Introduction to Information Security and Cyber Safety
In today’s digital world, information security and cyber safety are more critical than ever. Information security refers to protecting information from unauthorized access, alteration, and destruction, while cyber safety involves protecting users, especially on the internet, from cyber threats.
Whether it’s safeguarding personal data or preventing cyberattacks in organizations, these two fields are essential to ensure the digital environment remains safe. Both individuals and businesses need to understand the importance of cyber safety as threats grow more sophisticated every day.
Core Principles of Information Security
Information security revolves around three core principles, often called the CIA Triad.
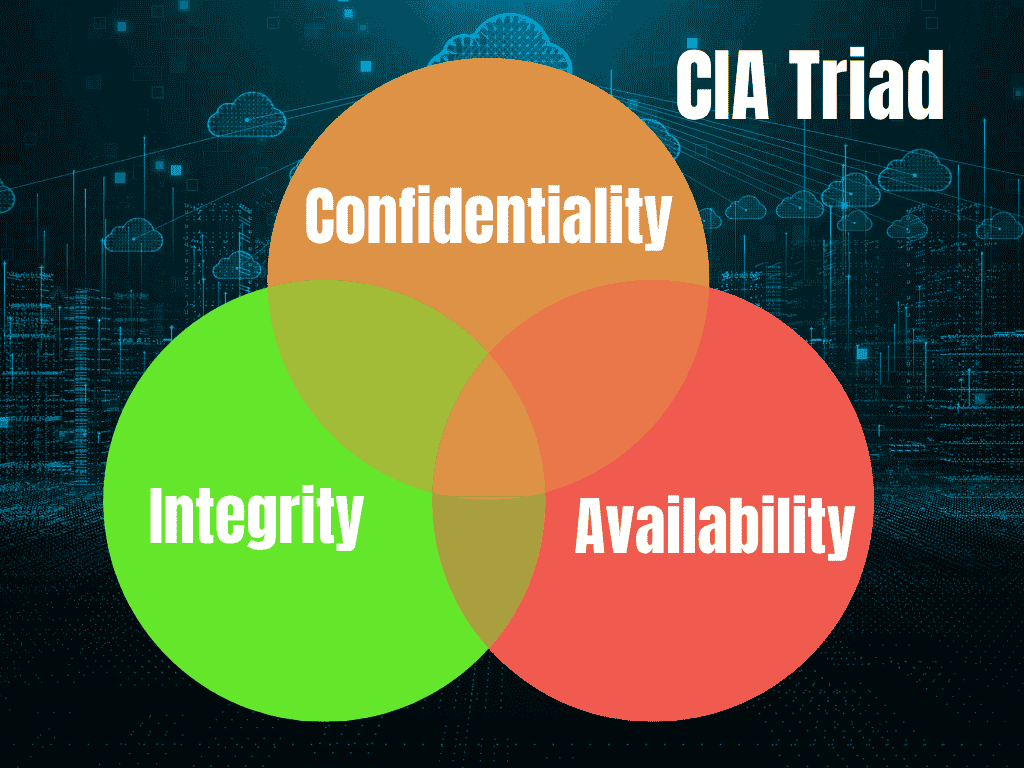
- Confidentiality: Confidentiality guarantees that sensitive data is accessible exclusively to authorized individuals.
- Integrity: Protects the accuracy and completeness of data. It prevents data from being tampered with by unauthorized sources.
- Availability: Ensures that information is available when authorized users need it. To enhance security, organizations implement authentication, authorization, and accountability. Authentication confirms the user’s identity, while authorization ensures they have the correct permissions. Accountability keeps track of actions and holds individuals responsible for their actions.
