe with you. By investing in robust network security hardware, you can show your customers that you take their security seriously. This helps build trust and can even be a selling point for your business.
Simple Management for SMEs
Another important consideration for SMEs is ease of management. Many small businesses don’t have dedicated IT staff, so they need security hardware that is easy to set up and maintain. Here are a few tips for finding hardware that is simple to manage:
- Choose Devices with Simple Setup: Some network security hardware is designed for easy installation. Look for devices with plug-and-play functionality or step-by-step setup guides that can be managed by non-technical staff.
- Cloud-Based Management: Cloud-managed security hardware allows businesses to control and monitor their security devices from anywhere. This is a great option for SMEs that don’t have on-site IT staff. Products like Cisco Meraki and Fortinet Cloud offer user-friendly dashboards for easy management.
6. Benefits of Using Network Security Hardware
Investing in network security hardware is one of the best ways to protect your business from cyber threats. Security hardware offers many benefits that help keep your network safe, monitor activity, and ensure compliance with regulations. In this chapter, we’ll explore the key benefits of using network security hardware and how it can improve your overall business security.
Protection Against External Threats
One of the biggest benefits of network security hardware is its ability to block external threats such as hackers, viruses, and malware. Cyberattacks can target businesses of all sizes, but with the right hardware in place, you can protect your network from these dangers.
Here are some ways network security hardware protects against external threats:
- Firewalls: Firewalls act as the first line of defense by monitoring incoming and outgoing traffic. They block unauthorized access and prevent harmful data from entering your network.
- Intrusion Detection Systems (IDS): IDS hardware detects suspicious activity on your network, such as hacking attempts, and alerts your IT team so they can take action.
- Intrusion Prevention Systems (IPS): IPS hardware goes a step further by automatically blocking potential threats as soon as they are detected, stopping attacks before they can cause damage.
By blocking these threats at the network level, security hardware helps prevent data breaches, ransomware attacks, and other cybercrimes that can harm your business.
Monitoring and Managing Network Traffic
Another key benefit of network security hardware is its ability to monitor and manage the flow of data across your network. This allows you to have better control over what is happening on your network at any given time.
- Real-Time Monitoring: Many network security devices, like firewalls and unified threat management (UTM) appliances, offer real-time monitoring. This means they can track traffic in and out of your network and flag any unusual activity.
- Traffic Management: Security hardware can also prioritize network traffic, ensuring that critical business applications get the bandwidth they need. This can improve the performance of your network, especially during times of heavy traffic.
- Logging and Reporting: Security hardware often comes with built-in logging and reporting features, allowing your team to analyze traffic patterns, detect potential threats, and track user activity. These reports can be valuable for understanding your network’s security and identifying areas that need improvement.
Enhancing Data Privacy and Compliance
Businesses today are under more pressure than ever to protect customer data and comply with privacy regulations. Network security hardware can help your business meet these requirements by providing an extra layer of protection for sensitive data.
Here’s how security hardware enhances data privacy and ensures compliance:
- Encryption: Many network security devices include encryption features, which secure your data by making it unreadable to unauthorized users. This is especially important for businesses that handle sensitive information like credit card numbers or medical records.
- Access Control: Network security hardware can control who has access to different parts of your network. By using Network Access Control (NAC) devices, you can ensure that only authorized users can connect to the network, helping prevent insider threats.
- Meeting Regulatory Requirements: Many industries, such as healthcare and finance, have strict regulations regarding data security. Network security hardware helps businesses comply with these rules by ensuring that sensitive data is protected from breaches.
By using network security hardware, you can ensure that your business meets legal requirements while keeping customer data safe.
Preventing Downtime and Improving Productivity
Cyberattacks can lead to network downtime, which can be costly for businesses. When your network is down, employees can’t access the tools or data they need to do their jobs, resulting in lost productivity and revenue.
- Reducing Downtime: Network security hardware can detect and block attacks before they cause damage, preventing downtime and keeping your business running smoothly.
- Ensuring Business Continuity: With strong security measures in place, you can minimize the risk of disruptions caused by cyberattacks. This ensures that your network is always available, allowing employees to stay productive and customers to access your services without interruption.
