1 Introduction
Definition of Information Forensics and Security
Information forensics and security are crucial fields in today’s digital world. Information forensics involves analyzing digital evidence to understand and respond to security breaches, while information security focuses on protecting data from unauthorized access or attacks. Both fields work together to safeguard sensitive information and ensure its integrity.
Importance of Data Protection in digital Age
In our increasingly connected world, data protection has become essential. With the rise of cyber threats, protecting personal and organizational data is critical to prevent financial losses, reputational damage, and legal issues. Effective data protection measures are crucial for maintaining trust and security in the digital landscape.
2 The Fundamentals of Information Forensics
Understanding Digital Evidence
Digital evidence includes any data stored or transmitted in digital form that can be used in investigations. This can range from emails and documents to log files and metadata. Understanding how to collect and analyze digital evidence is fundamental in uncovering the truth behind security incidents.
Key Principles of Forensics and Security
Information forensics is based on principles like preserving evidence integrity, maintaining a chain of custody, and using validated techniques for analysis. Security principles include confidentiality, integrity, and availability, ensuring that data is protected from unauthorized access, alteration, and loss.
3 Information Security Threats
Common information security threats
Information security threats are risks that can compromise the confidentiality, integrity, and availability of data. Here are some common threats:
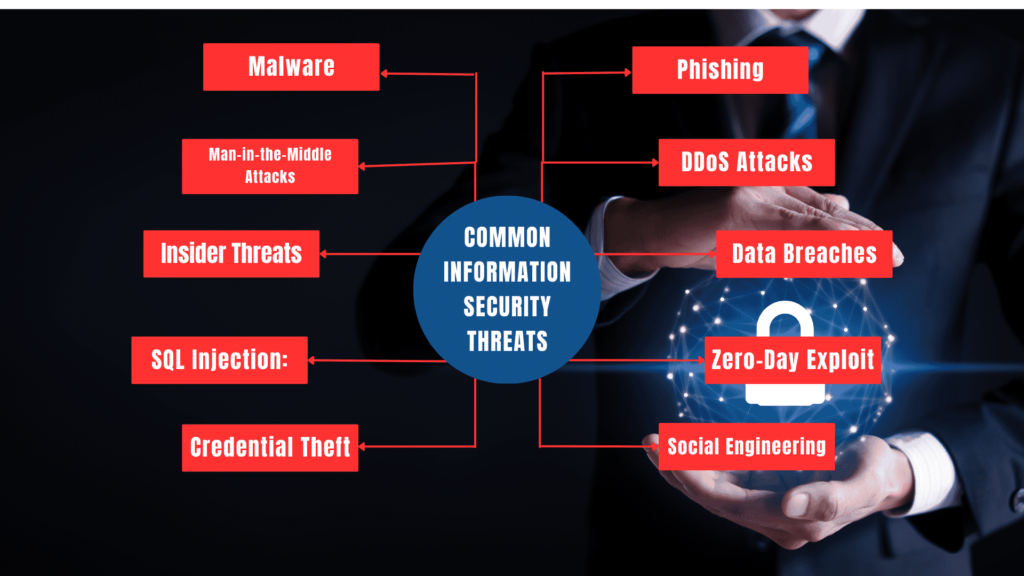
- Malware: Malicious software, including viruses, worms, ransomware, and spyware, designed to damage or exploit systems and data.
- Phishing: Deceptive attempts to acquire sensitive information, often through email or fake websites, by masquerading as a trustworthy entity.
- Man-in-the-Middle Attacks: Intercepting and altering communications between two parties without their knowledge, often to steal information or inject malicious content.
- DDoS Attacks: Distributed Denial of Service attacks overwhelm a system or network with excessive traffic, causing it to become slow or unavailable.
- Insider Threats: Risks posed by individuals within the organization, such as employees or contractors, who misuse or mishandle sensitive information.
- Data Breaches: Unauthorized access or acquisition of sensitive data, often leading to data loss or exposure.
- SQL Injection: Exploiting vulnerabilities in a web application’s database query handling to execute malicious SQL commands.
- Zero-Day Exploits: Attacks targeting vulnerabilities that are unknown to the software vendor or security community, leaving systems unprotected until a fix is released.
- Credential Theft: Stealing or guessing user credentials to gain unauthorized access to systems or data.
- Social Engineering: Social engineering manipulates individuals into revealing confidential information or compromising security. It exploits human emotions, trust, or lack of awareness. Unlike technical hacks, it targets people, making it difficult to defend against.
Emerging Threats in the Cybersecurity Landscape
Emerging threats in the cybersecurity landscape are constantly evolving as technology advances and attackers become more sophisticated. Here are some key emerging threats:

- Advanced Persistent Threats (APTs): These are long-term, targeted attacks where adversaries maintain a presence within a network to steal data or disrupt operations. They often involve sophisticated tactics and are hard to detect.
- Ransomware-as-a-Service (RaaS): This model allows cybercriminals to deploy ransomware without needing technical expertise. It lowers the barrier to entry for attacks and enables widespread ransomware campaigns.