Cyber Safety Essentials
In addition to securing information, cyber safety focuses on safe practices when using the internet. Here are some essential tips for individuals and organizations
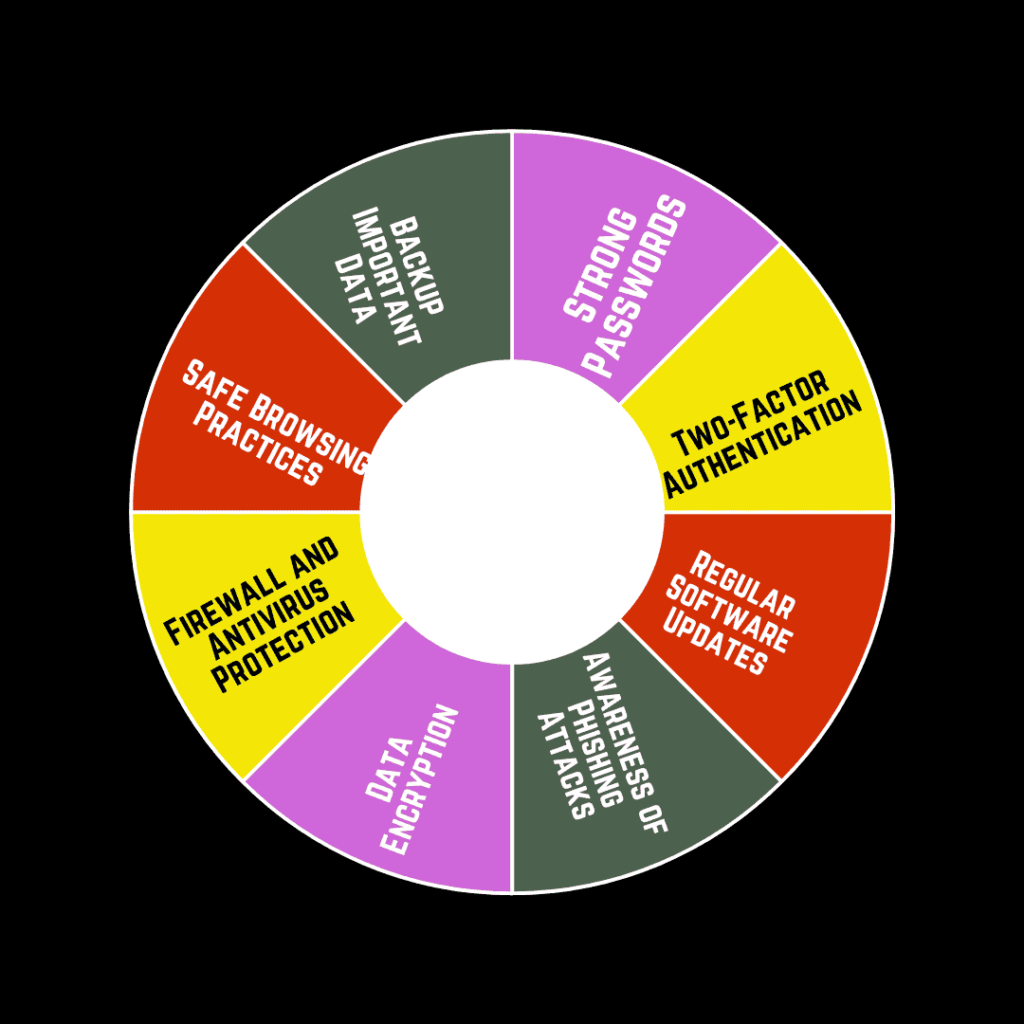
Strong Passwords
- Use complex passwords that include a mix of letters (upper and lower case), numbers, and special characters.
- Avoid using easily predictable information such as birthdays or common phrases.
- Frequently update your passwords and ensure each account has a distinct one.
Two-Factor Authentication (2FA)
- Implement 2FA wherever possible to add an extra layer of security to your online accounts.
- This could involve receiving a code via SMS, using an authenticator app, or even biometric authentication (like fingerprints).
Regular Software Updates
- Keep your operating systems, applications, and antivirus software up to date to ensure they are protected against the latest threats.
- Many attacks exploit outdated software vulnerabilities.
Awareness of Phishing Attacks
- Be cautious when clicking on links or downloading attachments from unknown or suspicious emails and messages.
- Confirm the sender’s identity before disclosing any personal information.
Data Encryption
- Use encryption for sensitive data to protect it from unauthorized access.
- Enable encryption on devices (phones, laptops) and consider using encrypted messaging apps.
Firewall and Antivirus Protection
- Ensure that firewalls are active on your devices to block malicious traffic.
- Utilize trusted antivirus software to identify and eliminate possible threats.
Safe Browsing Practices
- Avoid visiting unsafe or suspicious websites and ensure that the websites you visit are secure (look for “HTTPS” in the URL).
- Consider using a VPN (Virtual Private Network) when browsing on public Wi-Fi to protect your internet connection.
Backup Important Data
- Regularly backup your important data to an external hard drive or a secure cloud service.
- In case of data loss due to cyber-attacks or system failure, this ensures that your information can be recovered.