Building Trust with Customers
In today’s digital age, customers are becoming more aware of data privacy and security. They want to know that their personal information is safe when they do business with you. By investing in network security hardware, you can show your customers that you take their security seriously.
Boosting Customer Confidence: When customers know that your business has strong security measures in place, they are more likely to trust you with their data. This can be a key selling point, especially for businesses that handle sensitive information.
Protecting Customer Data: Network security hardware helps protect customer data from breaches, keeping their personal information safe from hackers and cybercriminals.
7. Advanced Features in Modern Network Security Hardware
As technology evolves, so do the capabilities of network security hardware. Today’s devices offer advanced features that provide businesses with stronger protection and better control over their networks. In this chapter, we’ll explore some of the most important modern features of network security hardware and how they benefit your business.
AI-Powered Threat Detection and Response
One of the biggest advancements in network security hardware is the integration of artificial intelligence (AI). AI-powered systems can detect and respond to cyber threats more quickly and accurately than traditional security measures.
- How AI Works in Security Hardware: AI-based systems analyze patterns in network traffic and user behavior to identify unusual activities. These systems can learn from past attacks and use this knowledge to detect new threats, even if they haven’t been encountered before.
- Benefits of AI: AI-powered security hardware provides faster threat detection, often identifying potential risks before they cause harm. This proactive approach helps businesses stop attacks in real-time, reducing the risk of data breaches and network disruptions.
- Example: Palo Alto Networks’ next-generation firewalls use AI to detect unknown malware and prevent attacks based on patterns of behavior, rather than relying on a database of known threats.
Cloud-Based Security Management Integration
Cloud technology is transforming the way businesses manage their networks. Many modern network security devices now offer cloud-based management, making it easier for businesses to monitor and control their networks remotely.
- How Cloud-Based Management Works: Instead of managing security hardware locally, businesses can use cloud-based platforms to control their devices from anywhere. This is especially helpful for businesses with multiple offices or remote workers.
- Benefits of Cloud Integration:
- Remote Monitoring: Cloud-based platforms allow IT teams to monitor network activity and respond to security threats from any location.
- Simplified Management: With cloud integration, businesses can manage multiple security devices through a single dashboard. This makes it easier to update settings, apply security patches, and view real-time reports.
- Example: Cisco Meraki offers cloud-based network security management, allowing businesses to easily manage firewalls, routers, and other security devices from a web-based platform.
Encryption and VPN Support for Secure Communication
In today’s world, secure communication is essential, especially for businesses with remote workers or those handling sensitive data. Modern network security hardware often comes with encryption and VPN (Virtual Private Network) support to ensure that all data transmitted across the network is secure.
- Encryption: Encryption ensures that data is converted into a code to prevent unauthorized access. Many network security devices now include encryption features that protect data both while it’s stored and when it’s being transmitted.
- VPN Support: VPNs create a secure, encrypted connection between users and the business network, making it harder for cybercriminals to intercept data. Many modern routers and firewalls come with built-in VPN support, making it easy for businesses to set up secure remote connections for employees.
- Benefits of Encryption and VPN:
- Data Security: Encryption and VPNs help protect sensitive data, such as financial information or customer records, from being intercepted by hackers.
- Privacy: VPNs ensure that remote workers can securely access company data without the risk of cyberattacks, providing a safe connection for employees working from home.
- Example: Fortinet’s firewalls come with built-in VPN support and encryption features, providing secure data transmission for businesses of all sizes.
Multi-Layered Security for Comprehensive Protection
Many modern network security devices offer multi-layered security solutions, combining several protective features into one device. This provides businesses with comprehensive protection without the need for multiple pieces of hardware.
- Unified Threat Management (UTM): UTM appliances combine firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), antivirus, and VPN support into one device. This all-in-one solution simplifies network security management while offering strong protection.
- Next-Generation Firewalls (NGFW): NGFWs go beyond traditional firewalls by providing deep packet inspection, application awareness, and integration with cloud security. They can analyze data packets in greater detail, stopping more advanced threats.
- Benefits of Multi-Layered Security:
- Simplified Management: By combining multiple security functions into one device, businesses can manage their network security more easily.
- Stronger Protection: Multi-layered security offers protection at different levels, ensuring that your network is safe from various types of attacks.