- AI-Powered Attacks: The use of artificial intelligence and machine learning by attackers to automate and enhance their strategies, such as creating realistic phishing emails or discovering vulnerabilities faster.
- Deep fake Technology: Creating hyper-realistic fake videos or audio recordings used for social engineering attacks, fraud, or misinformation campaigns.
- IoT Vulnerabilities: As the number of Internet of Things (IoT) devices increases, so do the risks associated with their often inadequate security, leading to potential exploits and botnet creation.
- Supply Chain Attacks: Targeting vulnerabilities in the supply chain, where attackers compromise software or hardware used by multiple organizations to gain access to their systems.
- 5G Network Risks: The rollout of 5G networks introduces new vulnerabilities, such as the potential for increased attack surfaces and challenges in securing the expanded network infrastructure.
- Quantum Computing Threats: The potential future capability of quantum computers to break traditional encryption methods, posing a risk to data confidentiality and integrity.
- Cloud Security Issues: As organizations increasingly migrate to the cloud, new risks emerge related to data security, misconfigured cloud services, and shared responsibility models.
- Synthetic Identity Fraud: Creating fake identities using a combination of real and fake information to commit fraud or bypass security systems.
These emerging threats highlight the need for continuous adaptation and improvement in cybersecurity practices and technologies.
4 Challenges and Trends in Information Security and Forensics
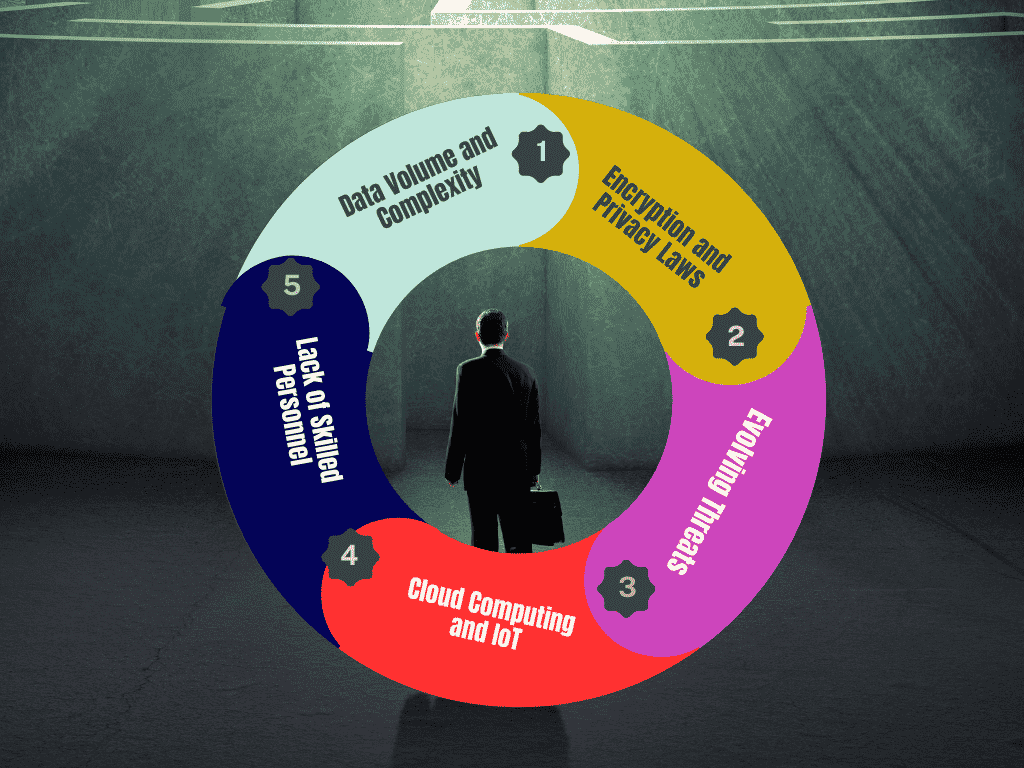
- Data Volume and Complexity: The vast amount of data generated daily presents a challenge in terms of storage, processing, and analysis. Forensic investigators must sift through enormous datasets to locate relevant evidence, which can be time-consuming and resource intensive.
2.Encrypti on and Privacy Laws: While encryption protects data from unauthorized access, it also poses a challenge for forensic investigators when attempting to access information needed for an investigation. Furthermore, navigating complex privacy laws can restrict access to critical data during forensic analysis.
- Evolving Threats: Cyber threats such as ransomware, advanced persistent threats (APTs), and social engineering are becoming more sophisticated, making it difficult for security measures to keep pace. Forensic professionals must stay ahead of these evolving threats to effectively respond to breaches.
- Cloud Computing and IoT: The rise of cloud storage and the Internet of Things (IoT) introduces new challenges. Forensics experts must deal with distributed systems, multiple data sources, and devices with limited security measures, complicating evidence collection and preservation.
- Lack of Skilled Personnel: There is a shortage of trained professionals with expertise in both cybersecurity and digital forensics, making it challenging for organizations to respond effectively to security incidents and perform forensic investigations.
Trends in Information Security and Forensics
- Artificial Intelligence and Machine Learning: AI and machine learning are being integrated into cybersecurity and forensic tools to automate threat detection, improve response times, and assist in the identification of patterns within large datasets, making investigations more efficient.