Staying vigilant and keeping up with the latest cybersecurity trends is essential for maintaining your cyber safety in a world with ever-evolving digital threat
Network and Device Security
A vital part of cyber safety is ensuring that networks and devices are secure. Here are the best practices:
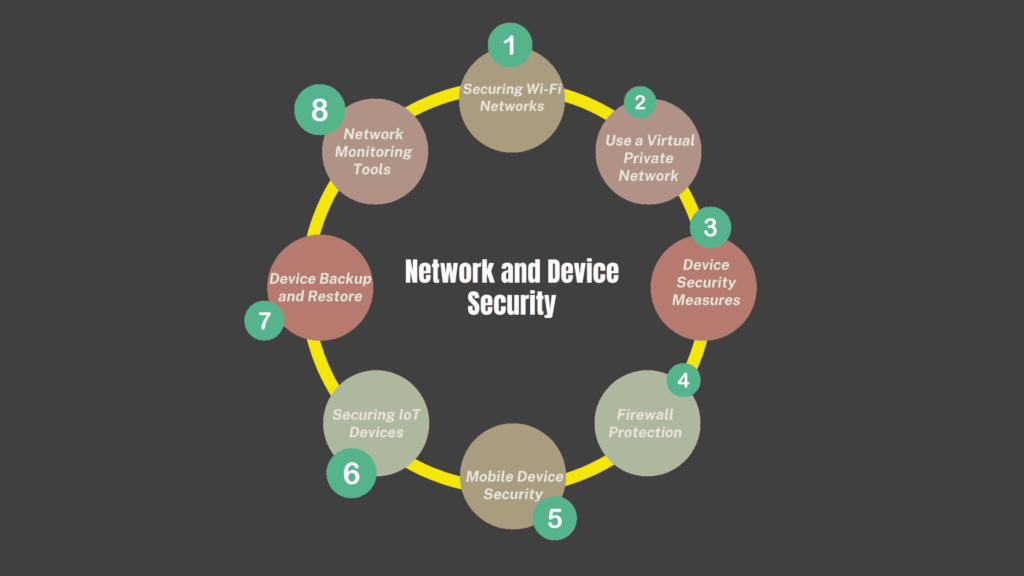
Securing Wi-Fi Networks
- Ensure your Wi-Fi network is protected with a strong, unique password to block unauthorized access.
- Consider disabling WPS (Wi-Fi Protected Setup), as it can introduce security vulnerabilities.
- Periodically check for firmware updates for your router to ensure it’s protected against known threats.
- Limit the number of connected devices to reduce potential attack vectors.
Use a Virtual Private Network (VPN)
- A VPN can help bypass geo-restrictions and access content safely from different regions.
- Make sure to choose a reliable VPN provider that does not log user activity.
- Use a VPN whenever connecting to unsecured public networks like coffee shops or airports.
- Always verify that the VPN connection is active before accessing sensitive data online.
Device Security Measures
- Lock your devices after a period of inactivity to protect against unauthorized access.
- Be cautious when connecting external storage devices, as they may contain malware.
- Regularly clear cached data and browsing history to minimize your digital footprint.
- Avoid jailbreaking or rooting your devices, as it can disable built-in security protections.
Firewall Protection
- Configure your firewall to block all incoming traffic except for trusted sources.
- Set up firewall rules based on the principle of least privilege, allowing only essential services.
- Use a firewall to monitor outbound traffic to detect any malicious activities from compromised devices.
- Check your firewall logs regularly to identify potential intrusion attempts or abnormal activity.
Mobile Device Security
- Always download apps from trusted sources such as Google Play or the Apple App Store.
- Use remote tracking features to locate your device if it gets lost or stolen.
- Periodically review app permissions and revoke access to those that are no longer necessary.
- Enable automatic updates for apps and system software to stay protected against vulnerabilities.
Securing IoT Devices
- Segment your IoT devices on a separate network to reduce exposure to cyber threats.
- Disable unused features or services on your IoT devices to minimize the attack surface.
- Use device-specific passwords rather than default credentials that are easier to compromise.
- Regularly review the devices connected to your network to ensure they are authorized.
Device Backup and Restore
- Test your backup system periodically to ensure the integrity of your backups.
- Use encrypted cloud storage for offsite backups, adding an extra layer of security.
- Maintain multiple backup copies to mitigate the risk of data loss from hardware failure.
- Automate your backup process to ensure it runs consistently without manual intervention.