- Example: FortiGate UTM appliances provide multi-layered security by combining firewall, IDS/IPS, VPN, and antivirus features in one device, making it ideal for small and medium businesses.
8. Installation and Maintenance of Network Security Hardware
Setting up and maintaining network security hardware is a crucial step in protecting your business from cyber threats. Proper installation and regular maintenance ensure that your security devices are working effectively and up to date with the latest security standards. In this chapter, we’ll cover best practices for installing and maintaining network security hardware to keep your network safe
Best Practices for Setup and Configuration
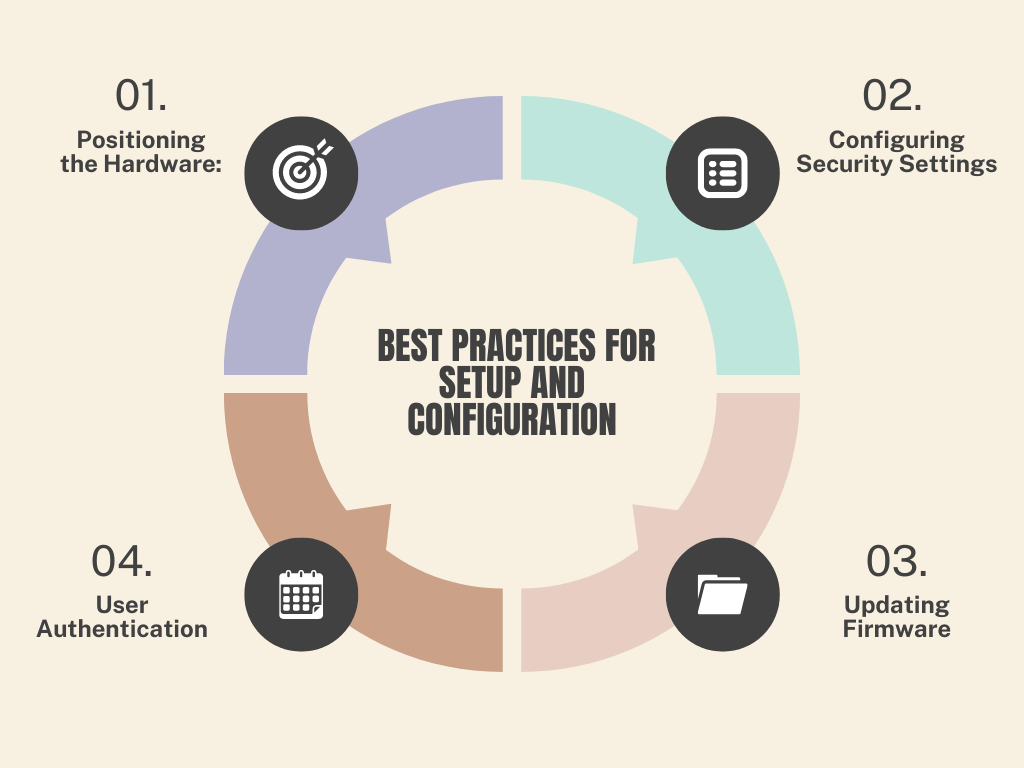
Installing network security hardware can seem like a complicated task, but following best practices will make the process smoother and more effective. Here are some key steps to ensure your security devices are set up properly:
- Positioning the Hardware:
- Make sure that firewalls and other security devices are positioned at the network’s perimeter. This ensures that they can monitor all incoming and outgoing traffic.
- For businesses with multiple locations, consider placing additional security hardware at each location to protect local networks.
- Configuring Security Settings:
- Once the hardware is installed, it’s important to configure the settings correctly. Default settings are often too weak, so customize firewall rules to block unnecessary ports and restrict access based on your business needs.
- Set up encryption and VPNs (if available) to protect data in transit. This is especially important for businesses with remote workers or multiple office locations.
- Updating Firmware:
- Security hardware manufacturers regularly release firmware updates to address vulnerabilities and improve performance. Always update your hardware’s firmware during installation to ensure that it’s protected against the latest threats.
- User Authentication:
- Set up strong user authentication methods, such as two-factor authentication (2FA), to control access to your security hardware. This adds an extra layer of security and prevents unauthorized individuals from changing settings or accessing sensitive data.