- Blockchain for Data Integrity: Blockchain technology is being explored for its potential to maintain data integrity in forensic investigations. It provides a transparent and immutable record of digital evidence, ensuring the authenticity and tamper-proof nature of forensic data.
- Zero Trust Security Models: The shift towards zero trust architecture is gaining traction. This model assumes that threats could come from both external and internal sources, leading to more stringent verification of users and devices before granting access to resources.
- Cloud Forensics: As organizations increasingly adopt cloud services, cloud forensics is becoming a critical area. It involves developing tools and techniques to collect, analyze, and preserve data from cloud environments while addressing issues like multi-jurisdictional data storage and access controls.
5 The Role of Encryption in Data Protection
Encryption plays a vital role in data protection by ensuring that sensitive information is secured and remains confidential, even if unauthorized parties gain access to it. Here’s how encryption contributes to data protection
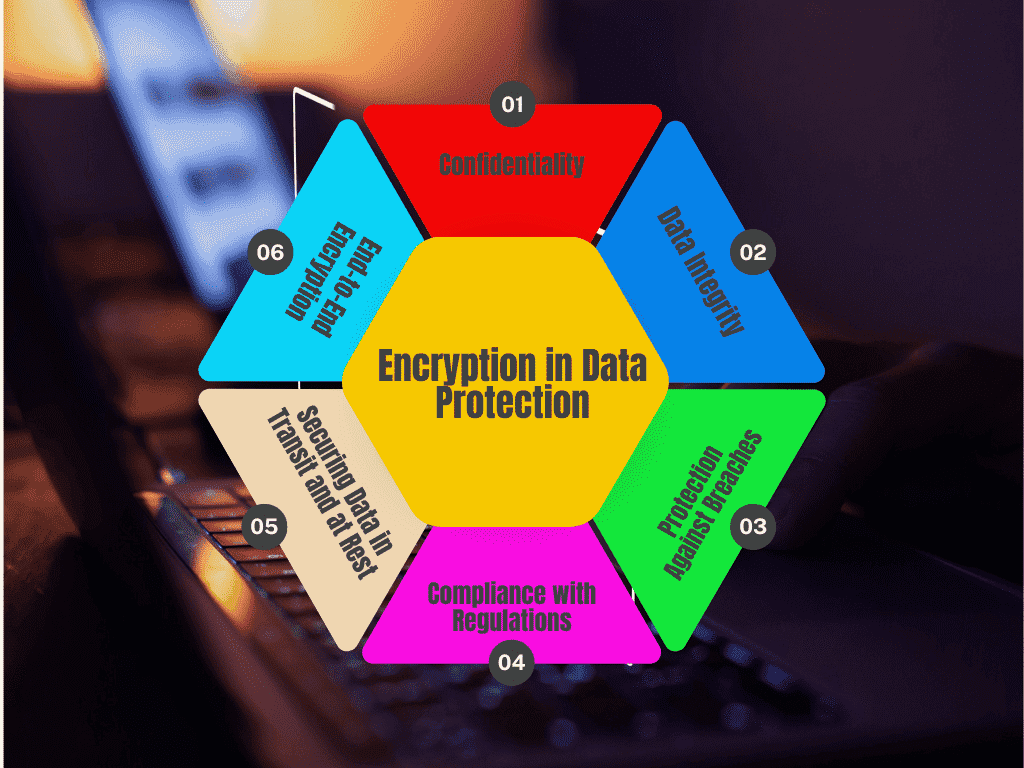
1 Confidentiality: Encryption transforms data into unreadable ciphertext, ensuring that only authorized users with the decryption key can access the original information. This helps protect sensitive data such as financial records, personal information, and intellectual property from unauthorized access.
2 Data Integrity: Encryption ensures that the data has not been tampered with or altered during transmission or storage. Hashing algorithms used alongside encryption provide checksums that verify data integrity, ensuring that any changes can be detected.
3 Protection Against Breaches: Even if attackers gain access to encrypted data, they cannot easily exploit it without the corresponding decryption key, reducing the risk of data breaches leading to identity theft or financial loss.
4 Compliance with Regulations: Many data protection regulations, such as GDPR and HIPAA, mandate the use of encryption to safeguard personal and sensitive data. Encryption helps organizations meet compliance requirements and avoid penalties for data exposure.
5 Securing Data in Transit and at Rest: Encryption protects data whether it is being transmitted over networks (in transit) or stored on servers, devices, or cloud environments (at rest). This ensures that sensitive data always remains protected, regardless of its location.
6 End-to-end Encryption: In communication systems, end-to-end encryption ensures that only the communicating parties can read the messages, protecting them from interception by third parties, including service providers.
6 Information Forensics and Legal Aspects
Information Forensics
Digital Evidence Collection: Information forensics involves gathering digital evidence from various sources, such as computers, mobile devices, and networks, to understand the details of a security incident.
Evidence Preservation: Properly preserving digital evidence is crucial to maintain its integrity and prevent alteration or loss during the investigation.