8. Network Monitoring Tools
- Set up alerts for unusual login attempts or abnormal bandwidth usage on your network.
- Use deep packet inspection (DPI) tools to analyze network traffic for potential threats.
- Regularly audit your network security settings and access logs for unauthorized changes.
- Employ network segmentation to isolate sensitive data and reduce the impact of a breach.
These practices ensure a strong, multi-layered defense against cyber threats, promoting a secure environment for both personal and business use.
Data Privacy and Encryption
Data privacy refers to how data is collected, shared, and used, while encryption is the process of encoding information so only authorized parties can read it. Both are vital components of protecting sensitive information.
- Encryption: Encrypting sensitive data like financial information ensures that even if someone intercepts it, they can’t understand or use it.
- Protecting Personal Information: Be mindful of what information you share online, especially on social media or websites that require personal data.
Data privacy is an increasingly significant concern as more personal and financial activities shift online.
Cybersecurity Threats and Defenses
The rise of cyber threats has made it more important to understand the types of attacks and how to defend against them:
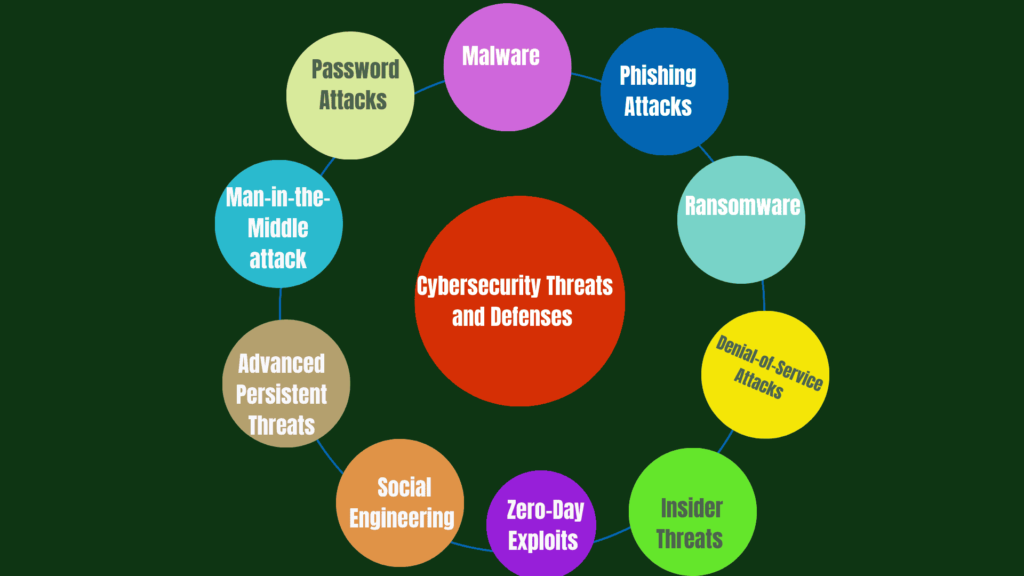
Malware
Malware includes various forms such as viruses, worms, spyware, and ransomware that aim to infiltrate, damage, or take control of systems. To defend against malware, it is essential to install and regularly update antivirus software, which can detect and eliminate potential threats. Additionally, it’s crucial to avoid downloading software or files from untrusted sources, as they may contain harmful malware. Enabling email filters can also block phishing emails, which often carry malware attachments designed to compromise your system.
Phishing Attacks
Phishing attacks deceive users into revealing sensitive information, like passwords or credit card details, by posing as legitimate entities. Always verify the sender’s email address and be cautious when clicking on links or downloading attachments. Educating employees and users about identifying phishing emails is another effective defense. Using email security solutions to filter out suspicious messages before they reach the inbox provides an additional layer of protection.
Ransomware
Ransomware is a type of malware that encrypts files and demands payment for their release, often causing significant data loss or exposure. To mitigate the effects of ransomware, regularly back up important data to offline storage solutions, so that recovery is possible without paying the ransom. Utilizing advanced anti-malware software can detect and block ransomware attacks before they encrypt your files. Keeping your operating systems and software updated helps patch known vulnerabilities exploited by ransomware.