Regular Updates and Patching for Enhanced Security
Even after your network security hardware is installed, keeping it up to date is critical for maintaining a secure network. Cyber threats evolve over time, so regular updates and patches help protect your network from new vulnerabilities.
- Firmware Updates:
Firmware updates are essential for fixing bugs, patching vulnerabilities, and improving performance. Make it a habit to regularly check for updates from your hardware provider and install them as soon as possible. - Security Patches:
Security patches are designed to fix specific vulnerabilities that could be exploited by hackers. Many hardware vendors release patches in response to newly discovered threats, so it’s important to stay informed and apply these patches as they become available. - Automated Updates:
Some modern security hardware offers automated updates, which ensure that your devices always have the latest security features and patches without requiring manual intervention. If your hardware supports this feature, enable it to streamline the update process.
Monitoring Network Health and Performance
Regular monitoring of your network’s health and performance is a key part of maintaining your security hardware. This helps you spot potential issues early and take action before they cause significant problems.
- Real-Time Monitoring:
Many network security devices offer real-time monitoring features, allowing you to track traffic and detect suspicious activity. Use these tools to keep an eye on your network and respond to any unusual behavior immediately. - Performance Monitoring:
Security hardware can impact your network’s performance, especially if it’s not configured properly or if it’s outdated. Monitor the performance of your devices to ensure they’re running efficiently and not slowing down your network. - Logging and Reporting:
Most network security hardware provides logging and reporting features that track network activity, security incidents, and performance metrics. Review these logs regularly to identify trends, potential vulnerabilities, and areas where security can be improved.
Scheduling Regular Maintenance
Just like any other piece of technology, network security hardware needs regular maintenance to keep it running smoothly. Here’s a basic maintenance checklist to follow:
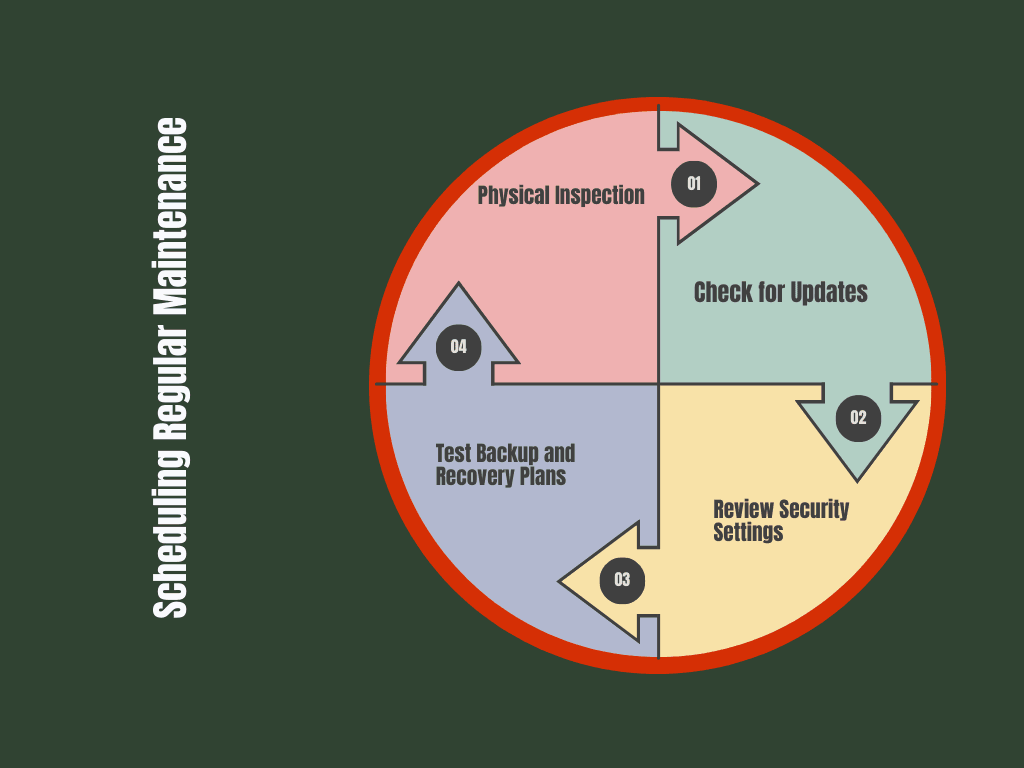
1 Physical Inspection:
For on-premise security hardware, occasionally check the physical condition of your devices. Dust, overheating, or loose cables can affect performance and should be addressed immediately.