Data Analysis: Analyzing collected data helps identify the nature of the attack, the vulnerabilities exploited, and the impact on the organization.
Legal Aspects
Compliance with Regulations: Forensic investigations must comply with data protection laws and privacy regulations to ensure that evidence handling is lawful, and that individuals’ rights are respected.
Adherence to Legal Standards: Investigators must follow strict legal procedures to ensure that evidence is admissible in court, which includes documenting the chain of custody and using approved forensic tools.
Jurisdictional Considerations: Legal aspects also involve understanding jurisdictional boundaries, especially in cases where data crosses national borders or involves multiple legal systems.
Due Process: Ensuring that all investigative procedures respect the rights of individuals and organizations involved is essential to maintain fairness and legality in the investigation process.
Expert Testimony: Forensic experts may be required to provide testimony in court regarding their findings and the methods used in their investigation, making it important for them to be able to clearly explain complex technical details in a way that is understandable to legal professionals.
The intersection of information forensics and legal considerations ensures that cybercrime investigations are conducted properly and that any evidence collected is reliable and actionable in legal proceedings.
7 Techniques in Information Forensics
Network Forensics
Network forensics focuses on analyzing network traffic and data to detect and investigate cyber incidents. Key techniques include:
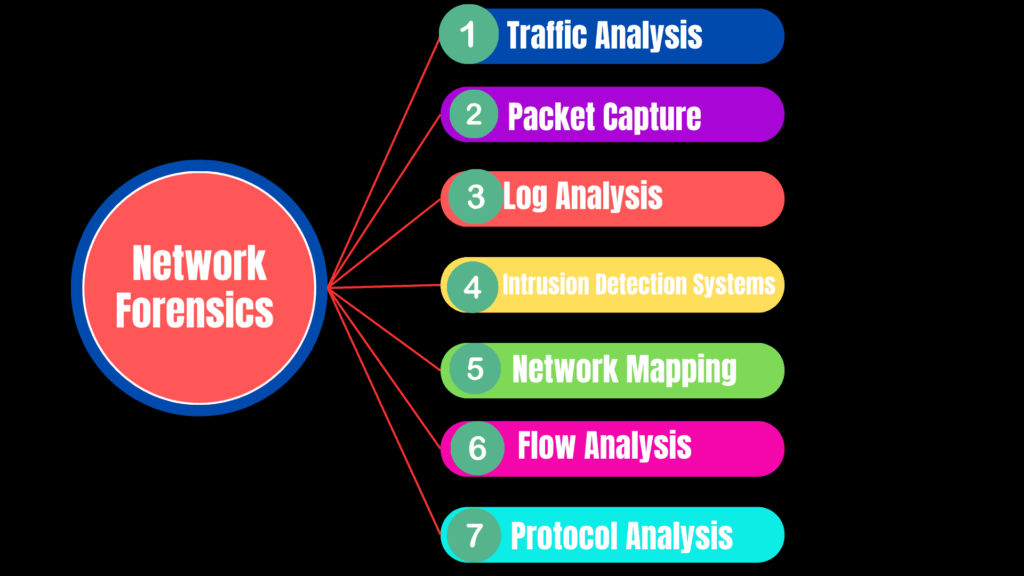
- Traffic Analysis: Monitoring network traffic helps identify anomalies and suspicious patterns, revealing potential security breaches.
- Packet Capture: Tools like Wireshark capture and analyze network packets to uncover malicious activities or unauthorized data transfers.
- Log Analysis: Reviewing logs from network devices such as routers and firewalls helps track user actions and detect network intrusions.
- Intrusion Detection Systems (IDS): IDS tools monitor and alert suspicious network activities, helping to identify and respond to threats in real time.
- Network Mapping: Creating a network topology map aids in understanding the network structure and identifying vulnerabilities.
- Flow Analysis: Analyzing flow data, such as Net Flow, tracks traffic patterns and detects anomalies that might indicate a security issue.