Denial-of-Service (DoS) Attacks
Denial-of-Service (DoS) attacks overwhelm a network or server with excessive traffic, rendering it inaccessible to legitimate users. To defend against DoS attacks, use specialized DDoS protection services that can detect and mitigate abnormal traffic patterns. Rate-limiting techniques are also helpful, as they restrict traffic from unknown sources, reducing the impact of such attacks. Having an incident response plan in place ensures that your team can respond quickly and minimize downtime in case of an attack.
Insider Threats
Insider threats involve employees or trusted individuals intentionally or unintentionally causing harm to systems, resulting in data breaches or sabotage. Implementing strict access controls is a key defense, ensuring that employees can only access data relevant to their roles. Monitoring employee activity, especially on critical systems, helps in identifying suspicious behavior. Fostering a security-aware culture through regular training can prevent accidental leaks and malicious insider actions.
Zero-Day Exploits
Zero-day exploits take advantage of software vulnerabilities that are unknown to the vendor and remain unpatched, allowing unauthorized access or damage. Defending against zero-day exploits involves using intrusion detection and prevention systems (IDPS) that monitor for unusual behavior. Regularly updating software to apply the latest security patches is essential to close any discovered vulnerabilities. Endpoint detection and response (EDR) solutions can quickly detect and respond to such exploits, limiting potential damage.
Social Engineering
Social engineering manipulates individuals into divulging confidential information through deception or psychological tactics. To defend against social engineering, mandatory security awareness training is crucial to educate users on recognizing these tactics. Establish clear verification procedures before sharing sensitive information, especially over the phone or email. Implementing multi-factor authentication (MFA) adds an additional layer of protection, ensuring that even if credentials are compromised, unauthorized access is still prevented.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are prolonged, targeted attacks by skilled adversaries seeking to steal sensitive data or compromise networks over time. Network segmentation is a key defense, isolating critical systems and limiting an attacker’s ability to move laterally within the network. Continuous monitoring tools help detect any signs of persistent activity or intrusion. Regular penetration testing and vulnerability assessments ensure that weaknesses are identified and fixed before they can be exploited by attackers.
Man-in-the-Middle (MITM) Attacks
Man-in-the-Middle (MITM) attacks involve an attacker intercepting and altering communication between two parties to steal sensitive data. Strong encryption protocols, such as HTTPS and VPNs, are essential for securing communications and preventing interception. Network security measures, like firewalls and intrusion detection systems, are effective in detecting suspicious activity and stopping MITM attacks. Avoid using public Wi-Fi for sensitive transactions, or use a VPN to encrypt your traffic when you must connect to public networks.
Password Attacks
Password attacks involve attempts to gain unauthorized access by cracking or stealing passwords through brute force or credential stuffing. To defend against these attacks, it’s vital to use complex passwords that include a mix of letters, numbers, and special characters, and to change them regularly. Implementing two-factor authentication (2FA) adds a layer of security, making it harder for attackers to succeed even if a password is compromised. Password managers can help securely store and generate strong, unique passwords for every account, reducing the risk of reuse. Limiting the number of login attempts and using CAPTCHA can further prevent automated attacks like brute-force attempts.
Business Information Security
Businesses are often targeted by cyberattacks due to the valuable data they hold. To prevent attacks, organizations need to develop strong security policies
- Organizational Security Framework: Businesses must establish clear rules and policies to protect their data and networks. Regular audits ensure these policies are followed.
- Employee Training: Employees should be trained on best security practices, including recognizing phishing attempts and securing their devices.
- Disaster Recovery Plans: In case of a breach, businesses need a disaster recovery plan to restore lost data and resume normal operations.
- By creating a strong culture of cybersecurity, businesses can better protect themselves against potential threats.
Legal and Ethical Issues in Information Security
The rise of cyber threats has led to the implementation of cybersecurity laws and regulations that aim to protect data and privacy. Here are some key considerations:
Data Privacy and Protection
- Laws like GDPR and CCPA enforce strict regulations on data collection, storage, and sharing practices.
- Organizations must ensure compliance to avoid fines and legal penalties for mishandling data.
- Ethically, businesses should seek user consent and be transparent about data usage.
- Individuals’ personal data must be protected, respecting their right to privacy.
Intellectual Property Rights
- Unauthorized use of software, trade secrets, and digital content can lead to legal consequences.
- Organizations must comply with copyright and software licensing agreements.
- Ethically, respecting digital creations and intellectual property is vital for maintaining trust.
- Proper adherence to licenses and ensuring correct use of software is necessary for compliance.
Cybercrime and Legal Accountability
- Cybercrime, such as hacking and identity theft, is punishable by laws like the CFAA in the U.S.