2 Check for Updates:
Schedule regular checks for firmware updates and patches. This should be done at least once a month or whenever a new threat is reported by your hardware provider.
3 Review Security Settings:
Over time, your business’s needs may change, and so should your security settings. Periodically review your firewall rules, access controls, and encryption protocols to ensure they still meet your security requirements.
4 Test Backup and Recovery Plans:
If a cyberattack or hardware failure occurs, having a backup and recovery plan in place is essential. Regularly test your backup systems to ensure they are working properly and can restore your network in case of an emergency.
9. Future Trends in Network Security Hardware
As technology continues to evolve, so do the threats and challenges businesses face in protecting their networks. To keep up with these changes, network security hardware is constantly advancing with new features and capabilities. In this chapter, we’ll explore some of the most exciting trends shaping the future of network security hardware and how businesses can prepare for these developments.
The Role of AI and Machine Learning in Network Security
One of the most significant trends in network security is the increasing use of artificial intelligence (AI) and machine learning (ML) to detect and prevent cyber threats. AI and ML can analyze vast amounts of data and identify patterns that humans might miss, making them powerful tools for improving network security.
- How AI and ML Work in Security Hardware: AI-powered systems can detect abnormal network behavior, identify potential threats, and automatically respond to security incidents. Machine learning algorithms continuously improve by learning from past events, allowing them to recognize new and emerging threats.
- Benefits of AI and ML in Security:
- Faster Threat Detection: AI and ML can analyze network traffic in real-time, detecting and responding to threats faster than traditional security methods.
- Predictive Security: These systems can anticipate potential risks based on historical data, enabling businesses to take preventative measures before an attack occurs.
- Example: AI-powered firewalls, such as those offered by Palo Alto Networks, use machine learning to identify and block unknown malware and sophisticated attacks that would otherwise go undetected.
Integration with Cloud Security Platforms

As more businesses move their operations to the cloud, the need for cloud-integrated network security hardware has grown. Many modern security devices now offer seamless integration with cloud platforms, providing businesses with centralized security management and enhanced visibility across their network.
- Cloud-Based Security Solutions: Cloud-integrated hardware allows businesses to monitor, manage, and protect both on-premises and cloud environments from a single platform. This makes it easier to enforce consistent security policies across all locations and devices.
- Benefits of Cloud Integration:
- Centralized Management: With cloud integration, businesses can manage multiple security devices, even across different geographic locations, through a single dashboard.
- Scalability: Cloud-integrated security systems can scale more easily as a business grows, ensuring that security measures can keep up with increasing network demands.
- Example: Cisco Meraki is a popular cloud-managed network security solution, offering firewalls, VPNs, and other security features that can be controlled through a web-based platform.
The Impact of IoT on Network Security Hardware
The rise of the Internet of Things (IoT) presents new challenges for network security. As more devices—such as smart sensors, cameras, and appliances—connect to the internet, they create new entry points for cybercriminals. To address these risks, network security hardware is evolving to include advanced IoT protection.
- Challenges of IoT Security: Many IoT devices have limited security features, making them vulnerable to attacks. Network security hardware must now include features that can monitor and secure a growing number of connected devices.
- IoT Security Features in Modern Hardware:
- Device Identification and Monitoring: New security hardware can automatically detect and monitor IoT devices on the network, identifying any suspicious activity.
- Segmentation: Network segmentation ensures that IoT devices are isolated from critical parts of the network, limiting the damage if a device is compromised.
- Example: Fortinet offers IoT security solutions that integrate with their network security hardware, providing visibility and protection for all connected devices.
Zero Trust Architecture and Network Security Hardware
The Zero Trust model is gaining traction as a critical approach to network security. In a Zero Trust architecture, no user or device is automatically trusted—every request for access must be verified. This model is being implemented through advancements in network security hardware.