- Protocol Analysis: Examining network protocols ensures that communications are secure and helps identify vulnerabilities that could be exploited by attackers. Forensics
Mobile Forensics
Mobile forensics involves extracting and analyzing data from mobile devices to investigate incidents. Key techniques include:
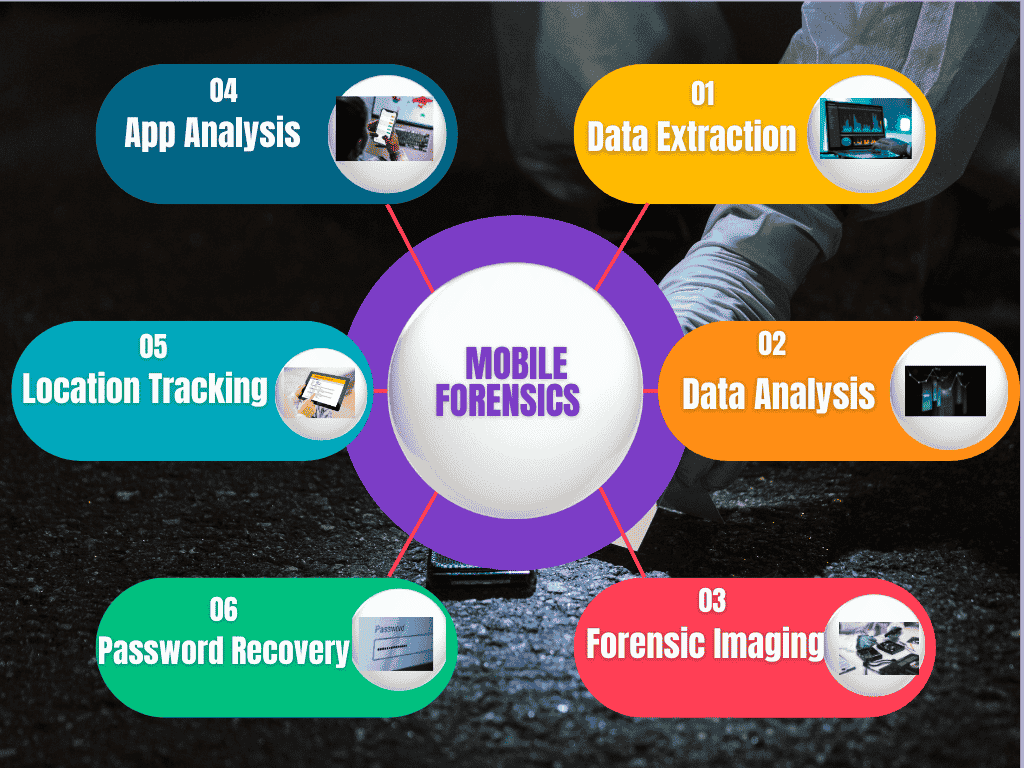
- Data Extraction: Techniques like logical, physical, and file system extraction retrieve data from mobile devices. This includes messages, calls, and other data.
- Data Analysis: Analyzing extracted data helps reconstruct user activities and identify evidence related to the incident.
- Forensic Imaging: Creating a bit-for-bit copy of the mobile device’s storage preserves the original data for analysis, preventing data alteration.
- App Analysis: Examining data from installed applications, including social media and messaging apps, provides insights into user interactions and behavior.
- Location Tracking: Analyzing location data from GPS or network connections helps track the device’s movements and locations of interest.
- Password Recovery: Techniques for bypassing or recovering device passwords enable access to locked devices for further investigation.
Disk Forensics
Disk forensics involves analyzing hard drives and other storage devices to uncover digital evidence. Key techniques include:
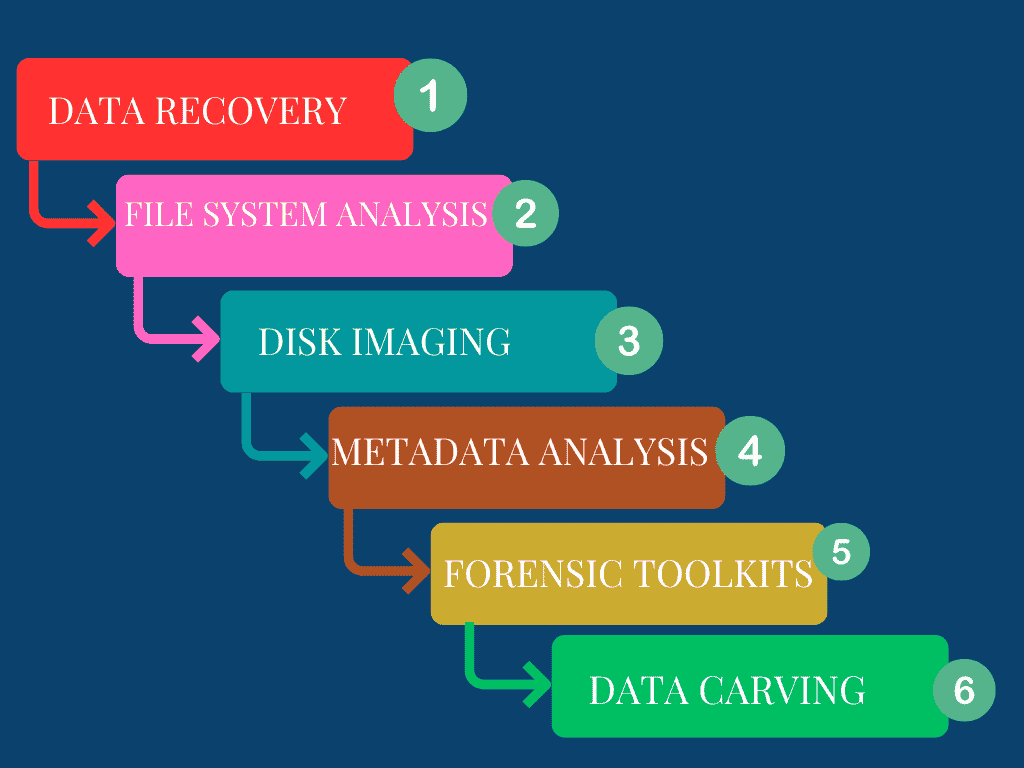
- Data Recovery: Retrieving deleted or damaged files from storage devices using specialized tools to recover crucial evidence.