- Organizations are legally obligated to report cybercrime incidents and assist law enforcement.
- Businesses can face legal consequences if they fail to secure systems, resulting in breaches.
- Ethically, transparency in reporting breaches and notifying users is crucial for maintaining trust.
Ethical Hacking and Responsible Disclosure
- Ethical hacking involves identifying system vulnerabilities with permission to improve security.
- Responsible disclosure means reporting vulnerabilities to companies before making them public.
- Ethically, hackers must avoid releasing vulnerabilities that could be exploited by malicious actors.
- Organizations should collaborate with ethical hackers to fix issues before they’re exploited.
Surveillance and Privacy
- Excessive surveillance without user consent may violate privacy laws like GDPR.
- Ethically, companies should disclose their surveillance practices and obtain user consent.
- Governments and organizations must balance security needs with respecting individual privacy rights.
- Surveillance must comply with legal frameworks to avoid infringing on personal privacy.
Cybersecurity Workforce Ethics
- Cybersecurity professionals must follow ethical guidelines that promote confidentiality and integrity.
- Insider threats, such as the misuse of privileged access, are a significant legal concern.
- Organizations should promote ethical behavior within cybersecurity teams to prevent conflicts of interest.
- Adhering to a strong ethical code of conduct ensures the responsible handling of sensitive information.
Legal Responsibilities in Incident Response
- Organizations have legal responsibilities to notify individuals and regulators of data breaches.
- Failure to comply with breach notification laws can result in significant legal penalties.
- Ethically, companies should prioritize transparency and communicate the full impact of incidents.
- Effective incident response plans must align with both legal requirements and ethical standards.
Artificial Intelligence (AI) and Ethical Use in Security
- AI raises concerns about privacy, bias, and decision-making in information security.
- Organizations must ensure AI is used in compliance with legal regulations on data privacy.
- Ethically, AI systems should be transparent, unbiased, and accountable for their decisions.
- AI in security should balance efficiency with respect for individual rights and fairness.
Emerging Trends and Future Challenges
The world of information security and cyber safety is constantly evolving. Some emerging trends include

Artificial Intelligence and Machine Learning in Security
- AI and machine learning (ML) are revolutionizing cybersecurity by enabling faster threat detection and response. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that signal potential security breaches.
- However, the growing reliance on AI introduces challenges, such as the risk of AI-driven attacks and the potential for bias in ML models.
- The ethical use of AI is also a concern, as AI systems must remain transparent and free from discriminatory practices.
- As AI evolves, organizations will need to balance the benefits of automation with the risks associated with its misuse.
Quantum Computing and Encryption
- Quantum computing holds the potential to break current encryption standards, posing a major future challenge to information security. While still in its early stages, quantum computing could render traditional encryption methods obsolete.
- To counter this, researchers are developing quantum-resistant encryption algorithms, but these are not yet widely adopted.
- The future of cybersecurity will depend on the rapid development of new encryption standards that can withstand the power of quantum computers.
- Organizations need to start preparing for a post-quantum world by investing in research and adopting forward-looking encryption solutions.
Cloud Security
- As more businesses move to the cloud, securing cloud environments has become a critical concern. The flexibility and scalability of cloud services bring new vulnerabilities, including data breaches, insecure APIs, and misconfigurations.
- Ensuring the protection of sensitive data in shared and multi-tenant environments is a challenge for organizations.
- Trends like Zero Trust architecture, which requires continuous verification of access, are gaining traction to improve cloud security.
- Companies must work closely with cloud providers to ensure robust security measures, such as encryption and multi-factor authentication, are in place.
Internet of Things (IoT) Security
- The rapid proliferation of IoT devices presents significant security risks, as many of these devices lack strong security features. Vulnerabilities in smart home devices, industrial sensors, and healthcare equipment can be exploited to launch large-scale cyber-attacks.
- Ensuring the security of connected devices requires implementing strong authentication, encryption, and network segmentation.
- As the number of IoT devices continues to grow, the challenge of securing these devices and preventing unauthorized access will only intensify.
- Future solutions will need to focus on securing the entire IoT ecosystem, from device manufacturers to end users.
Ransomware and Cyber Extortion
- Ransomware attacks have surged in recent years, with cybercriminals increasingly targeting critical infrastructure and healthcare systems. The rise of ransomware-as-a-service (RaaS) has made it easier for even less skilled hackers to launch sophisticated attacks.