- How Zero Trust Works: Zero Trust architecture requires constant verification of users and devices, regardless of whether they are inside or outside the network. Network security hardware plays a key role in enforcing these policies, by using tools like firewalls, NAC devices, and identity verification systems.
- Benefits of Zero Trust:
- Stronger Access Control: Zero Trust ensures that only verified users and devices can access sensitive parts of the network.
- Reduced Risk of Breaches: By constantly verifying access, Zero Trust minimizes the risk of unauthorized users gaining access to critical systems.
- Example: Many next-generation firewalls now support Zero Trust policies by integrating identity verification features and access controls that limit who can access different parts of the network.
5G and the Future of Network Security Hardware
The rollout of 5G technology will bring faster network speeds and lower latency, but it also introduces new security challenges. As 5G networks expand, businesses will need more advanced network security hardware to protect against the risks associated with this new technology.
- How 5G Impacts Network Security: With 5G, networks will be able to handle more connected devices and transfer data at faster speeds. This increases the risk of cyberattacks, as more data is being transmitted, and attackers can exploit new vulnerabilities in the infrastructure.
- Security Solutions for 5G:
- Edge Security: Network security hardware will need to be placed closer to the edge of the network to monitor traffic and protect data as it moves between devices.
- Advanced Encryption: Faster networks will require stronger encryption methods to ensure that data remains secure during transmission.
- Example: Companies like Fortinet are already developing security hardware designed to protect 5G networks, offering edge firewalls and secure access solutions that safeguard against 5G-specific threats.
Difference between Firewall and Intrusion Detection System (IDS)
| Feature | Firewall | Intrusion Detection System (IDS) |
|---|
| Primary Function | Blocks and controls incoming/outgoing network traffic | Monitors network traffic for suspicious activity |
| Proactive or Reactive | Proactive – blocks threats before they enter the network | Reactive – detects threats after they have occurred |
| Placement in Network | Positioned at the network’s perimeter to filter traffic | Positioned inside the network to monitor internal activity |
| Action on Threats | Actively blocks unauthorized access or harmful data | Alerts administrators of potential threats |
| Best Used For | Preventing external attacks like malware and unauthorized access | Detecting internal threats or malicious behavior |
FAQs
What is Network Security Hardware?
Network security hardware consists of physical devices like firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and VPN routers designed to protect a network from unauthorized access, cyberattacks, and data breaches. These devices monitor and control traffic, ensuring that only safe and authorized data flows through the network.
Why is Network Security Hardware important for businesses?
Network security hardware is essential for protecting sensitive data, preventing cyberattacks, and ensuring business continuity. It acts as a barrier against external threats like malware, hackers, and unauthorized access. Businesses also rely on these devices to comply with industry regulations regarding data security.
What’s the difference between Network Security Hardware and Software?
Network security hardware refers to physical devices (e.g., firewalls, VPN routers) installed in a network to protect it from attacks. In contrast, network security software (e.g., antivirus, firewall programs) is installed on individual devices like computers or servers to protect those specific systems. Both work together to provide comprehensive security.
Can Network Security Hardware protect against all cyber threats?
While network security hardware provides strong protection against many cyber threats, it’s most effective when combined with security software solutions. No single device can protect against every threat, so it’s important to use a layered security approach that includes firewalls, antivirus software, intrusion prevention, and encryption.
How often should Network Security Hardware be updated?
Network security hardware should be regularly updated with firmware upgrades and security patches to address new vulnerabilities and threats. It’s a good practice to check for updates at least once a month or whenever manufacturers release new updates to ensure your hardware remains effective against the latest cyber threats.
Conclusion
Network security hardware plays a critical role in safeguarding business networks from cyber threats. It includes devices like firewalls, VPN routers, and intrusion detection/prevention systems (IDS/IPS), providing protection against unauthorized access, malware, and data breaches. By monitoring and controlling data traffic, these hardware solutions prevent hackers from infiltrating your network. Businesses benefit from enhanced security, better network performance, and compliance with industry regulations. As cyberattacks become more frequent and sophisticated, investing in robust network security hardware is essential for maintaining business continuity, protecting sensitive data, and building customer trust.