- File System Analysis: Examining the file system to trace data access, modifications, and deletions, helping to reconstruct timelines of events.
- Disk Imaging: Creating an exact copy of the storage device’s contents ensures that the original data remains unaltered, allowing for thorough analysis.
- Metadata Analysis: Reviewing metadata associated with files, such as creation and modification dates, provides context and history of file activities.
- Forensic Toolkits: Utilizing forensic toolkits and software to analyze disk contents, search for specific data, and uncover hidden or encrypted files.
- Data Carving: Extracting files and data fragments from unallocated space on the disk, useful for recovering files that have been deleted but not overwritten.
These techniques in network, mobile, and disk forensics are essential for investigating and solving cyber incidents, providing valuable insights and evidence to support legal and security efforts,
8 Incident Response and Recovery
Incident response and recovery are critical components of a robust cybersecurity strategy, designed to manage and mitigate the impact of security incidents. Incident response involves the steps taken to address and manage a security breach or attack.
It starts with detection and identification, where the security team monitors for signs of suspicious activity or breaches using various tools and techniques. Once an incident is identified, the focus shifts to containment, which aims to limit the spread of the attack and prevent further damage. This is followed by eradication, where the root cause of the incident is addressed, and malicious elements are removed from the environment.
Finally, recovery involves restoring affected systems and services to normal operation, ensuring that they are free of threats and vulnerabilities. The recovery phase also includes post-incident analysis, which involves reviewing the incident to understand what happened, evaluating the response effectiveness, and identifying areas for improvement. This analysis helps to refine incident response plans, enhance security measures, and better prepare for future incidents.
9 Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a crucial strategy designed to protect sensitive information and prevent data breaches. DLP solutions focus on identifying, monitoring, and securing data to ensure it is not lost, misused, or accessed by unauthorized individuals.
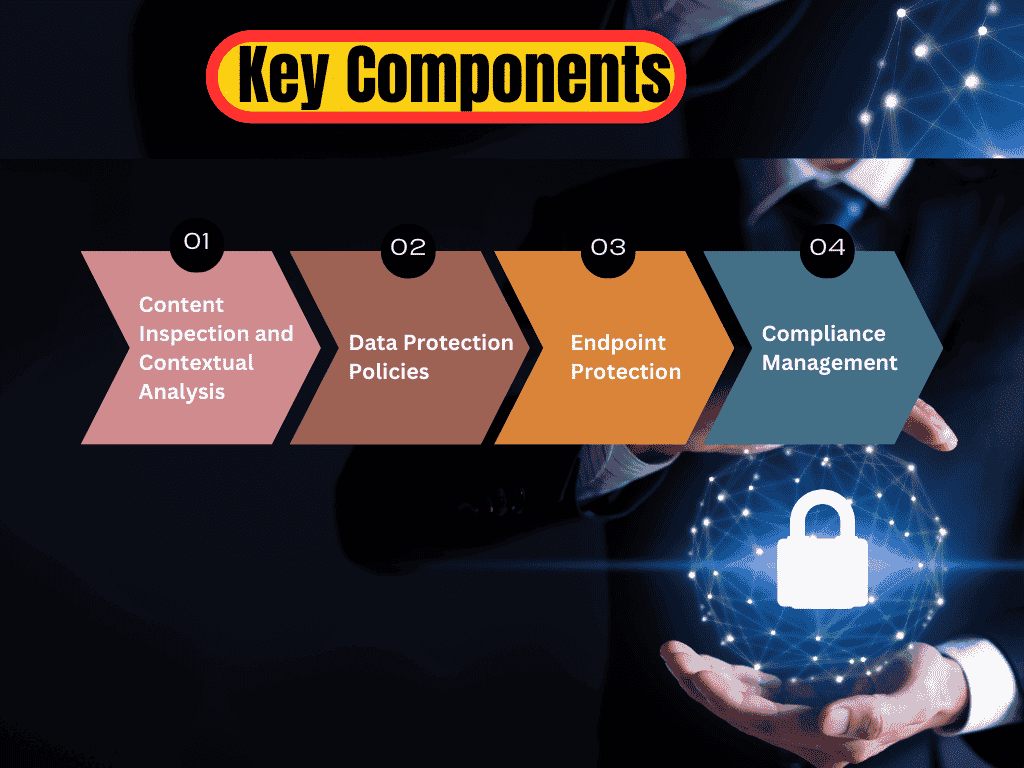
Key Components
Content Inspection and Contextual Analysis: DLP technologies use content inspection and contextual analysis to detect sensitive data within files, emails, and other data sources. They identify data based on predefined policies and rules, such as personally identifiable information (PII) and financial records.
Data Protection Policies: Once sensitive data is identified, DLP solutions enforce protection policies by blocking unauthorized access, encrypting data, or alerting administrators to potential breaches.
Endpoint Protection: DLP solutions also include endpoint protection, which secures data on user devices. They monitor and control data transfers to external storage devices or cloud services, ensuring that sensitive information remains protected.
Compliance Management: DLP helps organizations adhere to regulatory requirements like GDPR, HIPAA, and PCI-DSS. It enforces data protection policies and generates compliance reports to ensure legal and regulatory standards are met.