- Organizations must prioritize data backups, employee training, and ransomware-specific defenses to mitigate these threats.
- The challenge lies in combating the increasingly advanced encryption methods used by attackers and the growing demand for cryptocurrency in ransom payments.
- As ransomware attacks evolve, the need for advanced threat intelligence and incident response strategies will become more critical.
5G and Network Security
- The rollout of 5G networks is set to transform industries by enabling faster speeds, lower latency, and the connection of billions of devices. However, the increased bandwidth and device connectivity create new attack surfaces for cybercriminals.
- Securing 5G networks will require addressing vulnerabilities in both the network infrastructure and connected devices.
- The challenge will be to implement strong security protocols without compromising the performance and scalability of 5G networks.
- Organizations will need to focus on network segmentation, encryption, and ensuring secure software-defined networking (SDN) to safeguard against future 5G threats.
Privacy and Data Sovereignty
- The increasing amount of personal data being collected and processed has heightened concerns about privacy and data sovereignty. Countries are introducing stricter data protection laws, such as GDPR, which have global implications.
- Managing cross-border data transfers and ensuring compliance with multiple regulations is a growing challenge for global organizations.
- The trend toward decentralized data storage solutions, like blockchain, may provide new opportunities to enhance data privacy.
- In the future, organizations will need to invest in privacy-first strategies and technologies to navigate the complex regulatory landscape and protect user data.
Biometric Security
- Biometric authentication, such as fingerprint scanning, facial recognition, and iris scans, is increasingly being used to enhance security. While biometrics offer convenience, they also raise privacy concerns and potential vulnerabilities if biometric data is compromised.
- Protecting biometric data from theft or misuse is a growing challenge as more organizations adopt these technologies.
- Ethical considerations surrounding the use of biometrics for surveillance and user tracking will continue to spark debate.
- The future of biometric security will require stronger encryption, anonymization of biometric data, and clear guidelines for its ethical use.
Cybersecurity Skills Gap
- The cybersecurity industry faces a significant skills gap, with demand for skilled professionals far outstripping supply. As cyber threats continue to increase in complexity, the need for qualified cybersecurity experts becomes more critical.
- Organizations must invest in training and developing talent, as well as exploring automated solutions to fill the gap.
- The challenge is not only attracting and retaining skilled cybersecurity professionals but also ensuring they stay ahead of emerging threats.
- In the future, initiatives like cybersecurity education programs and certifications will play a key role in addressing the skills shortage.
Regulatory Compliance and Ethical Issues
- As cyber threats evolve, governments worldwide are enacting stricter regulations to enforce security measures. Staying compliant with various data protection laws, such as GDPR, CCPA, and HIPAA, is a major challenge for organizations.
- Ethical issues, such as the responsible use of AI and balancing security with privacy, are also gaining importance.
- Companies will need to focus on ethical decision-making and ensure that their cybersecurity practices align with legal and moral standards.
- The future of cybersecurity will involve navigating the increasingly complex regulatory landscape while addressing evolving ethical considerations.
Emerging trends and future challenges in information security will require organizations to adopt more advanced and proactive strategies. Staying ahead of technological changes, while addressing regulatory and ethical concerns, will be key to maintaining a secure and resilient digital environment.
FAQs
What is the CIA Triad in information security?
The CIA Triad stands for Confidentiality, Integrity, and Availability. It ensures data is protected from unauthorized access, remains accurate, and is available to authorized users when needed.
How can you protect personal data online?
Protect personal data by using strong, unique passwords, enabling two-factor authentication, avoiding phishing links, and keeping your devices and software up-to-date.
What is the role of encryption in data security?
Encryption encodes data so that only authorized users can read it. It protects sensitive information from being accessed or intercepted by unauthorized parties.
Why is employee training important in cybersecurity?
Employee training ensures staff can identify cyber threats, such as phishing, and follow best practices to protect organizational data from attacks and breaches.
What are some emerging trends in cybersecurity?
Emerging trends include using AI for threat detection, securing cloud environments, and protecting Internet of Things (IoT) devices from new vulnerabilities.
Conclusion
As the digital world continues to grow, information security and cyber safety are more crucial than ever. By following best practices for securing data, networks, and devices, individuals and organizations can reduce their vulnerability to cyberattacks. The key takeaway is to remain vigilant, keep systems updated, and stay informed about the latest security threats and solutions.