10 Best Practices in Information Security
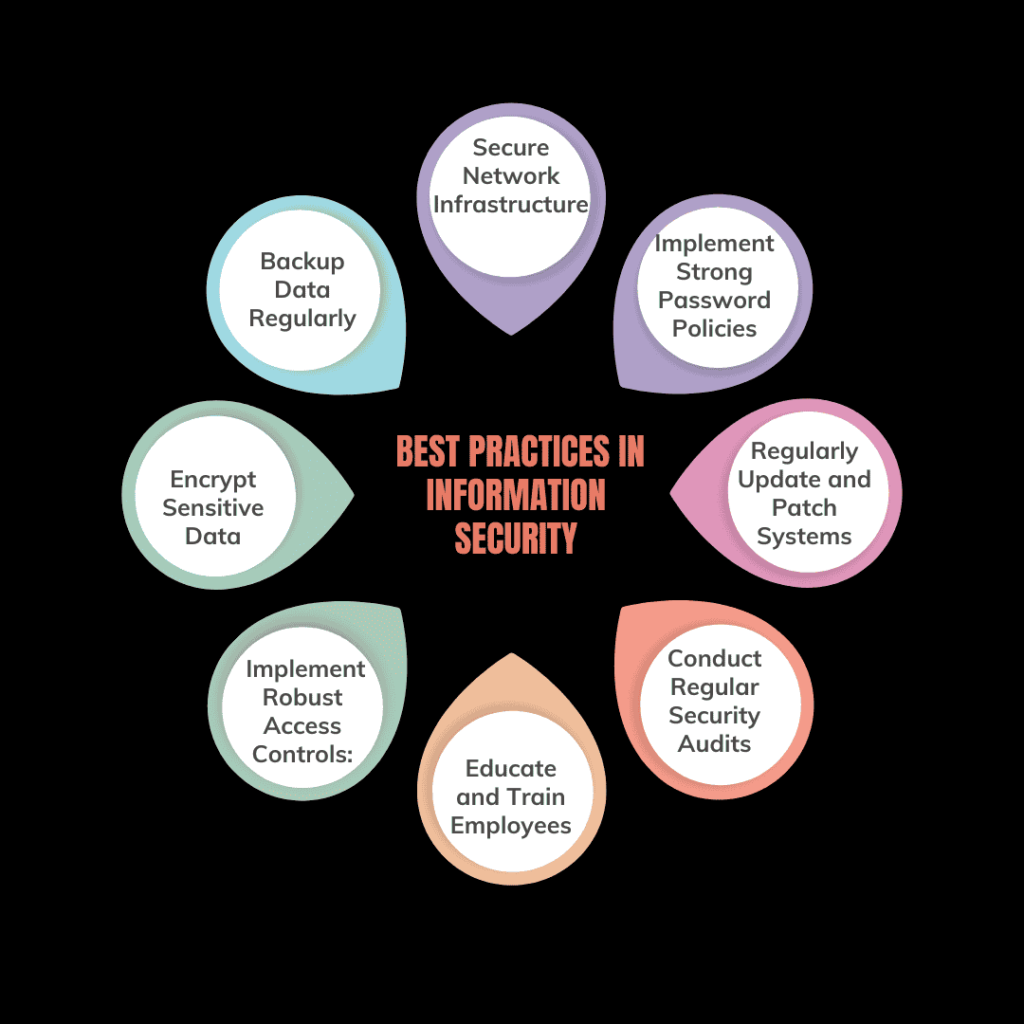
- Implement Strong Password Policies: Enforce the use of complex, unique passwords for all user accounts and systems. Promote the adoption of multi-factor authentication (MFA) to strengthen security with an extra protective layer. Regularly update passwords and avoid using the same password across multiple sites.
- Regularly Update and Patch Systems: Keep all software, including operating systems, applications, and firmware, up to date with the latest patches and updates. This helps protect against known vulnerabilities and exploits that could be used by attackers.
- Conduct Regular Security Audits: Perform regular security audits and vulnerability assessments to identify and address potential weaknesses in your systems. This includes penetration testing, security reviews, and risk assessments to ensure that your security measures are effective.
- Educate and Train Employees: Provide ongoing security training and awareness programs for employees to recognize and respond to potential threats, such as phishing attacks and social engineering. Ensure that staff understand the importance of information security and follow best practices.
- Implement Robust Access Controls: Use role-based access controls (RBAC) to ensure that employees only have access to the information and systems necessary for their roles. Regularly review and update access permissions to reflect changes in employee roles and responsibilities.
- Encrypt Sensitive Data: Protect sensitive data both at rest and in transit by using encryption. This guarantees that even if unauthorized individuals intercept or access the data, it stays encrypted and secure.
- Backup Data Regularly: Implement regular data backups and ensure that backup copies are stored securely. Test backup and recovery processes to confirm that data can be restored quickly and accurately in case of data loss or system failure.
8 Secure Network Infrastructure: Use firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to protect your network from unauthorized access and attacks. Ensure that network devices are properly configured and regularly reviewed for security.
11 Future Trends in Information Forensics and Security

- Advanced AI and Machine Learning Integration : The integration of AI and machine learning in information forensics and security will become increasingly sophisticated. Future advancements will enable more accurate threat detection, automated analysis of large datasets, and predictive capabilities that anticipate potential security breaches before they occur. AI-driven tools will enhance forensic investigations by providing deeper insights and more efficient processing of evidence.
- Quantum Computing Impact: Quantum computing holds the potential to revolutionize information security and forensics by drastically increasing computing power. While this could accelerate data processing and encryption, it also poses challenges, as quantum computers could potentially break current encryption methods. Research into quantum-resistant encryption algorithms and security measures will be crucial to address these emerging risks.
- Blockchain for Data Integrity: Blockchain technology will play a significant role in ensuring data integrity and transparency in forensics. By using blockchain to record and verify digital evidence, organizations can create immutable records that are resistant to tampering and fraud. This will enhance the reliability of forensic investigations and the trustworthiness of digital evidence.
- Increased Use of Cloud Forensics: With the growing adoption of cloud services, cloud forensics will become a critical area of focus. Future trends will involve developing advanced techniques for investigating cloud-based incidents, including challenges related to data jurisdiction, multi-tenancy, and virtualization. Ensuring effective cloud forensics will require specialized tools and approaches tailored to cloud environments.
5 Proactive Threat Hunting: Proactive threat hunting will gain prominence as organizations shift from reactive to proactive security measures. Future trends will emphasize the importance of continuous monitoring and active searching for threats before they cause significant damage. This approach will involve using advanced analytics and threat intelligence to identify and mitigate potential risks early.
- IoT Security Challenges: The proliferation of Internet of Things (IoT) devices will introduce new security challenges, including vulnerabilities and data privacy concerns. Future trends will focus on enhancing security measures for IoT devices, developing standardized protocols, and implementing robust forensic techniques to address incidents involving interconnected devices.
12 Information Security in Various Sectors
Healthcare Data Protection: In healthcare, protecting patient data is crucial for privacy and meeting legal requirements like HIPAA. This involves using encryption to secure data both during transfer and when stored. Access controls ensure only authorized staff can view or change patient information. Secure storage solutions help prevent unauthorized access and data breaches.
Financial Sector Security: For the financial sector, safeguarding sensitive data is essential to prevent fraud and maintain trust. This includes using fraud detection systems to spot suspicious activity and secure transaction methods to protect financial exchanges. Data encryption keeps financial information safe from cyber threats. Regular security checks help identify and fix potential issues.
Government Data Protection: Government agencies need to protect sensitive information related to national security and public services. They use strict access controls to ensure only authorized people can access this data. Encryption is employed to keep information secure and private. Regular security audits are conducted to find and address any vulnerabilities.
Retail Sector Security: In retail, protecting customer information is vital for preventing data breaches and maintaining customer trust. Secure payment systems protect transaction details, while data encryption safeguards personal information. Following PCI-DSS standards helps ensure robust security practices. Regular updates and security checks address potential vulnerabilities.
Education Sector Security: In education, safeguarding student and faculty data is important for privacy and compliance with regulations like FERPA. Access controls limit data access to authorized individuals, while encryption protects sensitive information from unauthorized access. Compliance with legal standards ensures proper data handling. Regular security reviews help maintain data security.
13 FAQs
What is information forensics?
Information forensics involves analyzing digital evidence to uncover and understand security breaches. It focuses on preserving evidence integrity and determining how incidents occurred. This process helps in responding effectively and preventing future breaches.
What makes data protection essential in today’s digital era?
Data protection is vital to avoid financial loss, reputational damage, and legal issues from cyber threats. Safeguarding data ensures confidentiality, integrity, and availability, maintaining trust in digital interactions and systems. Effective protection measures are essential for secure operations.
What are common cybersecurity threats?
Frequent threats consist of malware, phishing schemes, ransomware, and denial-of-service attacks. These threats can compromise systems, steal data, or disrupt operations. Understanding these threats helps in developing strategies to defend against them effectively.
What is the role of network forensics?
Network forensics involves analyzing network traffic and logs to detect and investigate cyber incidents. It helps in understanding the scope of breaches, identifying affected systems, and tracing the origin of attacks.
How does data loss prevention (DLP) work?
Data Loss Prevention (DLP) involves using strategies and tools to monitor and control data flows, preventing unauthorized access, transfer, or loss of sensitive information. DLP solutions help enforce policies and protect data from breaches and leaks.
15 Conclusion
In conclusion, improving data protection requires a comprehensive approach that combines information forensics, strong security practices, and awareness of new trends. Information forensics is essential for understanding and investigating security breaches, while effective security measures prevent unauthorized access and reduce risks. Staying updated on evolving threats and technologies like AI and blockchain is crucial for maintaining robust protection. By implementing thorough data protection strategies, organizations can keep sensitive information secure against cyber threats. Regularly updating security measures, educating employees, and adopting advanced technologies help safeguard data and manage incidents effectively. As technology advances, vigilance and adaptability in forensics and security are key to defending against new cyber threats.
